Abstract
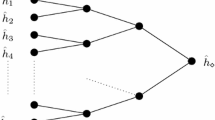
This article presents a rare case of a deterministic second preimage attack on a cryptographic hash function. Using the notion of controllable output differences, we show how to construct second preimages for the SMASH hash functions. If the given preimage contains at least n + 1 blocks, where n is the output length of the hash function in bits, then the attack is deterministic and requires only to solve a set of n linear equations. For shorter preimages, the attack is probabilistic.
The work described in this paper has been supported in part by the European Commission through the IST Programme under Contract IST-2002-507932 ECRYPT, and by the Austrian Science Fund (FWF) project P18138. The information in this document reflects only the author’s views, is provided as is and no guarantee or warranty is given that the information is fit for any particular purpose. The user thereof uses the information at its sole risk and liability.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Baretto, P.S.L.M., Rijmen, V.: The Whirlpool Hashing Function. Cryptology ePrint Archive, Report 2005/281 (2000) (revised in May 2003), http://paginas.terra.com.br/informatica/paulobarreto/WhirlpoolPage.html
Black, J., Rogaway, P., Shrimpton, T.: Black-Box Analysis of the Block-Cipher-Based Hash-Function Constructions from PGV. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 320–335. Springer, Heidelberg (2002)
Daemen, J., Rijmen, V.: A New MAC Construction ALRED and a Specific Instance ALPHA-MAC. In: Gilbert, H., Handschuh, H. (eds.) FSE 2005. LNCS, vol. 3557, pp. 1–17. Springer, Heidelberg (2005)
Dobbertin, H.: The First Two Rounds of MD4 are Not One-Way. In: Vaudenay, S. (ed.) FSE 1998. LNCS, vol. 1372, pp. 284–292. Springer, Heidelberg (1998)
Knudsen, L.R.: SMASH - A Cryptographic Hash Function. In: Gilbert, H., Handschuh, H. (eds.) FSE 2005. LNCS, vol. 3557, pp. 228–242. Springer, Heidelberg (2005)
Knudsen, L.R., Mathiassen, J.E.: Preimage and Collision Attacks on MD2. In: Gilbert, H., Handschuh, H. (eds.) FSE 2005. LNCS, vol. 3557, pp. 255–267. Springer, Heidelberg (2005)
Menezes, A.J., van Oorschot, P.C., Vanstone., S.A.: Handbook of Applied Cryptography. CRC Press, Boca Raton (1997), http://www.cacr.math.uwaterloo.ca/hac/
National Institute of Standards and Technology (NIST). FIPS-180-2: Secure Hash Standard (August 2002), Available online at: http://www.itl.nist.gov/fipspubs/
Pramstaller, N., Rechberger, C., Rijmen, V.: Breaking a New Hash Function Design Strategy Called SMASH. In: Preneel, B., Tavares, S. (eds.) SAC 2005. LNCS, vol. 3897, pp. 233–244. Springer, Heidelberg (2006)
Preneel, B., Govaerts, R., Vandewalle, J.: Hash Functions Based on Block Ciphers: A Synthetic Approach. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 368–378. Springer, Heidelberg (1994)
Rogaway, P., Shrimpton, T.: Cryptographic Hash-Function Basics: Definitions, Implications, and Separations for Preimage Resistance, Second-Preimage Resistance, and Collision Resistance. In: Roy, B.K., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, pp. 371–388. Springer, Heidelberg (2004)
Wang, X., Yin, Y.L., Yu, H.: Finding Collisions in the Full SHA-1. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 17–36. Springer, Heidelberg (2005)
Yu, H., Wang, G., Zhang, G., Wang, X.: The Second-Preimage Attack on MD4. In: Desmedt, Y.G., Wang, H., Mu, Y., Li, Y. (eds.) CANS 2005. LNCS, vol. 3810, pp. 1–12. Springer, Heidelberg (2005)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2006 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Lamberger, M., Pramstaller, N., Rechberger, C., Rijmen, V. (2006). Second Preimages for SMASH. In: Abe, M. (eds) Topics in Cryptology – CT-RSA 2007. CT-RSA 2007. Lecture Notes in Computer Science, vol 4377. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11967668_7
Download citation
DOI: https://doi.org/10.1007/11967668_7
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-69327-7
Online ISBN: 978-3-540-69328-4
eBook Packages: Computer ScienceComputer Science (R0)