Abstract
To protect distributed network resources and assets, collaborative intrusion detection systems/networks (CIDSs/CIDNs) have been widely deployed in various organizations with the purpose of detecting any potential threats. While such systems and networks are usually vulnerable to insider attacks, some kinds of trust mechanisms should be integrated in a real-world application. Challenge-based trust mechanisms are one promising solution, which can measure the trustworthiness of a node by sending challenges to other nodes. In the literature, challenge-based CIDNs have proven to be robust against common insider attacks, but it may still be susceptible to advanced insider attacks. How to further improve the robustness of challenge-based CIDNs remains an issue. Motivated by the recently rapid development of blockchains, in this work, we aim to combine these two and provide a blockchained challenge-based CIDN framework. Our evaluation shows that blockchain technology has the potential to enhance the robustness of challenge-based CIDNs in the aspects of trust management (i.e., enhancing the detection of insider nodes) and alarm aggregation (i.e., identifying untruthful inputs).
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
- Intrusion detection
- Collaborative network
- Insider attack
- Blockchain technology
- Challenge-based trust mechanism
1 Introduction
Due to the connectivity and sensing features, Internet-of-Things (IoT) has been gradually adopted by many organizations. The Gartner manager predicted that the IoT would keep delivering new opportunities for digital business innovation over the next decade, many of which can be further boosted by newly developed technologies like artificial intelligence [12]. Their report forecasts that up to 14.2 billion things will be connected by the end of 2019, and will finally reach a total of 25 billion devices by the end of 2021 [11].
The rapid growth of IoT devices brings many benefits, i.e., facilitating our daily lives, but it also becomes a major target by cyber criminals. The Symantec security report indicated that the overall volume of IoT attacks remained consistent and high in 2018 [51]. In particular, connected cameras and routers were the most infected devices - there is an increase on the infection vector. While worms and bots are still the most commonly detected IoT attacks. For example, the Mirai distributed denial of service (DDoS) worm remained an active threat and, account for 16% of the detected attacks, which was the third most common IoT threat in 2018.
To help protect the security of IoT, intrusion detection systems (IDSs) are a basic and essential security mechanism. To fit the distributed nature, collaborative intrusion detection systems/network (CIDSs/CIDNs) are often deployed in a distributed environment, which allow a set of IDS nodes to exchange required messages and understand the protected environment [54, 59]. A detector could be either rule-based (signature-based) or anomaly-based. The former has to compare its stored rules with incoming events, in order to identify an attack [44, 55]. The latter discovers a potential threat through identifying an anomaly between its pre-built benign profile and the current profile [45].
Insider attacks are one major threat to distributed networks and environments, hence some trust mechanisms are often implemented to protect CIDSs/CIDNs. In the literature, challenge-based trust mechanism is one promising solution, which evaluates a node’s reputation by sending challenges and receiving the corresponding feedback [8]. A series of research like [8, 9] has proven its effectiveness against common insider attacks; however, some studies demonstrated that such challenge-based CIDNs may still be susceptible to advanced attacks [23,24,25, 27]. For instance, the Passive Message Fingerprint Attack (PMFA) [23] enables suspicious nodes to cooperate in identifying normal messages and remain their reputation without being detected. Thus, there is a great need to design a more robust challenge-based CIDNs to ensure its detection effectiveness. Below are three desirable attributes for a new CIDN framework.
-
To avoid the issue of a single point of failure (SPOF), the CIDN framework should not rely mainly on a centralized server.
-
The CIDN framework should provide a robust trust management process, which can evaluate the trustworthiness of nodes in an accurate way.
-
The CIDN framework should be able to identify malicious inputs, which are even from some trusted nodes.
Recently, blockchain technology has become quite popular encouraged by the success of cryptocurrency Bitcoin. The Gemalto report [10] indicates that the adoption of blockchains has doubled from 9% to 19% in the early 2019, and this trend is likely to continue in the next year and beyond. They also described a survey that up to 23% of respondents believed that blockchain technology would be an ideal solution to use for securing IoT devices, and 91% of organisations are likely to consider it in the future. For instance, Amazon announced its new managed service, Amazon Managed Blockchain, which allows users to set up and configure a scalable blockchain network with just a few clicks [2]. With a huge number of devices, blockchains can increasingly be used to monitor and record those communications and transactions in an IoT environment [29].
Currently, blockchains have been applied into many domains like IoT [28, 48], transportation [17, 22], and energy [47]. The strong encryption used to secure blockchains can greatly increase the difficulty for cyber criminals to brute-force their way into private and sensitive environments. Due to these merits, some research has started trying to combine blockchains with CIDSs/CIDNs. An initial blockchain-based framework was proposed by Alexopoulos et al. [1], aiming to protect the alarm exchange among the collaborating nodes. They regarded raw alarms generated by the monitors are stored as transactions in a blockchain, replicated among the participating nodes of peer-to-peer network. While they did not show any experimental implementation or results. Tug et al. [52] introduced CBSigIDS, a framework of collaborative blockchained signature-based IDSs, by incrementally sharing and building a trusted signature database via blockchains in a CIDN network. They mainly targeted the combination of blockchains with signature-based IDSs, but remained anomaly-based detection as future work. On the other hand, a blockchain-based framework called CIoTA was proposed by Golomb et al. [13], which focused solely on anomaly detection via updating a trusted detection model.
