Abstract
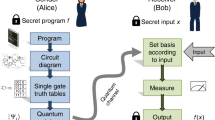
A one-time program (OTP) works as follows: Alice provides Bob with the implementation of some function. Bob can have the function evaluated exclusively on a single input of his choosing. Once executed, the program will fail to evaluate on any other input. State-of-the-art one-time programs have remained theoretical, requiring custom hardware that is cost-ineffective/unavailable, or confined to ad-hoc/unrealistic assumptions. To bridge this gap, we explore how the Trusted Execution Environment (TEE) of modern CPUs can realize the OTP functionality. Specifically, we build two flavours of such a system: in the first, the TEE directly enforces the one-timeness of the program; in the second, the program is represented with a garbled circuit and the TEE ensures Bob’s input can only be wired into the circuit once, equivalent to a smaller cryptographic primitive called one-time memory. These have different performance profiles: the first is best when Alice’s input is small and Bob’s is large, and the second for the converse.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Hazay and Lindell [19] give a thorough treatment of interactive two-party protocols.
- 2.
As an example, Intel STK2mv64CC, a Compute Stick that supports both TXT and TPM, was priced at $499.95 USD on Amazon.com (as of September 2018).
- 3.
A state-bound cryptographic operation performed by the TPM chip, like encryption.
- 4.
Essentially, one would define a very general function we might call \(\mathsf {Apply}\) that will execute the first input variable on the second: \(y=\mathsf {Apply}(f,b)=f(b)\). Since f is now Alice’s private input, it is hidden. The implementation of \(\mathsf {Apply}\) might be a universal circuit where f defines the gates’ logic—in this case \(\mathsf {Apply}\) would leak (an upper-bound on) the circuit size of f but otherwise keep f private.
- 5.
We consider various TEEs and justify this choice in the full version of our paper.
- 6.
A flag is more straightforward to implement than a TPM monotonic counter, thanks to the PCR-bound NVRAM sealing, whereas a counter would involve extra steps (such as attesting to the counterAuth password).
- 7.
Unselected keys remain sealed, if never unsealed it serves as cryptographic deletion.
- 8.
The wire program may be written and compiled on a separate machine from that which will be shipped to Bob. If Alice chooses to use the same machine, the (no longer needed) raw wire code and Frigate executable should be removed from the box before provisioning continues.
- 9.
Similarly, we can also list the SNPs for BRCA2 and determine the contribution of the observed SNPs to the total risk factor.
- 10.
This can easily be adjusted, but is accompanied by substantial changes in the resulting circuit size. For example, an 11 GB circuit that outputs 16 bits grows to 18 GB by doubling the output size to 32 bits. We conservatively choose 16 bits for demonstration purposes, but the output size may be reduced as appropriate.
- 11.
We use a second disk to simulate what is shipped to the client (with all test data consolidated), separate from our primary disk for development.
- 12.
Another option would have been to upgrade the memory of the initial evaluation machine, but we chose to forgo this, as a test run on the server-class machine revealed that upwards of 60 GB would be required (not supportable by the motherboard).
References
Ayday, E., Raisaro, J.L., Laren, M., Jack, P., Fellay, J., Hubaux, J.P.: Privacy-preserving computation of disease risk by using genomic, clinical, and environmental data. In: Proceedings of USENIX Security Workshop on Health Information Technologies (HealthTech 2013). No. EPFL-CONF-187118 (2013)
Baldi, P., Baronio, R., De Cristofaro, E., Gasti, P., Tsudik, G.: Countering gattaca: efficient and secure testing of fully-sequenced human genomes. In: Proceedings of the 18th ACM CCS 2011, pp. 691–702 (2011)
Bellare, M., Hoang, V.T., Rogaway, P.: Adaptively secure garbling with applications to one-time programs and secure outsourcing. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 134–153. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34961-4_10
Brasser, F., Müller, U., Dmitrienko, A., Kostiainen, K., Capkun, S., Sadeghi, A.R.: Software grand exposure: SGX cache attacks are practical. In: 11th USENIX Workshop on Offensive Technologies (WOOT 2017), Vancouver, BC (2017)
