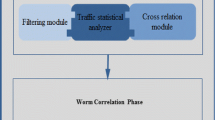
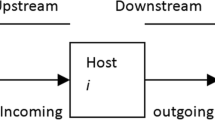
Abstract
During the last few years, the number of Internet worms and viruses has significantly increased. For the fast detection of Internet worms/viruses, the signature-based scheme with TCAM is necessary for the network intrusion detection system (NIDS). However, due to the limit of the TCAM size, all the signatures of Internet worms/viruses cannot be stored. Hence, we propose a two-phase content inspection algorithm which can support a large number of long signatures at TCAM. From the simulation results, it is shown that our algorithm for TCAM provides a fast virus-detection capability at line rate of 10Gbps (OC192).
This research was supported in part by ITRC program of the Ministry of Information and Communication, Korea.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Snort, http://www.snort.org/
Clam Antivirus, http://www.clamav.net/
Liu, H.: Routing Table Compaction in Ternary CAM. IEEE Micro. (2002)
Ravikumar, V.C., Mahapatra, R.N.: TCAM Architecture for IP Lookup Using Prefix Properties. IEEE Micro. (2004)
IDT, Network Search Engine (NSE) with QDRTM Interface, http://www1.idt.com/pcms/tempDocs/75K6213452134_DS_80635.pdf
Sung, J.S., Kang, S.M., Lee, Y.S., Kwon, T.G., Kim, B.T.: A Multi-gigabit Rate Deep Packet Inspection Algorithm using TCAM. IEEE Globecom (2005) (to appear)
Yu, F., Kats, R.H., Lakshman, T.V.: Gigabit Rate Packet Pattern-Matching Using TCAM. In: IEEE International Conference on Network Protocols (2004)
Naik, U.R., Chandra, P.R.: Designing High-Performance Networking Applications, p. 472. Intel Press (2004)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Song, IS., Lee, Y., Kwon, TG. (2005). A Multi-gigabit Virus Detection Algorithm Using Ternary CAM. In: Hao, Y., et al. Computational Intelligence and Security. CIS 2005. Lecture Notes in Computer Science(), vol 3802. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11596981_33
Download citation
DOI: https://doi.org/10.1007/11596981_33
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-30819-5
Online ISBN: 978-3-540-31598-8
eBook Packages: Computer ScienceComputer Science (R0)