Contributions. Though some studies have discussed the intersection between CIDSs and blockchains, to the best of our knowledge, most existing work was initialized at the high level, without specifying a concrete CIDS/CIDN. In addition, there is no work focusing on a specific trust-based detection system. To make up this gap, in this work, we focus on the challenge-based trust mechanism, and develop a blockchained challenge-based CIDN framework. Our contributions can be summarized as below.
-
To combine the blockchain technology with a concrete type of trust-based CIDN, we propose a blockchained challenge-based CIDN framework, which can be workable under both signature-based and anomaly-based detection. In particular, blockchains can be served as an additional layer to provide the flexibility in practical deployment.
-
Under our framework, we show how to use blockchains to enhance the robustness of trust management against attacks, as well as protect the alarm aggregation process from malicious inputs. The enhancement is valid for both signature-based and anomaly-based detection.
-
In the evaluation, we exploit the performance of our framework in the aspects of trust computation and alarm aggregation. Our results demonstrate that our framework can become more robust via the implementation of blockchains, i.e., identifying malicious nodes and untruthful inputs.
Paper Organization. Section 2 introduces research studies on collaborative intrusion detection and the background of blockchains. Section 3 describes our framework of blockchained challenge-based CIDNs that can be suitable for both signature-based and anomaly-based detection. We show how to use blockchains to enhance the trust management and alarm aggregation. Section 4 shows our experimental settings and analyzes the collected results. We discuss some challenges in Sect. 5 and conclude the work in Sect. 6.
2 Background and Related Work
In this section, we introduce the background of blockchain technology and review research studies on distributed detection systems, collaborative intrusion detection and blockchain-based detection.
2.1 Background of Blockchains
The original purpose of blockchains is to make payments between entities without a trust relationship and build a temper-resistant blockchain. Cryptocurrencies like Bitcoin have proven to be a phenomenal success. The underlying blockchain technique, which is an ingenious combination of multiple technologies such as peer-to-peer network, consensus protocol over a distributed network, cryptographic schemes, distributed database, smart contract and game theory, provides a decentralized way to build trust in our social and economic activities, and thus holds a huge promise to change the future of financial transactions, and even our way of computation and collaboration. As one of the hottest topics in the fields of IT and Fintech, blockchain has drawn much attention from researchers, as well as IT and FinTech industry. So far, both research community and industry community have made significant progresses in blockchain technologies and applications.
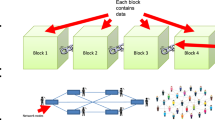
A blockchain node often maintains a list of records (known as blocks), which are organized in a chronological order based on discrete time stamps [60]. A block is typically comprised of a payload, a timestamp and a cryptographic hash value. The first block is called genesis block, and the node behind can connect to the previous one via a hash value. New blocks are added in a sequential manner with the next block containing a hash of the previous block. A new block can be generated once the previous block enters in the blockchain. The big feature of a block is that the recorded data in any block could not be modified without the alteration of all subsequent blocks [38]. The high-level review of blockchains is depicted in Fig. 1.
A blockchain can be generally classified into two categories: public blockchain and permissioned blockchains [60]. The former enables anyone to join and contribute to the network like Bitcoin [39] and Ethereum [58]. A public blockchain is completely open and anyone is free to join & leave. Everyone can participate in the major activities of the blockchain network including reading, writing and auditing the ongoing activities on the public blockchain network. The latter allows only verified entities to join the network, and perform only certain activities on the network like Hyperledger [15]. For example, Such blockchains would grant special permissions to each participant to have permissions to read, access and write pre-defined information on the blockchains. Blockchain nodes can make a decision-making process via consensus algorithms. There are some requirements for consensus algorithms in blockchains. For instance, the algorithm should collect all the agreements from chain nodes. Each node should aim at a better agreement to fit a whole interest.
There are may related studies focused on consensus mechanism. Badertscher et al. [3] put forth the first global universally composable (GUC) treatment of PoS-based blockchains in a setting that captures arbitrary numbers of parties that may not be fully operational (i.e., dynamic availability, which naturally captures decentralized environments within which real-world deployed blockchain protocols are assumed to operate). They proposed a new PoS-based protocol called “Ouroboros Genesis” which enables new or offline parties to safely (re-) join and bootstrap their blockchain from the genesis block without any trusted advice (such as checkpoints) or assumptions regarding past availability. With the model allowing adversarial scheduling of messages in a network with delays and captures the dynamic availability of participants in the worst case, the authors proved the GUC security of Ouroboros Genesis against a fully adaptive adversary controlling less than half of the total stake. Kiffer et al. [16] developed a simple Markov-chain based method for analyzing consistency properties of blockchain protocols. This method could be used to address a number of basic questions about consistency of blockchains such as providing a tighter guarantee on the consistency property of Nakamoto’s protocol, analyzing a family of delaying attacks and extending them to other protocols, giving the first rigorous consistency analysis of GHOST, and so on. Wan et al. [56] presented a novel hybrid consensus protocol named Goshawk, in which a two-layer chain structure with two-level PoW mining strategy and a ticket-voting mechanism are elaborately combined. They showed that Goshawk is the first blockchain protocol with three key properties such as high efficiency, strong robustness against the 51% attack.
