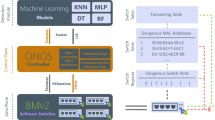
Abstract
One of the most critical issues emerging from the Internet is the diverse number of spyware and bots. When a spyware is installed in your PC then it will be difficult to detect, mainly because it deploys covert channels to communicate with outbound data transmissions. These attacks are usually sent from PCs infected with a bot that communicates with malicious controllers over an encrypted channel. However, the available pattern-based intrusion detection system (IDS) and antivirus systems (AVs) are unable to detect the infected PC. This paper presents a Monitoring and Filtering method (SMF) for outgoing packets based on machine learning and behavioral-based methods that can help in the protection of PCs. In addition, this paper presents recent research contributions and emerging tools in the field of spyware detection and identifies existing gaps in the literature. The paper then presents a High-level Architecture to inspect the outgoing packet from the hardware and the software installed in PCs as a solution.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Zou, C.C., Cunningham, R.: Honeypot-aware advanced botnet construction and maintenance. In: Proceeding of the DSN 2006, pp. 199–208, June 2006
Sudo, T., Fujiwara, K.: The evaluation of the botnet analysis system based on the virtual Internet environment. In: Proceeding of the CSS 2006, pp. 513–158. IPSJ, October 2006
Miwa, S., Miyachi, T., Miyachi, T., Eto, M., Yoshizumi, M., Shinoda, Y.: Design issues of isolated sandbox for analyzing. In: Proceeding of the IWSEC 2007, pp. 13–27. IPSJ, October 2007
Kondo, S., Sato, N.: Botnet traffic detection techniques by C&C session classification using SVM. In: Proceeding of the IWSEC 2007, pp. 91–104. IPSJ, October 2007
Chien, E.: Techniques of Adware and Spyware. WWW document (2005). https://www.symantec.com/avcenter/reference/techniques.of.adware.and.spyware.pdf. Accessed 15 Feb 2017
Jang-Jaccard, J., Nepal, S.: A survey of emerging threats in cybersecurity. J. Comput. Syst. Sci. 80(5), 973–993 (2014). ISSN 0022-0000
Konrad, R., Trinius, P., Willems, C., Holz, T.: Automatic analysis of malware behavior using machine learning. J. Comput. Secur. 19, 639–668 (2011)
Harley, D., Lee, A.: Heuristic Analysis—Detecting Unknown Viruses (2009)
Kaleem Awan, M.S., Burnap, P., Rana, O.: Identifying cyber risk hotspots: a framework for measuring temporal variance in computer network risk. Comput. Secur. 57, 31–46 (2016). ISSN 0167-4048
Sultan, K., Ali, H., Zhang, Z.: Call detail records driven anomaly detection and traffic prediction in mobile cellular networks. IEEE Access 6, 41728–41737 (2018)
Takemori, K., Nishigaki, M., Takami, T., Miyake, Y.: Detection of Bot infected PCs using destination-based IP and domain whitelists during a non-operating term. In: IEEE GLOBECOM 2008 - 2008 IEEE Global Telecommunications Conference, pp. 1–6 (2008)
Dragos, G., Cimpoesu, M., Anton, D., Ciortuz, L.: Malware detection using machine learning. In: Proceedings of the International Multiconference on Computer Science and Information Technology, pp. 735–741 (2009)
Priyank, S., Raul, N.: Malware Detection Module using Machine Learning Algorithms to Assist in Centralized Security in Enterprise Networks (2015)
Usukhbayar, B., Jambaljav, N., Horng, S.: A Static Malware Detection System Using Data Mining Methods. Cornell University (2013)
Mamoun, A., Venkatraman, S., Watters, P., Alazab, M.: Zero-day malware detection based on supervised learning algorithms of API call signatures. In: Proceedings of the 9-th Australasian Data Mining Conference, pp. 171–181 (2011)
Forte, D.: Spyware: more than a costly annoyance. Netw. Secur. 2005(12), 8–10 (2005). ISSN 1353-4858
Caballero, A.: Information security essentials for information technology managers. In: Computer and Information Security Handbook, pp. 393–419 (2017)
Chen, T.M., Walsh, P.J.: Guarding against network intrusions. In: Network and System Security, pp. 57–82 (2014)
Arasteh, A.R., Debbabi, M.: Forensic memory analysis: from stack and code to execution history. Sci. Direct Digital Invest. 4(Supplement), 114–125 (2017)
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Afzulpurkar, A., Alshemaili, M., Samara, K. (2019). Outgoing Data Filtration for Detecting Spyware on Personal Computers. In: Barolli, L., Xhafa, F., Khan, Z., Odhabi, H. (eds) Advances in Internet, Data and Web Technologies. EIDWT 2019. Lecture Notes on Data Engineering and Communications Technologies, vol 29. Springer, Cham. https://doi.org/10.1007/978-3-030-12839-5_32
Download citation
DOI: https://doi.org/10.1007/978-3-030-12839-5_32
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-12838-8
Online ISBN: 978-3-030-12839-5
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)