Abstract
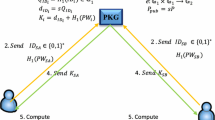
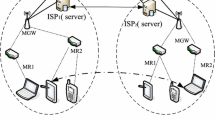
In this paper we propose a new efficient authentication protocol that reduces a burden of computation for digital signature generation/verification on mobile devices in the personal area network. In particular, we focus on eliminating the traditional public key operations on mobile devices without any assistance of a signature server. Moreover, the proposed protocol provides a simplified procedure for certificate status management to alleviate communication and computational costs on mobile devices in the personal area network.
This work was supported by grant No. R01-2006-000-10260-0 from the Basic Research Program of the Korea Science & Engineering Foundation.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Bicakci, K., Baykal, N.: Server assisted signature revisited. Topics in Cryptology - CT-RSA 2003, pp. 143–156 (March 2003)
Ding, X., Mazzocchi, D., Tsudik, G.: Experimenting with Server-Aided Signatures. In: 2002 Network and Distributed Systems Security Symposium (NDSS 2002) (February 2002)
Gehrmann, C., Nyberg, K., Mitchell, C.: The personal CA - PKI for a Personal Area Network. In: Proceedings - IST Mobile & Wireless Communications Summit 2002 (June 2002)
Housley, R., Ford, W., Polk, W., Solo, D.: Internet X.509 public key infrastructure certificate and CRL profile, RFC 2459 (January 1999)
Jakobsson, M., Leighton, F., Micali, S., Szydlo, M.: Fractal Merkle Tree Representation and Traversal. In: Joye, M. (ed.) CT-RSA 2003. LNCS, vol. 2612, pp. 314–326. Springer, Heidelberg (2003)
Merkle, R.C.: A digital signatures based on a conventional encryption function. In: Pomerance, C. (ed.) CRYPTO 1987. LNCS, vol. 293, pp. 369–378. Springer, Heidelberg (1988)
Merkle, R.C.: A certified digital signature. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 218–238. Springer, Heidelberg (1990)
Naor, D., Shenhav, A., Wool, A.: One-Time Signature Revisited: Have They Become Practical? Cryptology ePrint Archive, Report 2005/442 (2005)
Naor, M., Nissim, K.: Certificate revocation and certificate update. In: The 7th USENIX Security Symposium (January 1998)
Myers, M., Ankney, R., Malpani, A., Galperin, S., Adams, C.: X.509 Internet public key infrastructure on-line certificate status protocol (OCSP), RFC 2560 (June 1999)
Stajano, F., Anderson, R.: The resurrecting duckling: security issues for ad-hoc wireless networks. In: The 7th International Workshop on Security Protocols, pp. 172–194 (1999)
Zhou, J., Fao, F., Deng, R.: An Efficient Public-Key Framework. In: The 5th International Conference on Information and Communications Security, October 2003, pp. 88–99 (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2006 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Sur, C., Yang, JP., Rhee, K.H. (2006). A New Efficient Protocol for Authentication and Certificate Status Management in Personal Area Networks. In: Levi, A., Savaş, E., Yenigün, H., Balcısoy, S., Saygın, Y. (eds) Computer and Information Sciences – ISCIS 2006. ISCIS 2006. Lecture Notes in Computer Science, vol 4263. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11902140_99
Download citation
DOI: https://doi.org/10.1007/11902140_99
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-47242-1
Online ISBN: 978-3-540-47243-8
eBook Packages: Computer ScienceComputer Science (R0)