Pass et al. [42] proposed a new paradigm called Thunderella for achieving state machine replication by combining a fast, asynchronous path with a (slow) synchronous “fall-back” path. With this paradigm, they provided a new resilient blockchain protocol (for the permissionless setting) assuming only that a majority of the computing power is controlled by honest players, and optimistically, transactions could be confirmed as fast as the actual message delay in the network if 3/4 of the computing power is controlled by honest players, and a special player called the accelerator is honest. Daian et al. [4] presented a provably secure proof-of-stake protocol called Snow White. As a matter of fact, Snow White was publicly released in 2016. It provides a formal, end-to-end proof of a proof-of-stake system in a truly decentralized, open-participation network. The authors identified a core “permissioned” consensus protocol suitable for proof-of-stake, and proposed a robust committee re-election mechanism such that as stake switches hands, the consensus committee can evolve in a timely manner and always reflect the most recent stake distribution. They also introduced a formal treatment of costless simulation issue and gave both upper- and lower-bounds that characterize exactly what setup assumptions are needed to resist costless simulation attacks.
2.2 Related Work
In real-world applications, a separate IDS often has no information about its deployed and protected environment, opening a chance for attackers and cyber-criminals. Due to the lack of contextual information, it becomes very hard for an IDS to figure out complicated attacks. Focus on this issue, there is a great need for building a distributed system or collaborative network to enhance the detection performance [59].
Distributed Systems. Distributed systems have been widely used in various domains over many years. For example, Prras et al. [43] introduced EMERALD (Event Monitoring Enabling Responses to Anomalous Live Disturbances) in 1997, which aimed to monitor malicious behaviors across different layers in a large network. It can model distributed high-volume events and correlate them using traditional IDS techniques. Snapp et al. [46] presented a distributed Intrusion Detection System (DIDS), which could improve the monitoring process with data reduction method and centralized data analysis. Then, COSSACK system [41] was developed to reduce the impact of DDoS attack, which could work without the support and inputs from humans, i.e., it could generate rules and signatures in an automatic way. Then, DOMINO (Distributed Overlay for Monitoring InterNet Outbreaks) [61] was proposed, aiming to enhance the collaboration process among different nodes. They particularly used an overlay design to achieve a heterogeneous, scalable, and robust mechanism. PIER [14] was an Internet-scale query engine and a kind of querying-based system. It could help distribute dataflows and queries in a better way.
Collaborative Intrusion Detection. A collaborative system encourages an IDS node to collect and exchange information with other nodes. Li et al. [18] found that most distributed intrusion detection architectures could not be scalable under different communication mechanisms. Thus, they proposed a distributed detection system by means of a decentralized routing infrastructure. However, one big limitation is that all nodes in their approach should be intra trusted. This may lead to insider attacks, which are one common threat for various distributed systems and collaborative networks.
To protect distributed/collaborative systems against insider attacks, it is very important to design suitable trust mechanisms to measure the reputation in such systems and networks. As an example, an overlay IDS was proposed by Duma et al. [5], which could identify insider attacks. It consists of a trust-aware engine for correlating alarms and an adaptive trust mechanism for handling trust. Then Tuan [53] applied game theory to help enhance the detection performance in a P2P network. They found that if a trust system was not incentive compatible, the more numbers of nodes in the system, the less likely that a malicious node would be identified.
Fung et al. [8] proposed a kind of challenge-based CIDNs, which could evaluate the trustworthiness of an IDS node based on the received answers to the challenges. They first proposed a collaboration framework for host-based IDSs with a forgetting factor, which can emphasize on the recent behavior of a node. To enhance such challenge mechanisms, Li et al. [19] claimed that IDS nodes may have different sensitivity levels in identifying particular intrusions. Then they proposed a concept of intrusion sensitivity (IS) that measures the detection sensitivity of an IDS for a particular intrusion. They also designed an intrusion sensitivity-based trust management model [20] that could automatically allocate the values by using machine learning classifiers like KNN classifier [34]. They also performed a study to investigated the effect of intrusion sensitivity on detecting pollution attacks, where a set of malicious nodes collaborate to affect alert rankings by offering untruthful information [21]. They indicated that IS can help decrease the reputation of malicious nodes quickly. Other related work regarding how to improve the performance of intrusion detection can refer to [6, 7, 30,31,32,33, 36, 37, 57].
Blockchain-Based Intrusion Detection. The application of blockchains in the field of intrusion detection has been studied, but it is still an emerging topic. Alexopoulos et al. [1] described a framework to show how to combine a blockchain with a CIDS. They considered a set of raw alarms produced by each IDS as transactions in a blockchain. Then, all collaborating nodes could use a consensus protocol to ensure the transaction validity before delivering them in a block. This can make sure that the stored alarms are tamper resistant in the blockchain. The major limitation is that they did not provide any results or implementation detail.
