Abstract
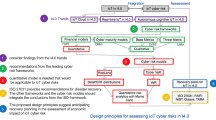
We developed the mechanism of assessing cyber risks for Internet of Things (IoT) projects. The relevance of this topic is explained by growing sophistication of cyber-attacks, the speed of new threats emergence and increasing damage from the attacks. The paper addresses decreasing efficiencies of existing mechanisms of cyber risk assessment and fills the research gaps in this area. Results include development of the mechanism’s concept, its block diagram, the specification and description of its comprising tools and the case study. Unlike peers, the mechanism provided holistic approach to cyber risk assessment; integrated and coordinated all related activities and tools. It simulated the confidence interval of project return on investments (ROI) and showing the chances to go above risk appetite. It makes cyber risk assessment dynamic, iterative, responsive to changes in cyber environment. These advantages let us conclude that the mechanism should have a significant scientific and practical use.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Abomhara, M., Koien, G.: Cyber security and internet of things: vulnerabilities, threats, intruders and attacks. J. Cyber Secur. 4, 65–68 (2015)
Deloitte Inside. The Internet of Things. A technical primer (2018). https://www2.deloitte.com/insights/us/en/focus/Internet of Things/technical-primer.html. Accessed 2 Mar 2019
Glukhov, V., Balashova, E.: Economics and Management in Info-Communication: Tutorial. Piter SPb, St. Petersburg (2012)
Grichounine, S.: Developing the mechanism of qualitative risk assessment in strategic controlling. SPbSPU J. Econ. 10(2), 64–74 (2017)
Radanliev, P., et al.: Future developments in cyber risk assessment for the Internet of things. Comput. Ind. 102, 14–22 (2018)
Ralston, P.A.S., Graham, J.H., Hieb, J.L.: Cyber security risk assessment for SCADA and DCS networks. ISA Trans. 46, 583–594 (2007)
Cherdantseva, Y., Burnap, P., et al.: A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 56, 1–27 (2016)
Nurse, S., Greese, S., De Roure, D.C.: Security risk assessment in internet of things systems. IT Prof. 19(5), 20–26 (2017)
Grishunin, S., Mukhanova, N., Suloeva, S.: Development of concept of risk controlling for industrial enterprise. Organ. Prod. 26(1), 45–46 (2018)
Antonucci, D.: The cyber risk handbook: creating and measuring effective cyber-security capabilities. Wiley, Hoboken (2017)
Filko, S., Filko, I.: Risk Controlling of Information Security. Accounting, Analysis and Audit: Theoretical and Practical Problems. SSAU 16, pp. 123–127 (2016)
ISO/IEC 27005:2013.: Information technology - security techniques - information security risk management. International Organization for Standardization (2005)
Abie, H., Balashingham, I: Risk-based adaptive security for smart IoT in e-health. In: Proceedings of the 7th Conference on Body Area Networks, Oslo, pp. 269–275 (2002)
Caralli, R., Stevens, J., Young, L., Wilson, W.: Introducing OCTAVE: Improving the Information Security Risk Assessment Process. Hansom AFB, MA (2007)
Wynn, J., et al.: Threat assessment and remediation analysis methodology, Bedford (2011)
Thomas, P., Bickel, J., Bratvold, R.: The risk of using risk matrices. SPE Econ. Manag. 6, 56–66 (2013)
Gusmao, A., Poleto, T., Silva, M., Silva, L.: Cybersecurity risk analysis model using fault tree analysis and fuzzy decision theory. Int. J. Inf. Manag. 43(6), 248–260 (2018)
Hubbard, D., Seiersen, R.: How to measure Anything in Cybersecurity Risk. Wiley, Hoboken (2016)
Grishunin, S., Suloeva, S., NekrasovaT, T.: Development of the mechanism of risk-adjusted scheduling and cost budgeting of R&D projects in telecommunications. In: Galinina, O., Andreev, S., Balandin, S., Koucheryavy, Y. (eds.) NEW2AN 2018, ruSMART 2018. LNCS, vol. 11118, pp. 456–470. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-01168-0_41
Framework for improving critical infrastructure cybersecurity. National Institute of Standards and Technology (2018)
Kotenko, I., Chechulin, A.: A cyber attack modeling and impact assessment framework. In: 5th Conference on Cyber Conflict Proceedings, pp. 1–24. IEEE, Tallinn (2013)
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Grishunin, S., Suloeva, S., Nekrasova, T., Egorova, A. (2019). Development of the Mechanism of Assessing Cyber Risks in the Internet of Things Projects. In: Galinina, O., Andreev, S., Balandin, S., Koucheryavy, Y. (eds) Internet of Things, Smart Spaces, and Next Generation Networks and Systems. NEW2AN ruSMART 2019 2019. Lecture Notes in Computer Science(), vol 11660. Springer, Cham. https://doi.org/10.1007/978-3-030-30859-9_41
Download citation
DOI: https://doi.org/10.1007/978-3-030-30859-9_41
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-30858-2
Online ISBN: 978-3-030-30859-9
eBook Packages: Computer ScienceComputer Science (R0)