Abstract
We develop attacks on the security of variants of pseudo-random generators computed by quadratic polynomials. In particular we give a general condition for breaking the one-way property of mappings where every output is a quadratic polynomial (over the reals) of the input. As a corollary, we break the degree-2 candidates for security assumptions recently proposed for constructing indistinguishability obfuscation by Ananth, Jain and Sahai (ePrint 2018) and Agrawal (ePrint 2018). We present conjectures that would imply our attacks extend to a wider variety of instances, and in particular offer experimental evidence that they break assumption of Lin-Matt (ePrint 2018).
Our algorithms use semidefinite programming, and in particular, results on low-rank recovery (Recht, Fazel, Parrilo 2007) and matrix completion (Gross 2009).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The work of Ananth, Jain, and Sahai [2] also considered degree-3 polynomials. We do not have attacks on such degree-3 polynomials; we discuss this further below.
- 2.
This cubic version of their assumption was made explicit in an update to [2].
- 3.
Along the same lines, we note that if \(\mathcal Q\) is nice and \({\mathbb {E}}_{q \sim \mathcal Q} q = 0\) (as we observe later, the latter can be enforced without loss of generality) then \(\mathcal Q\) is also \(\varLambda (n)\)-bounded for \(\varLambda (n) \leqslant O(n)\). The reason is that if \(\mathcal Q\) is nice and has \({\mathbb {E}}\, q = 0\) then
$$ {\mathbb {E}}\Vert q\Vert ^2 = \sum _{i,j \leqslant n} {\mathbb {E}}\, Q_{ij}^2 = \sum _{i,j \leqslant n} Var(Q_{ij}) = n^2\,.$$For every i, j and every q in the support of \(\mathcal Q\), we have by niceness that \(|q_{ij}| \leqslant \Vert q\Vert _2 \leqslant C n\). Hence \(\mathcal Q\) is O(n)-bounded.
One implication is that \(\mathcal Q\) cannot be a distribution on where the all-zero polynomial appears with probability, say, \(1-1/n\), as otherwise its support would also have to contain polynomials with coefficients \(\gg n\). Our main theorem could not apply to such a distribution, since clearly at least \(\varOmega (n^2)\) independent samples would be needed to get enough information to recover x from \(\{q_i,q_i(x)\}\), while we assume \(m \leqslant n(\log n)^{O(1)} \ll n^2\).
- 4.
For any \(q(x) = \sum _{i,j}q_{i\leqslant j} x_i x_j\), we define \(Q:\mathbb R^{n\times n}\rightarrow \mathbb R\) by \(Q_{i,j} = Q_{j,i}= q_{i,j}/2\). Then,
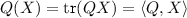 is a linear map on \(\mathbb R^{n \times n}\).
is a linear map on \(\mathbb R^{n \times n}\).
References
Agrawal, S.: New methods for indistinguishability obfuscation: Bootstrapping and instantiation. IACR Cryptology ePrint Archive 2018, 633 (2018). https://eprint.iacr.org/2018/633
Ananth, P., Jain, A., Sahai, A.: Indistinguishability obfuscation without multilinear maps: iO from LWE, bilinear maps, and weak pseudorandomness. IACR Cryptology ePrint Archive 2018, 615 (2018). https://eprint.iacr.org/2018/615
Ananth, P., Sahai, A.: Projective arithmetic functional encryption and indistinguishability obfuscation from degree-5 multilinear maps. In: Coron, J.-S., Nielsen, J.B. (eds.) EUROCRYPT 2017, Part I. LNCS, vol. 10210, pp. 152–181. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-56620-7_6
Barak, B., Brakerski, Z., Komargodski, I., Kothari, P.K.: Limits on low-degree pseudorandom generators (or: sum-of-squares meets program obfuscation). In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018, Part II. LNCS, vol. 10821, pp. 649–679. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78375-8_21
Boneh, D., Silverberg, A.: Applications of multilinear forms to cryptography. Contemp. Math. 324, 71–90 (2002)
Boneh, D., Wu, D.J., Zimmerman, J.: Immunizing multilinear maps against zeroizing attacks. IACR Cryptology ePrint Archive 2014, 930 (2014). http://eprint.iacr.org/2014/930
Brakerski, Z., Gentry, C., Halevi, S., Lepoint, T., Sahai, A., Tibouchi, M.: Cryptanalysis of the quadratic zero-testing of GGH. Cryptology ePrint Archive, Report 2015/845 (2015). http://eprint.iacr.org/
Cheon, J.H., Han, K., Lee, C., Ryu, H., Stehlé, D.: Cryptanalysis of the multilinear map over the integers. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015, Part I. LNCS, vol. 9056, pp. 3–12. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46800-5_1
Cheon, J.H., Lee, C., Ryu, H.: Cryptanalysis of the new clt multilinear maps. Cryptology ePrint Archive, Report 2015/934 (2015). http://eprint.iacr.org/
Coron, J.-S., et al.: Zeroizing without low-level zeroes: new MMAP attacks and their limitations. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015, Part I. LNCS, vol. 9215, pp. 247–266. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-47989-6_12
Daniely, A., Linial, N., Shalev-Shwartz, S.: From average case complexity to improper learning complexity. In: STOC, pp. 441–448. ACM (2014)
Feige, U.: Relations between average case complexity and approximation complexity. In: STOC, pp. 534–543. ACM (2002)
Garg, S., Gentry, C., Halevi, S.: Candidate multilinear maps from ideal lattices. In: Johansson, T., Nguyen, P.Q. (eds.) EUROCRYPT 2013. LNCS, vol. 7881, pp. 1–17. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-38348-9_1