Then Meng et al. [38] provided the first review regarding the intersection of blockchains and intrusion detection, and introduced the potential application of such combination. They indicated that blockchains can help enhance an IDS in the aspects of data sharing, trust computation and alarm exchange. For anomaly detection, Golomb et al. [13] described a framework called CIoTA, which could apply blockchains to perform anomaly detection in a distributed manner for IoT devices. By contrast, Li et al. [26] demonstrated how to use blockchains to enhance the performance of collaborative signature-based IDSs via building a verifiable rule database. On the other hand, some studies investigated how an IDS can help protect blockchain applications. Steichen et al. [50] introduced an OpenFlow-based firewall named ChainGuard, which could help protect blockchain-based SDN and identify malicious traffic and behavior in the network.
3 Our Proposed Framework
As discussed above, there are already some studies investigating the intersection of collaborative intrusion detection and blockchains. While most of them (e.g., [1]) focused on a generic CIDS without considering a particular trust mechanism. In practice, the implementation of blockchains may depend on the specific types of trust mechanisms. In this section, we propose a blockchain-based framework for challenge-based CIDNs particularly.
3.1 Framework Design
Figure 2 shows the high-level framework of blockchained challenge-based CIDNs. Under the CIDN, an IDS module is a basic component. There are some more major components: collaboration component, trust management component, P2P communication, and chain component.
-
Collaboration component is mainly responsible for assisting a node in computing the trust values of another node by sending out normal requests or challenges, and receiving the relevant feedback. This component can help a tested node deliver its feedback when receiving a request or challenge. For instance, Fig. 1 shows that when node A sends a request or challenge to node B, it can receive relevant feedback.
-
Trust management component is responsible for evaluating the reputation of other nodes via a specific trust approach. Challenge-based mechanism is a kind of trust approach that computes the trust values through comparing the received feedback with the expected answers. Each node can send out either normal requests or challenges for alert ranking (consultation). To further protect challenges, the original work [8] assumed that challenges should be sent out in a random manner and in a way that makes them difficult to be distinguished from a normal alarm ranking request.
-
P2P communication. This component is responsible for connecting with other IDS nodes and providing network organization, management and communication among IDS nodes.
-
Chain component. This component aims to connect the node with the blockchain, i.e., uploading information, voting and receiving decisions.
Blockchain Layer. This layer makes the framework different from traditional CIDN frameworks, by allowing to establish a consortium blockchain. A separate layer can facilitate the migration from the traditional framework to our blockchain-based framework, without the need of changing the infrastructure much. This framework is also workable under both signature-based and anomaly-based detection. That is, this layer provides an interface for both detection approaches to connect with blockchains. Taking malicious feedback as an example, each chain node can check and share the suspicious feedback to the chain, and other chain nodes can help verify the feedback. This can help either build a trusted rule database [26] or enhanced profile [13].
In such network, every IDS node can select its own partners according to defined policies, and maintain a list called partner list. When a node wants to join the CIDN, it first has to apply and get a unique proof of identity (e.g., a public and a private key pair) via a trusted certificate authority (CA). As depicted in Fig. 1, if node B asks for joining the network, it has to send a request to a CIDN node, say node A. Then, node A makes a decision and sends back an initial partner list, if node C is accepted. A CIDN node can typically send two types of messages: challenge and normal request.
-
A challenge mainly contains a set of IDS alarms, where a testing node can send these alarms to the tested nodes for labeling alarm severity. Because the testing node knows the severity of these alarms in advance, it can judge and compute the satisfaction level for the tested node, based on the received feedback.
-
A normal request is sent by a node for alarm aggregation, which is an important feature of collaborative networks in improving the detection performance of a single detector. The aggregation process usually only considers the feedback from highly trusted nodes. As a response, an IDS node should send back alarm ranking information as their feedback.
3.2 Trust Management
Node Expertise. In this work, we consider three expertise levels for an IDS node as low (0.1), medium (0.5) and high (0.95). The expertise of an IDS can refer to a beta function described as below:
where \(p' (\in [0,1])\) is the probability of intrusion examined by the IDS. \(f(p'|\alpha ,\beta )\) means the probability that a node with expertise level l responses with a value of \(p'\) to an intrusion examination of difficulty level \(d (\in [0,1])\). A higher value of l means a higher probability of correctly identifying an intrusion while a higher value of d means that an intrusion is more difficult to detect. In particular, \(\alpha \) and \(\beta \) can be defined as [9]:
where \(r \in \{0,1\}\) is the expected result of detection. For a fixed difficulty level, the node with higher level of expertise can achieve higher probability of correctly detecting an intrusion. For example, a node with expertise level of 1 can accurately identify an intrusion with guarantee if the difficulty level is 0.
Node Trust Evaluation. To measure the reputation of a target node, a testing node can deliver challenges via a random generation process. Then the testing node can calculate a score to indicate the satisfaction. According to [8], we can evaluate the reputation of a node i according to node j as follows:
where \(F_{k}^{j,i}\in [0,1]\) is the score of the received feedback k and n is the total number of feedback. \(\lambda \) is a forgetting factor that assigns less weight to older feedback response. \(w_{s}\) is a significant weight depending on the total number of received feedback, if there is only a few feedback under a certain minimum m, then \(w_{s}=\frac{\sum _{k=0}^{n} \lambda ^{tk}}{m}\), otherwise \(w_{s}=1\). x is the percentage of “don’t know” answers during a period (e.g., from t0 to tn). d is a positive incentive parameter to control the severity of punishment to “don’t know” replies. More details about equation derivation can be referred to [8].
