Abstract
Consider two ordinary, seemingly identical plain paper shredders labeled A and B.Whe n each of the two shredders is fed a blank sheet of paper, the resulting remnants are sufficiently similar that they are indistinguishable upon visual inspection.Now suppose that one of the shredders has been modified to introduce imperceptible variations in the size of each remnant it cuts. One of the shredders is then selected at random to destroy a blank sheet.By examination of the resulting paper remnants, can one determine if the sheet was shredded by A or B?
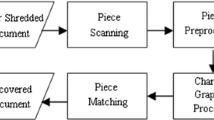
In this paper we show how information hidden in the size and shape of shredded page remnants can be used to reveal the identity of the device used for shredding.W e describe means for modifying shredders to introduce this hidden information. Experimental results reveal that properly embedded information can survive the severe nonlinear distortions introduced by the mechanics of paper shredding.F inally, we consider the question of whether paper shreds could reveal shredder identity even in the absence of device modifications.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
van Renesse, R. L.: Optical Document Security. Artech House, Boston (1993) 387
Wagner, N. R.: Fingerprinting. Proceedings of the 1983 IEEE Symposium on Security and Privacy. IEEE Computer Society (1983) 18–22 388
Golb, N.: Who Wrote the Dead Sea Scrolls? The Search for the Secret of Qumran. Scribner, New York (1995) 388
Ogden, J. A.: The Siting of Papyrus Fragments: An Experimental Application of Digital Computers. Ph.D. Thesis, University of Glascow (1969) 388
Levison, M.: The Siting of Fragments. The Computer Journal, vol 7, no 4 (1965) 388
Seul, M., O’Gorman, L., Sammon, M.: Practical Algorithms for Image Analysis: Description, Examples and Code. Cambridge University Press, Cambridge UK (2000) 391, 399
Helstrom, C. W.: Probability and Stochastic Processes for Engineers. MacMillan Publishing Co., New York (1984)
UPC Symbol Specification Manual. Uniform Code Council, Inc., Dayton Ohio (1986). See http://www.uc-council.org/re.ib/01302/d36-t.htm 396
Papoulis, A.: Probability, Random Variables and Stochastic Processes. McGraw-Hill Book Co., New York (1965) 397, 399
Information Security Team: Terminator VIII: How to Destroy your Classified Materials. Department of Defense Security Institute (1992). See http://www.dss.mil/training/term4/doc 398
Cohen, F.: The Mathematics of Shredding. Proceedings of the 2002 IEEE Symposium on Security and Privacy. IEEE Computer Society (2002) 399
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2003 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Brassil, J. (2003). Tracing the Source of a Shredded Document. In: Petitcolas, F.A.P. (eds) Information Hiding. IH 2002. Lecture Notes in Computer Science, vol 2578. Springer, Berlin, Heidelberg. https://doi.org/10.1007/3-540-36415-3_25
Download citation
DOI: https://doi.org/10.1007/3-540-36415-3_25
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-00421-9
Online ISBN: 978-3-540-36415-3
eBook Packages: Springer Book Archive