Abstract
We consider a strategic game with two classes of confronting randomized players on a graph G(V, E): ν attackers, each choosing vertices and wishing to minimize the probability of being caught, and a defender, who chooses edges and gains the expected number of attackers it catches. The Price of Defense is the worst-case ratio, over all Nash equilibria, of the optimal gain of the defender over its gain at a Nash equilibrium. We provide a comprehensive collection of trade-offs between the Price of Defense and the computational efficiency of Nash equilibria.
– Through reduction to a Two-Players, Constant-Sum Game, we prove that a Nash equilibrium can be computed in polynomial time. The reduction does not provide any apparent guarantees on the Price of Defense.
– To obtain such, we analyze several structured Nash equilibria:
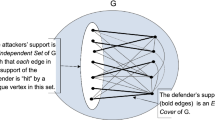
– In a Matching Nash equilibrium, the support of the defender is an Edge Cover. We prove that they can be computed in polynomial time, and they incur a Price of Defense of α(G), the Independence Number of G.
– In a Perfect Matching Nash equilibrium, the support of the defender is a Perfect Matching. We prove that they can be computed in polynomial time, and they incur a Price of Defense of \(\frac{|V|}{2}\).
– In a Defender Uniform Nash equilibrium, the defender chooses uniformly each edge in its support. We prove that they incur a Price of Defense falling between those for Matching and Perfect Matching Nash Equilibria; however, it is \({\cal NP}\)-complete to decide their existence.
– In an Attacker Symmetric and Uniform Nash equilibrium, all attackers have a common support on which each uses a uniform distribution. We prove that they can be computed in polynomial time and incur a Price of Defense of either \(\frac{|V|}{2}\) or α(G).
This work was partially supported by the IST Program of the European Union under contract number IST-2004-001907 (DELIS).
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Bonifaci, V., Di Iorio, U., Laura, L.: On the complexity of uniformly mixed nash equilibria and related regular subgraph problems. In: Liśkiewicz, M., Reischuk, R. (eds.) FCT 2005. LNCS, vol. 3623, pp. 197–208. Springer, Heidelberg (2005)
Bonifaci, V., Di Iorio, U., Laura, L.: New results on the complexity of uniformly mixed nash equilibria. In: Deng, X., Ye, Y. (eds.) WINE 2005. LNCS, vol. 3828, pp. 1023–1032. Springer, Heidelberg (2005)
Cheswick, E.R., Bellovin, S.M.: Firewalls and Internet Security. Addison-Wesley, Reading (1994)
Garey, M.R., Johnson, D.S.: Computers and Intractability: A Guide to the Theory of NP-Completeness. W. H. Freeman & Co., New York (1979)
Gelastou, M., Mavronicolas, M., Papadopoulou, V., Philippou, A., Spirakis, P.: The Power of the Defender. In: Proceedings of the 2nd International Workshop on Incentive-Based Computing (2006) (to appear)
Goldberg, A.V., Karzanov, A.V.: Maximum Skew-Symmetric Flows. In: Spirakis, P.G. (ed.) ESA 1995. LNCS, vol. 979, pp. 155–170. Springer, Heidelberg (1995)
Koutsoupias, E., Papadimitriou, C.: Worst-case equilibria. In: Meinel, C., Tison, S. (eds.) STACS 1999. LNCS, vol. 1563, pp. 404–413. Springer, Heidelberg (1999)
Markham, T., Payne, C.: Security at the Network Edge: A Distributed Firewall Architecture. In: Proceedings of the 2nd DARPA Information Survivability Conference and Exposition, vol. 1, pp. 279–286 (2001)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: A Network Game with Attacker and Protector Entities. In: Deng, X., Du, D.-Z. (eds.) ISAAC 2005. LNCS, vol. 3827, pp. 288–297. Springer, Heidelberg (2005)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: A Graph-Theoretic Network Security Game. In: Deng, X., Ye, Y. (eds.) WINE 2005. LNCS, vol. 3828, pp. 969–978. Springer, Heidelberg (2005)
Nash, J.F.: Equilibrium Points in N-Person Games. Proceedings of National Acanemy of Sciences of the United States of America 36, 48–49 (1950)
Nash, J.F.: Non-Cooperative Games. Annals of Mathematics 54(2), 286–295 (1951)
von Neumann, J.: Zur Theorie der Gesellschaftsspiele. Mathematische Annalen 100, 295–320 (1928)
Valiant, L.G.: The Complexity of Computing the Permanent. Theoretical Computer Science 8(2), 189–201 (1979)
West, D.B.: Introduction to Graph Theory, 2nd edn. Prentice Hall, Englewood Cliffs (2001)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2006 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Mavronicolas, M., Michael, L., Papadopoulou, V., Philippou, A., Spirakis, P. (2006). The Price of Defense. In: Královič, R., Urzyczyn, P. (eds) Mathematical Foundations of Computer Science 2006. MFCS 2006. Lecture Notes in Computer Science, vol 4162. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11821069_62
Download citation
DOI: https://doi.org/10.1007/11821069_62
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-37791-7
Online ISBN: 978-3-540-37793-1
eBook Packages: Computer ScienceComputer Science (R0)