Satisfaction Evaluation. Intuitively, satisfaction can be measured between an expected feedback (\(e\in [0,1]\)) and an actual received feedback (\(r \in [0, 1]\)). In addition, we can construct a function F (\(\in [0,1]\)) to derive the satisfaction score as follows [8, 9]:


where \(c_{1}\) controls the degree of penalty for wrong estimates and \(c_{2}\) controls satisfaction sensitivity. A larger \(c_{2}\) means more sensitive. In this work, we set \(c_{1}=1.5\) and \(c_{2}=1\) based on the simulation in [9].
In Combination with Blockchains. The blockchained challenge-based CIDN can be treated as a consortium blockchain, as each node should be verified by a CA and get their key pair. It is a key to enhance the robustness of trust computation by measuring the received feedback. In this case, we can submit the received feedback to the chain for verification. If it is not passed, then the feedback can be considered as a suspicious one.
3.3 Alarm Aggregation
Alarm aggregation is a critical process, which can help such collaborative systems make a decision. Intuitively, a node performing the process can request the alarm rankings from other trusted nodes in its partner list. For instance, node j can aggregate the feedback \(R_{j}(a)\) from others, and make a decision, e.g., the aggregated ranking of alert a, by using a weighted majority method as below.
where \(R_{i}(a) (\in [0,1])\) indicates the aggregated ranking of alert a by node i, r means a trust threshold that node j only accepts the alarm ranking from those nodes whose reputation is higher than this threshold. \(T_{i}^{j} (\in [0,1])\) indicates the reputation of node i according to node j. \(D_{i}^{j} (\in [0,1])\) describes how many hops between these two nodes.
In Combination with Blockchains. The alarm aggregation is a critical process in CIDNs, in which an IDS node decides whether there is an intrusion or not. In real-world applications, some malicious nodes may have high reputation at first (e.g., betrayal nodes) and can send untruthful alarm feedback. To avoid the negative impact, the blockchained challenge-based CIDN can submit the received alarm ranking to the chain for validation. If any suspicious clues are found, then the received alarm feedback can be discarded.
4 Evaluation: A Case Study
In this section, as a first study, our purpose is to evaluate the initial performance of our framework in a simulated environment, where malicious nodes could perform an advanced collusion attack, called random poisoning attack [35]. It enables malicious nodes making untruthful feedback with a possibility. In practice, the possibility can be tuned according to the requirements from different environments and networks. The simulated environment contains 50 nodes that are randomly distributed in a \(12\times 12\) grid region. We deployed an IDS, e.g., Snort [49] and Zeek [62] in each node, and all IDS nodes can find their own partners after communicating with others within a time period. The consortium blockchain was deployed in a mid-end computer with Intel(R) Core (TM)i6, CPU 2.5 GHz with 100 GB storage.
To evaluate the trustworthiness of partner nodes, each node can send out challenges randomly to its partners with an average rate of \(\varepsilon \). There are two levels of request frequency: \(\varepsilon _{l}\) and \(\varepsilon _{h}\). For the nodes that have a unclear trust value around the threshold, the frequency should be set as high \(\varepsilon _{h}\). The detailed parameters are shown in Table 1. All the settings are maintained similar to relevant work [8, 20, 24].
Trust Evaluation Under Attack. We randomly selected three expert nodes to perform the random poisoning attack. In particular, a malicious node under random poisoning attack enjoys a possibility of 1/2 in sending out malicious feedback. Figure 3 depicts the reputation of malicious nodes under both traditional framework and our blockchain-based framework.
-
It is observed that the trustworthiness of malicious nodes could be reduced faster under our framework than that under the traditional framework. This is because traditional framework cannot identify all malicious feedback nodes as the malicious nodes only behave untruthfully with a possibility.
-
By contrast, our framework leverages the application of blockchains and each feedback could be verified by all chain nodes. This can greatly increase the successful rate of detecting malicious feedback. Thus, our framework can decrease the reputation of malicious nodes in a fast manner.
Alarm Aggregation Under Attack. Similarly, we also selected three expert nodes randomly to deliver false alarm rankings to a node that performs alarm aggregation. We mainly consider a false negative (FN) rate and a false positive (FP) rate. Figure 4 shows the errors of alarm aggregation under both traditional framework and our framework.
-
It is found that the errors under the traditional framework are generally high with \(FN=33.3\%\) and \(FP=34.8\%\). This is because the traditional framework cannot identify malicious nodes efficiently, e.g., under the random poisoning attack. Therefore, these malicious nodes could still make a negative impact on the alarm aggregation.
-
In the comparison, our framework could reduce the error rates significantly, i.e., with \(FN=10.8\%\) and \(FP=11.9\%\). There are two major reasons. One is that our framework can help identify malicious nodes in a quick manner, e.g., under the random poisoning attack. Also, in our framework, the received alarm rankings can be submitted to the chain for verification, and it is easier to detect untruthful inputs, even from trusted nodes, i.e., betrayal nodes.
Overall, our study indicates that our framework can enhance the robustness of challenge-based CIDNs in the aspects of both trust management and alarm aggregation, through integrating with blockchains.
5 Discussion and Challenges
Though blockchain technology can bring a lot of benefits, it is still at a developing stage, which may suffer many challenges from both inside and outside [38].
