Abstract
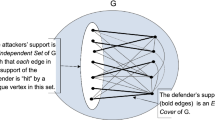
Consider a network vulnerable to security attacks and equipped with defense mechanisms. How much is the loss in the provided security guarantees due to the selfish nature of attacks and defenses? The Price of Defense was recently introduced in [7] as a worst-case measure, over all associated Nash equilibria, of this loss. In the particular strategic game considered in [7], there are two classes of confronting randomized players on a graph G(V, E): νattackers, each choosing vertices and wishing to minimize the probability of being caught, and a single defender, who chooses edges and gains the expected number of attackers it catches.
In this work, we continue the study of the Price of Defense. We obtain the following results:
– The Price of Defense is at least \(\frac{|V|}{2}\); this implies that the Perfect Matching Nash equilibria considered in [7] are optimal with respect to the Price of Defense, so that the lower bound is tight.
– We define Defense-Optimal graphs as those admitting a Nash equilibrium that attains the (tight) lower bound of \(\frac{|V|}{2}\). We obtain:
∙ A graph is Defense-Optimal if and only if it has a Fractional Perfect Matching. Since graphs with a Fractional Perfect Matching are recognizable in polynomial time, the same holds for Defense-Optimal graphs.
∙ We identify a very simple graph that is Defense-Optimal but has no Perfect Matching Nash equilibrium.
– Inspired by the established connection between Nash equilibria and Fractional Perfect Matchings, we transfer a known bivaluedness result about Fractional Matchings to a certain class of Nash equilibria. So, the connection to Fractional Graph Theory may be the key to revealing the combinatorial structure of Nash equilibria for our network security game.
This work was partially supported by the European Union under IST FET Integrated Project 015964 AEOLUS.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Aspnes, J., Chang, K., Yampolskiy, A.: Inoculation Strategies for Victims of Viruses and the Sum-of-Squares Problem. In: Proceedings of the 16th Annual ACMSIAM Symposium on Discrete Algorithms, pp. 43–52 (2005)
Bourjolly, J.-M., Pulleyblank, W.R.: König-Egerváry Graphs, 2-Bicritical Graphs and Fractional Matchings. Discrete Applied Mathematics 24, 63–82 (1989)
Cheswick, E.R., Bellovin, S.M.: Firewalls and Internet Security. Addison-Wesley, Reading (1994)
Gelastou, M., Mavronicolas, M., Papadopoulou, V., Philippou, A., Spirakis, P.: The Power of the Defender. In: CD-ROM Proceedings of the 2nd International Workshop on Incentive-Based Computing (July 2006)
Koutsoupias, E., Papadimitriou, C.H.: Worst-Case Equilibria. In: Meinel, C., Tison, S. (eds.) STACS 1999. LNCS, vol. 1563, pp. 404–413. Springer, Heidelberg (1999)
Markham, T., Payne, C.: Security at the Network Edge: A Distributed Firewall Architecture. In: Proceedings of the 2nd DARPA Information Survivability Conference and Exposition, vol. 1, pp. 279–286 (2001)
Mavronicolas, M., Michael, L., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: The Price of Defense. In: Královič, R., Urzyczyn, P. (eds.) MFCS 2006. LNCS, vol. 4162, pp. 717–728. Springer, Heidelberg (2006)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: A Network Game with Attacker and Protector Entities. In: Deng, X., Du, D.-Z. (eds.) ISAAC 2005. LNCS, vol. 3827, pp. 288–297. Springer, Heidelberg (2005)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spiraki, P.G.: A Graph-Theoretic Network Security Game. In: Deng, X., Ye, Y. (eds.) WINE 2005. LNCS, vol. 3828, pp. 969–978. Springer, Heidelberg (2005)
Mavronicolas, M., Spirakis, P.: The Price of Selfish Routing. In: Proceedings of the 33rd Annual ACM Symposium on Theory of Computing, pp. 510–519 (2001)
Moscibroda, T., Schmid, S., Wattenhofer, R.: When Selfish Meets Evil: Byzantine Players in a Virus Inoculation Game. In: Proceedings of the 25th Annual ACM Symposium on Principles of Distributed Computing, pp. 35–44 (2006)
Nash, J.F.: Equilibrium Points in N-Person Games. Proceedings of National Acanemy of Sciences of the United States of America 36, 48–49 (1950)
Nash, J.F.: Non-Cooperative Games. Annals of Mathematics 54(2), 286–295 (1951)
Scheinerman, E.R., Ullman, D.H.: Fractional Graph Theory. Wiley-Interscience Series in Discrete Mathematics and Optimization (1997)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2006 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Mavronicolas, M., Papadopoulou, V., Persiano, G., Philippou, A., Spirakis, P. (2006). The Price of Defense and Fractional Matchings. In: Chaudhuri, S., Das, S.R., Paul, H.S., Tirthapura, S. (eds) Distributed Computing and Networking. ICDCN 2006. Lecture Notes in Computer Science, vol 4308. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11947950_13
Download citation
DOI: https://doi.org/10.1007/11947950_13
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-68139-7
Online ISBN: 978-3-540-68140-3
eBook Packages: Computer ScienceComputer Science (R0)