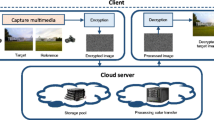
Abstract
The integration of cloud computing and smart multimedia gadgets has made an attractive business model today. However, data privacy is one of the major concern when moving to third party driven infrastructures like cloud. Furthermore, due to diverse camera sensors, the captured multimedia may contain insufficient lightning/colors and processing them manually is a painstakingly task. A few schemes have been proposed to address this problem, however they suffered from the major drawback of computational and storage overhead, and becomes non-trivial in case of videos. Considering these challenges, we propose an automatic video color grading approach in this chapter. The proposed approach enables cloud data center to process encrypted multimedia data by transferring its colors as per an example image as the reference. We analyze the correlation between consecutive video sequences and propose to evaluate the color transformation parameters for every alternate video frame. In addition, proxy encryption based Paillier cryptosystem has been used for video encryption. As a result, the computational and storage overheads are drastically reduced with effective video grading results. The feasibility and robustness of the proposed approach are validated through various tests.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Barni, M., Bianchi, T., Catalano, D., Di Raimondo, M., Donida Labati, R., Failla, P., Fiore, D., Lazzeretti, R., Piuri, V., Scotti, F. et al. [2010], Privacy-preserving fingercode authentication, in ‘Proceedings of the 12th ACM workshop on Multimedia and security’, ACM, pp. 231–240.
Boneh, D., Goh, E.-J. and Nissim, K. [2005], Evaluating 2-dnf formulas on ciphertexts, in ‘Theory of Cryptography Conference’, Springer, pp. 325–341.
Boneh, D. et al. [ 1999], ‘Twenty years of attacks on the rsa cryptosystem’, Notices of the AMS 46(2), 203–213.
Brakerski, Z. [ 2012], Fully homomorphic encryption without modulus switching from classical gapsvp, in ‘Advances in cryptology–crypto 2012’, Springer, pp. 868–886.
Bresson, E., Catalano, D. and Pointcheval, D. [2003], A simple public-key cryptosystem with a double trapdoor decryption mechanism and its applications, in ‘International Conference on the Theory and Application of Cryptology and Information Security’, Springer, pp. 37–54.
Chan, A. B., Liang, Z.-S. J. and Vasconcelos, N. [2008], Privacy preserving crowd monitoring: Counting people without people models or tracking, in ‘Computer Vision and Pattern Recognition, 2008. CVPR 2008. IEEE Conference on’, IEEE, pp. 1–7.
Chen, X., Huang, X., Li, J., Ma, J., Lou, W. and Wong, D. S. [ 2015], ‘New algorithms for secure outsourcing of large-scale systems of linear equations’, IEEE transactions on information forensics and security 10(1), 69–78.
Coron, J.-S., Mandal, A., Naccache, D. and Tibouchi, M. [ 2011], Fully homomorphic encryption over the integers with shorter public keys, in ‘Annual Cryptology Conference’, Springer, pp. 487–504.
ElGamal, T. [ 1985], ‘A public key cryptosystem and a signature scheme based on discrete logarithms’, IEEE transactions on information theory 31(4), 469–472.
Erkin, Z., Franz, M., Guajardo, J., Katzenbeisser, S., Lagendijk, I. and Toft, T. [ 2009], Privacy-preserving face recognition, in ‘International Symposium on Privacy Enhancing Technologies’, Springer, pp. 235–253.
Ferreira, B., Rodrigues, J., Leitao, J. and Domingos, H. [ 2015], Privacy-preserving content-based image retrieval in the cloud, in ‘Reliable Distributed Systems (SRDS), 2015 IEEE 34th Symposium on’, IEEE, pp. 11–20.
Gentry, C. [ 2010], ‘Computing arbitrary functions of encrypted data’, Communications of the ACM 53(3), 97–105.
Gentry, C., Halevi, S. and Smart, N. P. [ 2012 a], Better bootstrapping in fully homomorphic encryption, in ‘International Workshop on Public Key Cryptography’, Springer, pp. 1–16.
Gentry, C., Halevi, S. and Smart, N. P. [ 2012 b], Fully homomorphic encryption with polylog overhead, in ‘Annual International Conference on the Theory and Applications of Cryptographic Techniques’, Springer, pp. 465–482.