-
Energy and cost. The computational power is a concern for blockchain applications in real-world scenarios. For example, Proof of Work (PoW) may require huge amounts of energy while doing bitcoin mining, where the electricity consumption could rise to 7.7 GW by the end of 2018, which is almost half a percent of the world’s electricity consumption.
-
Security and privacy. Though Bitcoin has been widely adopted, it does not mean that it is safe. There are existing some types of attacks. Taking eclipse attack as an example, as the chain nodes have to keep constant communication to compare data, an attacker can fool it into accepting false data if he/she has successfully compromised that node [40]. This results in wasting network resources or accepting fake transactions. There is a need to enhance the security of blockchain itself.
-
Complexity and speed. Blokchain is a complex system that is hard to be established from scratch. A single mistake may cause the whole system to be compromised. Due to the complexity, it also suffers data storage and transaction speed issues. As a study, we only tried a proof-of-concept chain to investigate the performance. It is an important topic to exploit the practical performance when the blockchain runs for a while.
-
Blockchain size. In the beginning of a blockchain, the node number may be in a small scale, which makes it vulnerable to many attacks during the growth. For instance, assume there are only 30 nodes, if a single entity successfully controls just or more than 51% of the blockchain nodes, then it has a high probability to control the whole outputs.
6 Conclusion
Challenge-based Collaborative intrusion detection provides a promising solution to safeguard assets from being compromised; however, it may still be vulnerable to advanced attacks in practical deployment. Motivated by the fast development of blockchains, in this work, we propose a blockchained challenge-based CIDN framework by leveraging the benefits offered by the blockchain technology. Our framework enables nodes to form a consortium chain and improve the robustness of challenge-based CIDNs. In the evaluation, our results demonstrate that our framework can enhance the robustness in the aspects of trust management by detecting advanced malicious nodes, and alarm aggregation through identifying untruthful inputs and reducing error rates.
References
Alexopoulos, N., Vasilomanolakis, E., Ivánkó, N.R., Mühlhäuser, M.: Towards blockchain-based collaborative intrusion detection systems. In: D’Agostino, G., Scala, A. (eds.) CRITIS 2017. LNCS, vol. 10707, pp. 107–118. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-99843-5_10
Amazon Managed Blockchain: Easily create and manage scalable blockchain networks. https://aws.amazon.com/managed-blockchain/. Accessed 10 Apr 2019
Badertscher, C., Gazi, P., Kiayias, A., Russell, A., Zikas, V.: Ouroboros genesis: composable proof-of-stake blockchains with dynamic availability. In: Proceedings of ACM Conference on Computer and Communications Security (CCS), pp. 913–930 (2018)
Daian, P., Pass, R., Shi, E.: Snow white: robustly reconfigurable consensus and applications to provably secure proofs of stake. In: Financial Cryptography and Data Security (FC) (2019)
Duma, C., Karresand, M., Shahmehri, N., Caronni, G.: A trust-aware, P2P-based overlay for intrusion detection. In: DEXA Workshop, pp. 692–697 (2006)
Fadlullah, Z.M., Taleb, T., Vasilakos, A.V., Guizani, M., Kato, N.: DTRAB: combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Trans. Netw. 18(4), 1234–1247 (2010)
Friedberg, I., Skopik, F., Settanni, G., Fiedler, R.: Combating advanced persistent threats: from network event correlation to incident detection. Comput. Secur. 48, 35–47 (2015)
Fung, C.J., Baysal, O., Zhang, J., Aib, I., Boutaba, R.: Trust management for host-based collaborative intrusion detection. In: De Turck, F., Kellerer, W., Kormentzas, G. (eds.) DSOM 2008. LNCS, vol. 5273, pp. 109–122. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-87353-2_9
Fung, C.J., Zhu, Q., Boutaba, R., Basar, T.: Bayesian decision aggregation in collaborative intrusion detection networks. In: NOMS, pp. 349–356 (2010)
Almost half of companies still can’t detect IoT device breaches, reveals Gemalto study. https://www.gemalto.com/press/Pages/Almost-half-of-companies-still-can-t-detect-IoT-device-breaches-reveals-Gemalto-study.aspx. Accessed 10 Apr 2019
Leading the IoT: Gartner Insights on How to Lead in a Connected World. https://www.gartner.com/imagesrv/books/iot/iotEbook_digital.pdf. Accessed 22 Mar 2019
Gartner Identifies Top 10 Strategic IoT Technologies and Trends. https://www.gartner.com/en/newsroom/press-releases/2018-11-07-gartner-identifies-top-10-strategic-iot-technologies-and-trends. Accessed 22 Mar 2019
Golomb, T., Mirsky, Y., Elovici, Y.: CIoTA: Collaborative IoT Anomaly detection via blockchain. In: Proceedings of Workshop on Decentralized IoT Security and Standards (DISS), pp. 1–6 (2018)
