Abstract
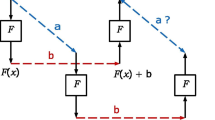
Bakhtiari et al recently proposed a fast message authentication primitive called KHF. This paper shows that KHF is highly vulnerable to differential cryptanalysis: it can be broken with about 37 chosen message queries. This suggests that the KHF design should be reconsidered.
Chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
References
S. Bakhtiari, R. Safavi-Naini, and J. Pieprzyk, “Keyed hash functions,” Cryptography: Policy and Algorithms, E. Dawson and Jovan Golic (Eds), Lecture Notes in Computer Science, vol. 1029, Springer-Verlag, 1996, pp.201–214.
E. Biham and A. Shamir, Differential Cryptanalysis of the Data Encryption Standard, Springer-Verlag, 1993.
B. Preneel, P.C. van Oorschot, “MDx-MAC and building fast MACs from hash functions,” Advances in Cryptology—CRYPTO’ 95, Springer-Verlag, 1995, pp. 1–14.
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 1998 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Wagner, D. (1998). Differential Cryptanalysis of KHF. In: Vaudenay, S. (eds) Fast Software Encryption. FSE 1998. Lecture Notes in Computer Science, vol 1372. Springer, Berlin, Heidelberg. https://doi.org/10.1007/3-540-69710-1_20
Download citation
DOI: https://doi.org/10.1007/3-540-69710-1_20
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-64265-7
Online ISBN: 978-3-540-69710-7
eBook Packages: Springer Book Archive