Gentry, C., Sahai, A. and Waters, B. [2013], Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based, in ‘Advances in Cryptology–CRYPTO 2013’, Springer, pp. 75–92.
Goldwasser, S. and Micali, S. [ 1982], Probabilistic encryption & how to play mental poker keeping secret all partial information, in ‘Proceedings of the fourteenth annual ACM symposium on Theory of computing’, ACM, pp. 365–377.
Guo, J., Zheng, P. and Huang, J. [2017], ‘An efficient motion detection and tracking scheme for encrypted surveillance videos’, ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 13(4), 61.
Halevi, S. and Shoup, V. [ 2014], Algorithms in helib, in ‘International Cryptology Conference’, Springer, pp. 554–571.
Halevi, S. and Shoup, V. [ 2015], Bootstrapping for helib, in ‘Annual International conference on the theory and applications of cryptographic techniques’, Springer, pp. 641–670.
Hsu, C.-Y., Lu, C.-S. and Pei, S.-C. [2012], ‘Image feature extraction in encrypted domain with privacy-preserving sift’, IEEE Transactions on Image Processing 21(11), 4593–4607.
Hu, X., Zhang, W., Li, K., Hu, H. and Yu, N. [2016], ‘Secure nonlocal denoising in outsourced images’, ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 12(3), 40.
Jagannathan, G. and Wright, R. N. [2005], Privacy-preserving distributed k-means clustering over arbitrarily partitioned data, in ‘Proceedings of the eleventh ACM SIGKDD international conference on Knowledge discovery in data mining’, ACM, pp. 593–599.
Jia, L. and Radke, R. J. [ 2014], ‘Using time-of-flight measurements for privacy-preserving tracking in a smart room’, IEEE Transactions on Industrial Informatics 10(1), 689–696.
Jost, C., Lam, H., Maximov, A. and Smeets, B. J. [2015], ‘Encryption performance improvements of the paillier cryptosystem.’, IACR Cryptology ePrint Archive 2015, 864.
Kargupta, H., Datta, S., Wang, Q. and Sivakumar, K. [2005], ‘Random-data perturbation techniques and privacy-preserving data mining’, Knowledge and Information Systems 7(4), 387–414.
Lathey, A. and Atrey, P. K. [ 2015], ‘Image enhancement in encrypted domain over cloud’, ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 11(3), 38.
Lathey, A., Atrey, P. K. and Joshi, N. [2013], Homomorphic low pass filtering on encrypted multimedia over cloud, in ‘IEEE Seventh International Conference on Semantic Computing (ICSC)’, IEEE, pp. 310–313.
Marwan, M., Kartit, A. and Ouahmane, H. [2018], ‘Security enhancement in healthcare cloud using machine learning’, Procedia Computer Science 127, 388–397.
Mohanty, M., Asghar, M. R. and Russello, G. [2016], ‘2dcrypt: Image scaling and cropping in encrypted domains’, IEEE Transactions on Information Forensics and Security 11(11), 2542–2555.
Mohanty, M., Ooi, W. T. and Atrey, P. K. [ 2013 a], Scale me, crop me, knowme not: Supporting scaling and cropping in secret image sharing, in ‘IEEE International Conference on Multimedia and Expo (ICME)’, IEEE, pp. 1–6.
Mohanty, M., Ooi, W. T. and Atrey, P. K. [ 2013 b], Secure cloud-based volume ray-casting, in ‘International Conference on Cloud Computing Technology and Science (CloudCom)’, Vol. 1, IEEE, pp. 531–538.
Paillier, P. [ 1999], Public-key cryptosystems based on composite degree residuosity classes, in ‘International Conference on the Theory and Applications of Cryptographic Techniques’, Springer, pp. 223–238.
Rahulamathavan, Y., Phan, R. C.-W., Chambers, J. A. and Parish, D. J. [ 2013], ‘Facial expression recognition in the encrypted domain based on local fisher discriminant analysis’, IEEE Transactions on Affective Computing 4(1), 83–92.
Rahulamathavan, Y., Veluru, S., Phan, R. C.-W., Chambers, J. A. and Rajarajan, M. [ 2014], ‘Privacy-preserving clinical decision support system using gaussian kernel-based classification’, IEEE journal of biomedical and health informatics 18(1), 56–66.