Huebsch, R., et al.: The architecture of PIER: an internet-scale query processor. In: Proceedings of the 2005 Conference on Innovative Data Systems Research (CIDR), pp. 28–43 (2005)
Hyperledger C Open Source Blockchain Technologies. https://www.hyperledger.org/
Kiffer, L., Rajaraman, R., Shelat, A.: A better method to analyze blockchain consistency. In: Proceedings of ACM Conference on Computer and Communications Security (CCS), pp. 729–744 (2018)
Lei, A., Cruickshank, H.S., Cao, Y., Asuquo, P.M., Ogah, C.P.A., Sun, Z.: Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 4(6), 1832–1843 (2017)
Li, Z., Chen, Y., Beach, A.: Towards scalable and robust distributed intrusion alert fusion with good load balancing. In: Proceedings of the 2006 SIGCOMM Workshop on Large-Scale Attack Defense (LSAD), pp. 115–122 (2006)
Li, W., Meng, Y., Kwok, L.-F.: Enhancing trust evaluation using intrusion sensitivity in collaborative intrusion detection networks: feasibility and challenges. In: Proceedings of the 9th International Conference on Computational Intelligence and Security (CIS), pp. 518–522. IEEE (2013)
Li, W., Meng, W., Kwok, L.-F.: Design of intrusion sensitivity-based trust management model for collaborative intrusion detection networks. In: Zhou, J., Gal-Oz, N., Zhang, J., Gudes, E. (eds.) IFIPTM 2014. IAICT, vol. 430, pp. 61–76. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-43813-8_5
Li, W., Meng, W.: Enhancing collaborative intrusion detection networks using intrusion sensitivity in detecting pollution attacks. Inf. Comput. Secur. 24(3), 265–276 (2016)
Li, L., et al.: CreditCoin: a privacy-preserving blockchain-based incentive announcement network for communications of smart vehicles. IEEE Trans. Intell. Transp. Syst. 19(7), 2204–2220 (2018)
Li, W., Meng, W., Kwok, L.-F., Ip, H.H.S.: PMFA: toward passive message fingerprint attacks on challenge-based collaborative intrusion detection networks. In: Chen, J., Piuri, V., Su, C., Yung, M. (eds.) NSS 2016. LNCS, vol. 9955, pp. 433–449. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-46298-1_28
Li, W., Meng, W., Kwok, L.-F.: SOOA: exploring special on-off attacks on challenge-based collaborative intrusion detection networks. In: Au, M.H.A., Castiglione, A., Choo, K.-K.R., Palmieri, F., Li, K.-C. (eds.) GPC 2017. LNCS, vol. 10232, pp. 402–415. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-57186-7_30
Li, W., Meng, W., Kwok, L.-F.: Investigating the influence of special on-off attacks on challenge-based collaborative intrusion detection networks. Future Internet 10(1), 1–16 (2018)
Li, W., Tug, S., Meng, W., Wang, Y.: Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener. Comput. Syst. 96, 481–489 (2019)
Li, W., Kwok, L.-F.: Challenge-based collaborative intrusion detection networks under passive message fingerprint attack: a further analysis. J. Inf. Secur. Appl. 47, 1–7 (2019)
Makhdoom, I., Abolhasan, M., Abbas, H., Ni, W.: Blockchain’s adoption in IoT: the challenges, and a way forward. J. Netw. Comput. Appl. 125, 251–279 (2019)
Marr, B.: 5 Blockchain Trends Everyone Should Know About. https://www.forbes.com/sites/bernardmarr/2019/01/28/5-blockchain-trends-everyone-should-know-about/#30c1ab523bb9. Accessed 10 Apr 2019
Meng, Y., Kwok, L.F.: Enhancing false alarm reduction using voted ensemble selection in intrusion detection. Int. J. Comput. Intell. Syst. 6(4), 626–638 (2013)
Meng, Y., Li, W., Kwok, L.F.: Towards adaptive character frequency-based exclusive signature matching scheme and its applications in distributed intrusion detection. Comput. Netw. 57(17), 3630–3640 (2013)
Meng, W., Li, W., Kwok, L.-F.: An evaluation of single character frequency-based exclusive signature matching in distinct IDS environments. In: Chow, S.S.M., Camenisch, J., Hui, L.C.K., Yiu, S.M. (eds.) ISC 2014. LNCS, vol. 8783, pp. 465–476. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-13257-0_29
Meng, W., Li, W., Kwok, L.-F.: EFM: enhancing the performance of signature-based network intrusion detection systems using enhanced filter mechanism. Comput. Secur. 43, 189–204 (2014)
Meng, W., Li, W., Kwok, L.-F.: Design of intelligent KNN-based alarm filter using knowledge-based alert verification in intrusion detection. Secur. Commun. Netw. 8(18), 3883–3895 (2015)
Meng, W., Luo, X., Li, W., Li, Y.: Design and evaluation of advanced collusion attacks on collaborative intrusion detection networks in practice. In: Proceedings of the 15th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2016), pp. 1061–1068 (2016)
Meng, W., Li, W., Xiang, Y., Choo, K.K.R.: A Bayesian inference-based detection mechanism to defend medical smartphone networks against insider attacks. J. Netw. Comput. Appl. 78, 162–169 (2017)
Meng, W., Li, W., Kwok, L.-F.: Towards effective trust-based packet filtering in collaborative network environments. IEEE Trans. Netw. Serv. Manag. 14(1), 233–245 (2017)
