Abstract
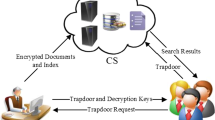
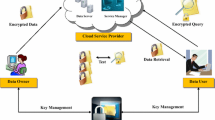
With the advances of technology, large amount of data is generated daily, which makes the traditional systems not to be able to handle such large quantities of data. A natural upgrade is to move to the cloud. In the last few years this was a trend adopted by an increasing number of organizations. Even an individual user uses the cloud in form of software as a service, for example, Google Drive, Google Docs, Microsoft OneDrive, Amazon Elastic Cloud etc. Also, a new trend is that smartphone manufacturers to provide a limited cloud storage in their own cloud for every user, storage used for data back-up or data storage. Extending the idea, an organization has much more data than an individual user and moving them to the cloud could be an advantage. But an organization or even an individual have sensitive documents stored on cloud and cloud computing brings many security challenges. A response to these challenges is searchable encryption, which allows searching for encrypted keywords over encrypted data on a server. In this paper, we propose a searchable encryption scheme, based on word suffix tree, in which we use two different algorithms to encrypt the keywords and documents.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
10 Key marketing trends for 2017 and ideas for exceeding customer expectations. IBM Marketing Cloud (2017)
Mell, P., Grance, T.: The NIST definition of cloud computing (2011)
Chang, V., Bacigalupo, D., Wills, G., De Roure, D.: A categorisation of cloud computing business models. In: Proceedings of the 2010 10th IEEE/ACM International Conference on Cluster, Cloud and Grid Computing, pp. 509–512. IEEE Computer Society (2010)
Ali, M., Khan, S.U., Vasilakos, A.V.: Security in cloud computing: opportunities and challenges. Inf. Sci. 305, 357–383 (2015)
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 223–238. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-48910-X_16
Okamoto, T., Uchiyama, S.: A new public-key cryptosystem as secure as factoring. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 308–318. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054135
Curtmola, R., Garay, J., Kamara, S., Ostrovsky, R.: Searchable symmetric encryption: improved definitions and efficient constructions. J. Comput. Secur. 19(5), 895–934 (2011)
Wang, Y., Wang, J., Chen, X.: Secure searchable encryption: a survey. J. Commun. Inf. Netw. 1(4), 52–65 (2016)
Weiner, P.: Linear pattern matching algorithms. In: 1973 IEEE Conference Record of 14th Annual Symposium on Switching and Automata Theory, SWAT 2008, pp. 1–11. IEEE (1973)
McCreight, E.M.: A space-economical suffix tree construction algorithm. J. ACM (JACM) 23(2), 262–272 (1976)
Ukkonen, E.: Constructing suffix trees on-line in linear time. In: Proceedings of the IFIP 12th World Computer Congress on Algorithms, Software, Architecture-Information Processing 1992, pp. 484–492. North-Holland Publishing Co. (1992)
Inenaga, S., Takeda, M.: On-line linear-time construction of word suffix trees. In: Lewenstein, M., Valiente, G. (eds.) CPM 2006. LNCS, vol. 4009, pp. 60–71. Springer, Heidelberg (2006). https://doi.org/10.1007/11780441_7
Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 506–522. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24676-3_30
Abdalla, M., et al.: Searchable encryption revisited: consistency properties, relation to anonymous IBE, and extensions. J. Cryptol. 21(3), 350–391 (2008)
Di Crescenzo, G., Saraswat, V.: Public key encryption with searchable keywords based on Jacobi symbols. In: Srinathan, K., Rangan, C.P., Yung, M. (eds.) INDOCRYPT 2007. LNCS, vol. 4859, pp. 282–296. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-77026-8_21
Baek, J., Safavi-Naini, R., Susilo, W.: Public key encryption with keyword search revisited. In: Gervasi, O., Murgante, B., Laganà, A., Taniar, D., Mun, Y., Gavrilova, M.L. (eds.) ICCSA 2008. LNCS, vol. 5072, pp. 1249–1259. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-69839-5_96
Rhee, H.S., Park, J.H., Susilo, W., Lee, D.H.: Trapdoor security in a searchable public-key encryption scheme with a designated tester. J. Syst. Softw. 83(5), 763–771 (2010)
Boneh, D., Waters, B.: Conjunctive, subset, and range queries on encrypted data. In: Vadhan, S.P. (ed.) TCC 2007. LNCS, vol. 4392, pp. 535–554. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-70936-7_29
Ma, S., Mu, Y., Susilo, W., Yang, B.: Witness-based searchable encryption. Inf. Sci. 453, 364–378 (2018)
Mahreen, S.K., Warsi, M.R., Neelam, S.K.: Domain dictionary-based metadata construction for search over encrypted cloud data. In: Singh, R., Choudhury, S., Gehlot, A. (eds.) Intelligent Communication, Control and Devices. AISC, vol. 624, pp. 661–669. Springer, Singapore (2018). https://doi.org/10.1007/978-981-10-5903-2_68
Etemad, M., Küpçü, A., Papamanthou, C., Evans, D.: Efficient dynamic searchable encryption with forward privacy. In: Proceedings on Privacy Enhancing Technologies, vol. 2018, no. 1, pp. 5–20 (2018)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Nita, S.L., Mihailescu, M.I. (2019). A Hybrid Searchable Encryption Scheme for Cloud Computing. In: Lanet, JL., Toma, C. (eds) Innovative Security Solutions for Information Technology and Communications. SECITC 2018. Lecture Notes in Computer Science(), vol 11359. Springer, Cham. https://doi.org/10.1007/978-3-030-12942-2_8
Download citation
DOI: https://doi.org/10.1007/978-3-030-12942-2_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-12941-5
Online ISBN: 978-3-030-12942-2
eBook Packages: Computer ScienceComputer Science (R0)