Rajput, A. S. and Raman, B. [ 2017], Color me, store me, know me not: Supporting image color transfer and storage in encrypted domain over cloud, in ‘International Conference on Multimedia & Expo Workshops (ICMEW)’, IEEE, pp. 291–296.
Rajput, A. S. and Raman, B. [ 2018 a], ‘Cloud based image color transfer and storage in encrypted domain’, Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-5580-2 pp. 1–29.
Rajput, A. S. and Raman, B. [ 2018 b], ‘Cryptoct: towards privacy preserving color transfer and storage over cloud’, Multimedia Tools and Applications. https://doi.org/10.1007/s11042-018-5729-7 pp. 1–23.
Rane, S. and Boufounos, P. T. [ 2013], ‘Privacy-preserving nearest neighbor methods: Comparing signals without revealing them’, IEEE Signal Processing Magazine 30(2), 18–28.
Reinhard, E., Adhikhmin, M., Gooch, B. and Shirley, P. [ 2001], ‘Color transfer between images’, IEEE Computer graphics and applications 21(5), 34–41.
Rivest, R. L., Shamir, A. and Adleman, L. [1978], ‘A method for obtaining digital signatures and public-key cryptosystems’, Communications of the ACM 21(2), 120–126.
Shamir, A. [ 1979], ‘How to share a secret’, Communications of the ACM 22(11), 612–613.
Singh, P., Agarwal, N. and Raman, B. [2018], ‘Secure data deduplication using secret sharing schemes over cloud’, Future Generation Computer Systems.
Singh, P., Raman, B., Agarwal, N. and Atrey, P. K. [2017], ‘Secure cloud-based image tampering detection and localization using pob number system’, ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 13(3), 23.
Van Dijk, M., Gentry, C., Halevi, S. and Vaikuntanathan, V. [ 2010], Fully homomorphic encryption over the integers, in ‘Annual International Conference on the Theory and Applications of Cryptographic Techniques’, Springer, pp. 24–43.
Wang, Q., He, M., Du, M., Chow, S. S., Lai, R. W. and Zou, Q. [ 2016], ‘Searchable encryption over feature-rich data’, IEEE Transactions on Dependable and Secure Computing.
Weng, L., Amsaleg, L., Morton, A. and Marchand-Maillet, S. [ 2015], ‘A privacy-preserving framework for large-scale content-based information retrieval’, IEEE Transactions on Information Forensics and Security 10(1), 152–167.
Xia, Z., Wang, X., Zhang, L., Qin, Z., Sun, X. and Ren, K. [ 2016], ‘A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing’, IEEE Transactions on Information Forensics and Security 11(11), 2594–2608.
Yagisawa, M. [ 2015], ‘Fully homomorphic encryption without bootstrapping.’, IACR Cryptology ePrint Archive 2015, 474.
Yakubu, A. M., Maddage, N. C. and Atrey, P. K. [2017], ‘Securing speech noise reduction in outsourced environment’, ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 13(4), 51.
Yakubu, M. A., Maddage, N. C. and Atrey, P. K. [2016], Encrypted domain cloud-based speech noise reduction with comb filter, in ‘Multimedia & Expo Workshops (ICMEW), 2016 IEEE International Conference on’, IEEE, pp. 1–6.
Yao, A. C. [ 1982], Protocols for secure computations, in ‘23rd Annual Symposium on Foundations of Computer Science’, IEEE, pp. 160–164.
Zhou, J., Cao, Z., Dong, X. and Lin, X. [2015], ‘Ppdm: A privacy-preserving protocol for cloud-assisted e-healthcare systems’, IEEE Journal of Selected Topics in Signal Processing 9(7), 1332–1344.
Acknowledgement
This work was supported by Information Security Education and Awareness (ISEA) Project (phase II), Deity, Government of India.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Rajput, A.S., Raman, B. (2019). Example Based Privacy-Preserving Video Color Grading. In: Singh, A., Mohan, A. (eds) Handbook of Multimedia Information Security: Techniques and Applications. Springer, Cham. https://doi.org/10.1007/978-3-030-15887-3_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-15887-3_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-15886-6
Online ISBN: 978-3-030-15887-3
eBook Packages: Computer ScienceComputer Science (R0)