Abstract
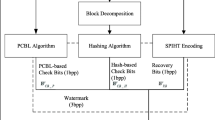
Due to the powerful image editing tools, image integrity protection is becoming important, for instance, in a court of law, news reports, insurance claims or telemedicine. Digital image watermarking is a technique for detecting, localizing and recovering of tampered image but capability and accuracy of performance by the existing methods are still issues especially when tampering rate is relatively high. This paper proposes a novel blind fragile watermarking mechanism for effective image authentication and recovery. In the proposed scheme, not only the probability of detection and localization of tampering is increased because of embedding appropriate authentication code in the proper position but also there is an efficient post-processing of recovery in a way that any pixel has treated differently leading to higher quality of recovered image. Furthermore, embedding more fragile authentication code with a smaller number of bits can help to provide a second opportunity for content recovery while the quality of watermarked image is preserved. Thus, better results have been achieved in terms of accuracy of detection and the quality of recovered image after higher tampering rate compared with some of the state-of-the-art schemes.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Liu, X.-L., Lin, C.-C., Yuan, S.-M.: Blind dual watermarking for color images’ authentication and copyright protection. IEEE Trans. Circ. Syst. Video Technol. 28(5), 1047–1055 (2018)
Wang, N., Cheng, X., Li, Z., Chen, Y.: Dual watermarking algorithm based on singular value decomposition and compressive sensing. In: IEEE 17th International Conference on Communication Technology (ICCT), pp. 1763–1767 (2017)
Qin, C., Ji, P., Zhang, X., Dong, J., Wang, J.: Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Sig. Process. 138, 280–293 (2017)
Dole, V.S., Patil, N.N.: Self-embedding fragile watermarking for image tampering detection and image recovery using self recovery blocks. In: IEEE International Conference on Computing Communication Control and Automation, (ICCUBEA) (2015)
Sing, D., Sing, S.K.: Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J. Vis. Commun. Image Represent. 38, 775–789 (2016)
Shehab, M., et al.: Secure and robust fragile watermarking scheme for medical images. IEEE Access 6, 10269–10278 (2018)
Hsu, C.-S., Tu, S.-F.: Image tamper detection and recovery using adaptive embedding rules. Measurement 88, 287–296 (2016)
Haghighi, B.B., Taherinia, A.H.: TRLH: fragile and blind dual watermarking for image tamper detection and self-recovery based on lifting wavelet transform and half toning technique. J. Vis. Commun. Image Represent. 50, 49–64 (2018)
Tai, W.L., Liao, Z.J.: Image self-recovery with watermark self-embedding. In: IEEE International Conference on Signal Processing, Signal Processing: Image Communication, vol. 65, pp. 11–25, July 2018
Kim, C., Shin, D., Yang, C.-N.: Self-embedding fragile watermarking scheme to restoration of a tampered image using AMBTC. Pers. Ubiquit. Comput. 22(1), 11–22 (2018)
Qin, C., Ji, P., Chang, C.-C., Dong, J., Sun, X.: Non-uniform watermark sharing based on optimal iterative BTC for image tampering recovery. IEEE Multimedia 25, 36–48 (2018)
Rakhmawati, L., Wirawan, W., Suwadi, S.: A recent survey of self-embedding fragile watermarking scheme for image authentication with recovery capability. EURASIP J. Image Video Process. 2019, 1–22 (2019)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Tohidi, F., Paul, M., Hooshmandasl, M.R., Debnath, T., Jamshidi, H. (2019). Efficient Self-embedding Data Hiding for Image Integrity Verification with Pixel-Wise Recovery Capability. In: Lee, C., Su, Z., Sugimoto, A. (eds) Image and Video Technology. PSIVT 2019. Lecture Notes in Computer Science(), vol 11854. Springer, Cham. https://doi.org/10.1007/978-3-030-34879-3_11
Download citation
DOI: https://doi.org/10.1007/978-3-030-34879-3_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-34878-6
Online ISBN: 978-3-030-34879-3
eBook Packages: Computer ScienceComputer Science (R0)