Broadbent, A., Gutoski, G., Stebila, D.: Quantum one-time programs. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8043, pp. 344–360. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40084-1_20
Bulck, J.V., et al.: Foreshadow: extracting the keys to the Intel SGX kingdom with transient out-of-order execution. In: USENIX Security Symposium, Baltimore, MD, USA, pp. 991–1008 (2018)
Canim, M., Kantarcioglu, M., Malin, B.: Secure management of biomedical data with cryptographic hardware. IEEE Trans. Inf Technol. Biomed. 16(1), 166–175 (2012)
Cariaso, M., Lennon, G.: SNPedia: a wiki supporting personal genome annotation, interpretation and analysis (2010). http://www.SNPedia.com
Chor, B., Goldreich, O., Kushilevitz, E., Sudan, M.: Private information retrieval. In: Proceedings of the 36th Annual Symposium on Foundations of Computer Science, pp. 41–50. IEEE (1995)
Fisch, B.A., Vinayagamurthy, D., Boneh, D., Gorbunov, S.: Iron: functional encryption using Intel SGX. Technical report, IACR eprint (2016)
Gnu.org: The multiboot specification (2009). http://www.gnu.org/software/grub/manual/multiboot/multiboot.html
Goldwasser, S., Kalai, Y.T., Rothblum, G.N.: One-time programs. In: Wagner, D. (ed.) CRYPTO 2008. LNCS, vol. 5157, pp. 39–56. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85174-5_3
Greene, J.: Intel® trusted execution technology. Technical report (2012)
Greshake, B., Bayer, P.E., Rausch, H., Reda, J.: Opensnp-a crowdsourced web resource for personal genomics. PLoS ONE 9(3), 1–9 (2014)
Guan, L., Lin, J., Luo, B., Jing, J.: Copker: computing with private keys without RAM. In: NDSS, San Diego, CA, USA, February 2014
Gunupudi, V., Tate, S.R.: Generalized non-interactive oblivious transfer using count-limited objects with applications to secure mobile agents. In: Tsudik, G. (ed.) FC 2008. LNCS, vol. 5143, pp. 98–112. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85230-8_8
Halderman, J.A., et al.: Lest we remember: cold boot attacks on encryption keys. In: USENIX Sec 2008, San Jose, CA, USA (2008)
Han, S., Shin, W., Park, J.H., Kim, H.: A bad dream: subverting trusted platform module while you are sleeping. In: 27th USENIX Security Symposium (USENIX Security 2018), Baltimore, MD, USA, pp. 1229–1246 (2018)
Hazay, C., Lindell, Y.: Efficient Secure Two-Party Protocols. ISC. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14303-8
Intel Corporation: Trusted boot (tboot), version: 1.8.0 (2017). http://tboot.sourceforge.net/
Järvinen, K., Kolesnikov, V., Sadeghi, A.-R., Schneider, T.: Garbled circuits for leakage-resilience: hardware implementation and evaluation of one-time programs. In: Mangard, S., Standaert, F.-X. (eds.) CHES 2010. LNCS, vol. 6225, pp. 383–397. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-15031-9_26
Jefferies, C.P.: How to identify user-upgradeable notebooks, June 2017. http://www.notebookreview.com/feature/identify-user-upgradeable-notebooks/
Kantarcioglu, M., Jiang, W., Liu, Y., Malin, B.: A cryptographic approach to securely share and query genomic sequences. IEEE Trans. Inf Technol. Biomed. 12(5), 606–617 (2008)
Kirkpatrick, M.S., Kerr, S., Bertino, E.: PUF ROKs: a hardware approach to read-once keys. In: Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, AsiaCCS 2011, Hong Kong, China, pp. 155–164 (2011)
Kitamura, T., Shinagawa, K., Nishide, T., Okamoto, E.: One-time programs with cloud storage and its application to electronic money. In: APKC (2017)
Kocher, P., et al.: Spectre attacks: exploiting speculative execution. CoRR (2018)
Kollenda, B., Koppe, P., Fyrbiak, M., Kison, C., Paar, C., Holz, T.: An exploratory analysis of microcode as a building block for system defenses. In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS 2018, Toronto, ON, Canada, 15–19 October 2018, pp. 1649–1666 (2018)
Koppe, P., et al.: Reverse engineering x86 processor microcode. In: 26th USENIX Security Symposium (USENIX Security 2017), Vancouver, BC, pp. 1163–1180 (2017)
Lee, S., Shih, M.W., Gera, P., Kim, T., Kim, H., Peinado, M.: Inferring fine-grained control flow inside SGX enclaves with branch shadowing. In: 26th USENIX Security Symposium (USENIX Security 2017), Vancouver, BC, pp. 557–574 (2017)
Lipp, M., et al.: Meltdown. CoRR (2018)
McCune, J.M.: Reducing the trusted computing base for applications on commodity systems. Ph.D. thesis, Carnegie Mellon University (2009)