Garg, S., Gentry, C., Halevi, S., Raykova, M., Sahai, A., Waters, B.: Candidate indistinguishability obfuscation and functional encryption for all circuits. In: 54th Annual IEEE Symposium on Foundations of Computer Science, FOCS 2013, 26–29 October, 2013, Berkeley, pp. 40–49 (2013)
Grigoriev, D.: Linear lower bound on degrees of positivstellensatz calculus proofs for the parity. Theor. Comput. Sci. 259(1–2), 613–622 (2001)
Gross, D.: Recovering low-rank matrices from few coefficients in any basis. IEEE Trans. Inform. Theory 57(3), 1548–1566 (2011). https://doi.org/10.1109/TIT.2011.2104999
Halevi, S.: Graded encoding, variations on a scheme. IACR Cryptol. ePrint Archive 2015, 866 (2015)
Hu, Y., Jia, H.: Cryptanalysis of GGH map. IACR Cryptol. ePrint Archive 2015, 301 (2015)
Lin, H.: Indistinguishability obfuscation from constant-degree graded encoding schemes. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016, Part I. LNCS, vol. 9665, pp. 28–57. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49890-3_2
Lin, H.: Indistinguishability obfuscation from SXDH on 5-linear maps and locality-5 PRGs. In: Katz, J., Shacham, H. (eds.) CRYPTO 2017, Part I. LNCS, vol. 10401, pp. 599–629. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-63688-7_20
Lin, H., Matt, C.: Pseudo flawed-smudging generators and their application to indistinguishability obfuscation. IACR Cryptology ePrint Archive 2018, 646 (2018). https://eprint.iacr.org/2018/646
Lin, H., Tessaro, S.: Indistinguishability obfuscation from bilinear maps and block-wise local PRGs. Cryptology ePrint Archive, Report 2017/250 (2017). http://eprint.iacr.org/2017/250
Lin, H., Vaikuntanathan, V.: Indistinguishability obfuscation from DDH-like assumptions on constant-degree graded encodings. In: IEEE 57th Annual Symposium on Foundations of Computer Science, FOCS 2016, 9–11 October 2016, Hyatt Regency, New Brunswick, pp. 11–20 (2016)
Lombardi, A., Vaikuntanathan, V.: On the non-existence of blockwise 2-local prgs with applications to indistinguishability obfuscation. IACR Cryptology ePrint Archive 2017, 301 (2017). http://eprint.iacr.org/2017/301
Miles, E., Sahai, A., Zhandry, M.: Annihilation attacks for multilinear maps: cryptanalysis of indistinguishability obfuscation over GGH13. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016, Part II. LNCS, vol. 9815, pp. 629–658. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53008-5_22
Minaud, B., Fouque, P.A.: Cryptanalysis of the new multilinear map over the integers. Cryptology ePrint Archive, Report 2015/941 (2015). http://eprint.iacr.org/
Recht, B.: A simpler approach to matrix completion. J. Mach. Learn. Res. 12, 3413–3430 (2011)
Recht, B., Fazel, M., Parrilo, P.A.: Guaranteed minimum-rank solutions oflinear matrix equations via nuclear norm minimization. SIAM Rev. 52(3), 471–501 (2010). https://doi.org/10.1137/070697835
Sahai, A., Waters, B.: How to use indistinguishability obfuscation: deniable encryption, and more. In: Symposium on Theory of Computing, STOC 2014, New York, May 31 - June 03, 2014, pp. 475–484 (2014)
Schoenebeck, G.: Linear level lasserre lower bounds for certain k-CSPs. In: 49th Annual IEEE Symposium on Foundations of Computer Science, FOCS 2008, 25–28 October 2008, Philadelphia, pp. 593–602 (2008)
Acknowledgements
Boaz Barak was supported by NSF awards CCF 1565264 and CNS 1618026 and a Simons Investigator Fellowship. Samuel B. Hopkins was supported by a Miller Postdoctoral Fellowship and NSF award CCF 1408673. Pravesh Kothari was supported in part by Ma fellowship from the Schmidt Foundation and Avi Wigderson’s NSF award CCF-1412958. Amit Sahai and Aayush Jain were supported in part from a DARPA/ARL SAFEWARE award, NSF Frontier Award 1413955, and NSF grant 1619348, BSF grant 2012378, a Xerox Faculty Research Award, a Google Faculty Research Award, an equipment grant from Intel, and an Okawa Foundation Research Grant. Aayush Jain was also supported by Google PhD Fellowship 2018, in the area of Privacy and Security. This material is based upon work supported by the Defense Advanced Research Projects Agency through the ARL under Contract W911NF-15-C- 0205. The views expressed are those of the authors and do not reflect the official policy or position of the Department of Defense, the National Science Foundation, the U.S. Government or Google.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Julia Code
A Julia Code









Rights and permissions
Copyright information
© 2019 International Association for Cryptologic Research
About this paper
Cite this paper
Barak, B., Hopkins, S.B., Jain, A., Kothari, P., Sahai, A. (2019). Sum-of-Squares Meets Program Obfuscation, Revisited. In: Ishai, Y., Rijmen, V. (eds) Advances in Cryptology – EUROCRYPT 2019. EUROCRYPT 2019. Lecture Notes in Computer Science(), vol 11476. Springer, Cham. https://doi.org/10.1007/978-3-030-17653-2_8
Download citation
DOI: https://doi.org/10.1007/978-3-030-17653-2_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-17652-5
Online ISBN: 978-3-030-17653-2
eBook Packages: Computer ScienceComputer Science (R0)





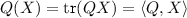 is a linear map on
is a linear map on 