Abstract
 is one of the round-1 candidates in the ongoing NIST Lightweight Cryptography standardization project and an evolution of the previously published
is one of the round-1 candidates in the ongoing NIST Lightweight Cryptography standardization project and an evolution of the previously published
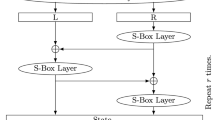
 scheme. For each data block, the mode performs multiple calls to a permutation in an Even-Mansour construction. The designers argue that the mode permits using a permutation with slightly suboptimal properties in order to increase performance, such as allowing differential distinguishers which cannot be extended to attacks on the full construction.
scheme. For each data block, the mode performs multiple calls to a permutation in an Even-Mansour construction. The designers argue that the mode permits using a permutation with slightly suboptimal properties in order to increase performance, such as allowing differential distinguishers which cannot be extended to attacks on the full construction.
We first show that this claim is incorrect since differences can not only be introduced via the processed data, but also via the mode’s control flow. Second, by exploiting a strong differential clustering effect in the permutation, we propose several forgery attacks on
 with complexity less than the security bound given by the designers, such as a block reordering attack on full
with complexity less than the security bound given by the designers, such as a block reordering attack on full
 with estimated success probability about \(2^{-54}\). Additionally, we discuss some trivial forgeries and point out domain separation issues.
with estimated success probability about \(2^{-54}\). Additionally, we discuss some trivial forgeries and point out domain separation issues.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bertoni, G., Daemen, J., Peeters, M., Van Assche, G., Van Keer, R.: Ketje v2. Submission to CAESAR: Competition for Authenticated Encryption. Security, Applicability, and Robustness (Round 3) (2014). http://competitions.cr.yp.to/round3/ketjev2.pdf
Daemen, J., Rijmen, V.: The Design of Rijndael: AES - The Advanced Encryption Standard. Information Security and Cryptography. Springer, Heidelberg (2002). https://doi.org/10.1007/978-3-662-04722-4
Eichlseder, M., Kales, D.: Clustering related-tweak characteristics: application to MANTIS-6. IACR Trans. Symmetric Cryptol. 2018(2), 111–132 (2018). https://doi.org/10.13154/tosc.v2018.i2.111-132
Eichlseder, M., Kales, D., Schofnegger, M.: Official Comment: FlexAEAD. Posting on the NIST LWC mailing list. https://groups.google.com/a/list.nist.gov/d/msg/lwc-forum/cRjs9x43G2I/KsBQLdDODAAJ
Jutla, C.S.: Encryption modes with almost free message integrity. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 529–544. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44987-6_32
Jutla, C.S.: Encryption modes with almost free message integrity. J. Cryptol. 21(4), 547–578 (2008). https://doi.org/10.1007/s00145-008-9024-z
Kam, J.B., Davida, G.I.: Structured design of substitution-permutation encryption networks. IEEE Trans. Comput. 28(10), 747–753 (1979). https://doi.org/10.1109/TC.1979.1675242
Mège, A.: Official Comment: FlexAEAD. Posting on the NIST LWC mailing list. https://groups.google.com/a/list.nist.gov/d/msg/lwc-forum/DPQVEJ5oBeU/YXW0QjfjBQAJ
Mouha, N., Wang, Q., Gu, D., Preneel, B.: Differential and linear cryptanalysis using mixed-integer linear programming. In: Wu, C.-K., Yung, M., Lin, D. (eds.) Inscrypt 2011. LNCS, vol. 7537, pp. 57–76. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34704-7_5
do Nascimento, E.M.: Algoritmo de Criptografia Leve com Utilização de Autenticação. Ph.D. thesis, Instituto Militar de Engenharia, Rio de Janeiro (2017). http://www.comp.ime.eb.br/pos/arquivos/publicacoes/dissertacoes/2017/2017-Eduardo.pdf
do Nascimento, E.M., Xexéo, J.A.M.: A flexible authenticated lightweight cipher using Even-Mansour construction. In: IEEE International Conference on Communications - ICC 2017, pp. 1–6. IEEE (2017). https://doi.org/10.1109/ICC.2017.7996734
do Nascimento, E.M., Xexéo, J.A.M.: A lightweight cipher with integrated authentication. In: Simpósio Brasileiro em Segurança da Informação e de Sistemas Computacionais - SBSEG, pp. 25–32. Sociedade Brasileira de Computação (2018). https://portaldeconteudo.sbc.org.br/index.php/sbseg_estendido/article/view/4138
do Nascimento, E.M., Xexéo, J.A.M.: FlexAEAD. Submission to Round 1 of the NIST Lightweight Cryptography Standardization Process (2019). https://csrc.nist.gov/CSRC/media/Projects/Lightweight-Cryptography/documents/round-1/spec-doc/FlexAEAD-spec.pdf
do Nascimento, E.M., Xexéo, J.A.M.: Official Comment: FlexAEAD. Posting on the NIST LWC mailing list (2019). https://csrc.nist.gov/CSRC/media/Projects/Lightweight-Cryptography/documents/round-1/official-comments/FlexAEAD-official-comment.pdf
National Institute of Standards and Technology (NIST): Lightweight cryptography standardization process (2019). https://csrc.nist.gov/projects/lightweight-cryptography
Rahman, M., Saha, D., Paul, G.: Attacks against FlexAEAD. Posting on the NIST LWC mailing list. https://groups.google.com/a/list.nist.gov/d/msg/lwc-forum/VLWtGnJStew/X3Fxexg1AQAJ
Rahman, M., Saha, D., Paul, G.: Interated truncated differential for internal keyed permutation of FlexAEAD. IACR Cryptology ePrint Archive, Report 2019/539 (2019). https://eprint.iacr.org/2019/539
Wu, H., Preneel, B.: AEGIS v1.1. Submission to CAESAR: Competition for Authenticated Encryption. Security, Applicability, and Robustness (Round 3 and Final Portfolio) (2014). http://competitions.cr.yp.to/round3/aegisv11.pdf
Wu, S., Wang, M.: Security evaluation against differential cryptanalysis for block cipher structures. IACR Cryptology ePrint Archive, Report 2011/551 (2011)
Acknowledgements
We thank the designers of
 and
and
 for their comments on a preliminary version of this analysis on the NIST LWC mailing list.
for their comments on a preliminary version of this analysis on the NIST LWC mailing list.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Eichlseder, M., Kales, D., Schofnegger, M. (2019). Forgery Attacks on FlexAE and FlexAEAD. In: Albrecht, M. (eds) Cryptography and Coding. IMACC 2019. Lecture Notes in Computer Science(), vol 11929. Springer, Cham. https://doi.org/10.1007/978-3-030-35199-1_10
Download citation
DOI: https://doi.org/10.1007/978-3-030-35199-1_10
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-35198-4
Online ISBN: 978-3-030-35199-1
eBook Packages: Computer ScienceComputer Science (R0)