Meng, W., Tischhauser, E.W., Wang, Q., Wang, Y., Han, J.: When intrusion detection meets blockchain technology: a review. IEEE Access 6(1), 10179–10188 (2018)
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system (2008). http://bitcoin.org/bitcoin.pdf
Orcutt, M.: How secure is blockchain really? https://www.technologyreview.com/s/610836/how-secure-is-blockchain-really/. Accessed 22 Mar 2019
Papadopoulos, C., Lindell, R., Mehringer, J., Hussain, A., Govindan, R.: COSSACK: coordinated suppression of simultaneous attacks. In: Proceedings of the 2003 DARPA Information Survivability Conference and Exposition (DISCEX), pp. 94–96 (2003)
Pass, R., Shi, E.: Thunderella: blockchains with optimistic instant confirmation. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018. LNCS, vol. 10821, pp. 3–33. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78375-8_1
Porras, P.A., Neumann, P.G.: EMERALD: event monitoring enabling responses to anomalous live disturbances. In: Proceedings of the 20th National Information Systems Security Conference, pp. 353–365 (1997)
Roesch, M.: Snort: lightweight intrusion detection for networks. In: Proceedings of USENIX Lisa Conference, pp. 229–238 (1999)
Scarfone, K., Mell, P.: Guide to intrusion detection and prevention systems (IDPS). NIST Special Publication 800-94 (2007)
Snapp, S.R., et al.: DIDS (distributed intrusion detection system) - motivation, architecture, and an early prototype. In: Proceedings of the 14th National Computer Security Conference, pp. 167–176 (1991)
Sharma, V.: An energy-efficient transaction model for the blockchain-enabled internet of vehicles (IoV). IEEE Commun. Lett. 23(2), 246–249 (2019)
Singh, S., Ra, I.H., Meng, W., Kaur, M., Cho, G.H.: SH-BlockCC: a secure and efficient IoT smart home architecture based on cloud computing and blockchain technology. Int. J. Distrib. Sens. Netw. (in press). SAGE
Snort: An an open source network intrusion prevention and detection system (IDS/IPS). http://www.snort.org/
Steichen, M., Hommes, S., State, R.: ChainGuard - a firewall for blockchain applications using SDN with OpenFlow. In: Proceedings of International Conference on Principles, Systems and Applications of IP Telecommunications (IPTComm), pp. 1–8 (2017)
Symantec 2019 Internet Security Threat Report. https://www.symantec.com/security-center/threat-report. Accessed 22 Mar 2019
Tug, S., Meng, W., Wang, Y.: CBSigIDS: towards collaborative blockchained signature-based intrusion detection. In: Proceedings of The 1st IEEE International Conference on Blockchain (Blockchain) (2018)
Tuan, T.A.: A game-theoretic analysis of trust management in P2P systems. In: Proceedings of ICCE, pp. 130–134 (2006)
Vasilomanolakis, E., Karuppayah, S., Muhlhauser, M., Fischer, M.: Taxonomy and survey of collaborative intrusion detection. ACM Comput. Surv. 47(4), 55:1–55:33 (2015)
Vigna, G., Kemmerer, R.A.: NetSTAT: a network-based intrusion detection approach. In: Proceedings of Annual Computer Security Applications Conference (ACSAC), pp. 25–34 (1998)
Wan, C., et al.: Goshawk: a novel efficient, robust and flexible blockchain protocol. In: Guo, F., Huang, X., Yung, M. (eds.) Inscrypt 2018. LNCS, vol. 11449, pp. 49–69. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-14234-6_3
Wang, Y., Meng, W., Li, W., Liu, Z., Liu, Y., Xue, H.: Adaptive machine learning-based alarm reduction via edge computing for distributed intrusion detection systems. Concurr. Comput. Pract. Exp. (2019). https://doi.org/10.1002/cpe.5101
Wood, G.: Ethereum: a secure decentralised generalised transaction ledger. EIP-150 Revision (2016)
Wu, Y.-S., Foo, B., Mei, Y., Bagchi, S.: Collaborative intrusion detection system (CIDS): a framework for accurate and efficient IDS. In: Proceedings of the 2003 Annual Computer Security Applications Conference (ACSAC), pp. 234–244 (2003)
Wüst, K., Gervais, A.: Do you need a blockchain? In: CVCBT, pp. 45–54 (2018)
Yegneswaran, V., Barford, P., Jha, S.: Global Intrusion Detection in the DOMINO Overlay System. In: Proceedings of the 2004 Network and Distributed System Security Symposium (NDSS), pp. 1–17 (2004)
The Zeek Network Security Monitor. https://www.zeek.org/
Acknowledgments
This work was funded by the National Natural Science Foundation of China (NSFC) Grant No. 61772148, 61802080 and 61802077.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Li, W., Wang, Y., Li, J., Au, M.H. (2019). Towards Blockchained Challenge-Based Collaborative Intrusion Detection. In: Zhou, J., et al. Applied Cryptography and Network Security Workshops. ACNS 2019. Lecture Notes in Computer Science(), vol 11605. Springer, Cham. https://doi.org/10.1007/978-3-030-29729-9_7
Download citation
DOI: https://doi.org/10.1007/978-3-030-29729-9_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-29728-2
Online ISBN: 978-3-030-29729-9
eBook Packages: Computer ScienceComputer Science (R0)