Mood, B., Gupta, D., Carter, H., Butler, K., Traynor, P.: Frigate: a validated, extensible, and efficient compiler and interpreter for secure computation. In: Euro-SP (2016)
Müller, T., Freiling, F.C., Dewald, A.: TRESOR runs encryption securely outside RAM. In: USENIX Security Symposium, San Francisco, CA, USA, August 2011
Naveed, M., et al.: Controlled functional encryption. In: CCS 2014, pp. 1280–1291. ACM (2014)
Naveed, M., et al.: Privacy and security in the genomic era. In: CCS 2014 (2014)
nccgroup: Cachegrab, December 2017. https://github.com/nccgroup/cachegrab
Saint-Jean, F.: Java implementation of a single-database computationally symmetric private information retrieval (cSPIR) protocol. Technical report, Yale University Department of Computer Science (2005)
Sevinsky, R.: Funderbolt: Adventures in Thunderbolt DMA Attacks. Black Hat USA (2013)
Simmons, P.: Security through Amnesia: a software-based solution to the cold boot attack on disk encryption. In: ACSAC (2011)
Sottek, T.: NSA reportedly intercepting laptops purchased online to install spy malware, December 2013. https://www.theverge.com/2013/12/29/5253226/nsa-cia-fbi-laptop-usb-plant-spy
Strackx, R., Jacobs, B., Piessens, F.: ICE: a passive, high-speed, state-continuity scheme. In: Proceedings of the 30th Annual Computer Security Applications Conference, ACSAC 2014, New Orleans, Louisiana, USA, pp. 106–115 (2014)
Strackx, R., Piessens, F.: Ariadne: a minimal approach to state continuity. In: 25th USENIX Security Symposium (USENIX Sec 2016), Austin, TX, pp. 875–892 (2016)
Tarnovsky, C.: Attacking TPM part 2: a look at the ST19WP18 TPM device, July 2012. dEFCON presentation. https://www.defcon.org/html/links/dc-archives/dc-20-archive.html
Trusted Computing Group: TCG Platform Reset Attack Mitigation Specification, May 2008
Trusted Computing Group: Trusted Platform Module Main Specification, version 1.2, revision 116 (2011). https://trustedcomputinggroup.org/tpm-main-specification/
Vasiliadis, G., Athanasopoulos, E., Polychronakis, M., Ioannidis, S.: PixelVault: using GPUs for securing cryptographic operations. In: CCS 2014, Scottsdale, AZ, USA, November 2014
Vidas, T.: Volatile memory acquisition via warm boot memory survivability. In: 43rd Hawaii International Conference on System Sciences, pp. 1–6, January 2010
Walsh, T., et al.: Detection of inherited mutations for breast and ovarian cancer using genomic capture and massively parallel sequencing. Natl Acad. Sci. 107(28), 12629–12633 (2010)
Wang, X.S., Huang, Y., Zhao, Y., Tang, H., Wang, X., Bu, D.: Efficient genome-wide, privacy-preserving similar patient query based on private edit distance. In: CCS, pp. 492–503. ACM (2015)
Yao, A.C.: Protocols for secure computations. In: FOCS (1982)
Zhang, N., Sun, K., Shands, D., Lou, W., Hou, Y.T.: Truspy: cache side-channel information leakage from the secure world on ARM devices. IACR Cryptology ePrint Archive 2016, 980 (2016)
Zhao, L., et al.: One-time programs made practical (2019). http://arxiv.org/abs/1907.00935
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Appendix
A Appendix
For space considerations, we also publish a full version [52] of this paper that provides additional information as follows:
-
More background helpful for understanding on one-time programs, garbled circuits, and one-time memories;
-
Discussion of an adaptive security attack on OTP systems;
-
Detailed modifications we make to Battleship;
-
Preprocessing steps for our case study application;
-
Additional one-time program use cases;
-
A list of the SNPs associated with BRCA1;
-
Details of our genomic algorithm;
-
Comments on porting efforts required for OTP; and
-
Discussion of more attacks (e.g., SMM and TPM relay attacks).
Rights and permissions
Copyright information
© 2019 International Financial Cryptography Association
About this paper
Cite this paper
Zhao, L. et al. (2019). One-Time Programs Made Practical. In: Goldberg, I., Moore, T. (eds) Financial Cryptography and Data Security. FC 2019. Lecture Notes in Computer Science(), vol 11598. Springer, Cham. https://doi.org/10.1007/978-3-030-32101-7_37
Download citation
DOI: https://doi.org/10.1007/978-3-030-32101-7_37
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-32100-0
Online ISBN: 978-3-030-32101-7
eBook Packages: Computer ScienceComputer Science (R0)