Abstract
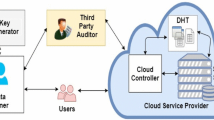
Data outsourcing is useful for ICT organizations who need cost-effective management of resources. Auditing of outsourced data is an essential requirement for the data owner who outsources it to the untrusted third party storage service provider. It is a posterior mechanism for data verification. In this work, we propose a distributed auditing scheme for verifying the integrity of the outsourced data as compare to the existing centralized auditing schemes. To the best of our knowledge, this is the first such scheme uses distributed auditing. The proposed scheme avoids intense computing requirement at the data owner or the auditor. We classify the existing auditing schemes into generic classes, analyze them, and compare them with the proposed scheme. The performance evaluation of the auditing operation in the proposed scheme is carried out and verified with the analytical results.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Barsoum, A., Hasan, A.: Enabling dynamic data and indirect mutual trust for cloud computing storage systems. IEEE Trans. Parallel Distrib. Syst. 24(12), 2375–2385 (2013)
De Capitani Di Vimercati, S., Foresti, S., Jajodia, S., Paraboschi, S., Samarati, P.: Over-encryption: management of access control evolution on outsourced data. In Proceedings of the 33rd International Conference on Very Large Data Bases, pp. 123–134. VLDB endowment (2007)
Arapinis, M., Bursuc, S., Ryan, M.: Privacy-supporting cloud computing by in-browser key translation. J. Comput. Secur. 21(6), 847–880 (2013)
Shacham, H., Waters, B.: Compact proofs of retrievability. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 90–107. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-89255-7_7
Juels, A., Kaliski Jr., B.S.: Pors: proofs of retrievability for large files. In: Proceedings of the 14th ACM Conference on Computer and Communications Security, pp. 584–597. ACM (2007)
Ateniese, G., Di Pietro, R., Mancini, L.V., Tsudik, G.: Scalable and efficient provable data possession. In: Proceedings of the 4th International Conference on Security and Privacy in Communication Netowrks, p. 9. ACM (2008)
Ateniese, G., et al.: Provable data possession at untrusted stores. In: Proceedings of the 14th ACM Conference on Computer and Communications Security, pp. 598–609. ACM (2007)
Ateniese, G., et al.: Remote data checking using provable data possession. ACM Trans. Inf. Syst. Secur. (TISSEC) 14(1), 12 (2011)
Popa, R.A., Lorch, J.R., Molnar, D., Wang, H.J., Zhuang, L.: Enabling security in cloud storage slas with cloudproof. In: USENIX Annual Technical Conference, vol. 242, pp. 355–368 (2011)
Deswarte, Y., Quisquater, J.-J., Saïdane, A.: Remote integrity checking. In: Jajodia, S., Strous, L. (eds.) Integrity and Internal Control in Information Systems VI. IIFIP, vol. 140, pp. 1–11. Springer, Boston, MA (2004). https://doi.org/10.1007/1-4020-7901-X_1
Zhang, Y., Chunxiang, X., Li, H., Liang, X.: Cryptographic public verification of data integrity for cloud storage systems. IEEE Cloud Comput. 5, 44–52 (2016)
Zhang, Y., Chunxiang, X., Liang, X., Li, H., Yi, M., Zhang, X.: Efficient public verification of data integrity for cloud storage systems from indistinguishability obfuscation. IEEE Trans. Inf. Forensics Secur. 12(3), 676–688 (2017)
Saxena, R., Dey, S.: Cloud audit: a data integrity verification approach for cloud computing. Procedia Comput. Sci. 89, 142–151 (2016)
Liu, C., Yang, C., Zhang, X., Chen, J.: External integrity verification for outsourced big data in cloud and iot: a big picture. Future Gener. Comput. Syst. 49, 58–67 (2015)
Chris Erway, C., Küpçü, A., Papamanthou, C., Tamassia, R.: Dynamic provable data possession. ACM Trans. Inf. Syst. Secur. 17(4), 15:1–15:29 (2015)
Barsoum, A.F., Anwar Hasan, M.: Provable possession and replication of data over cloud servers. Centre For Applied Cryptographic Research (CACR), University of Waterloo, Report, 32:2010 (2010)
Chunxiang, X., Zhang, Y., Yong, Y., Zhang, X., Wen, J.: An efficient provable secure public auditing scheme for cloudstorage. KSII Trans. Internet Inf. Syst. 8(11), 4226–4241 (2014)
Hussain, Md., Al-Mourad, M.B.: Effective third party auditing in cloud computing. In: 2014 28th International Conference on Advanced Information Networking and Applications Workshops (WAINA), pp. 91–95. IEEE (2014)
Yu, Y., Li, Y., Yang, B., Susilo, W., Yang, G., Bai, J.: Attribute-based cloud data integrity auditing for secure outsourced storage. IEEE Trans. Emerging Topics Comput. 1 (2019)
Kumar, N., Mathuria, A.: Improved write access control and stronger freshness guarantee to outsourced data. In: Proceedings of the 18th International Conference on Distributed Computing and Networking, Hyderabad, India, January 5–7, 2017, p. 19 (2017)
Wang, C., Chow, S.S.M., Wang, Q., Ren, K., Lou, W.: Privacy-preserving public auditing for secure cloud storage. IEEE Trans. Comput. 62(2), 362–375 (2013)
Yamamoto, G., Oda, S., Aoki, K.: Fast integrity for large data. In: Proceedings of the ECRYPT Workshop Software Performance Enhancement for Encryption and Decryption, pp. 21–32 (2007)
Krawczyk, H., Bellare, M., Canetti, R.: Hmac: Keyed-hashing for message authentication. Technical report (1997)
Ateniese, G., et al.: Remote data checking using provable data possession. ACM Trans. Inf. Syst. Secur. 14(1), 12:1–12:34 (2011)
Oprea, A., Reiter, M.K., Yang, K., et al.: Space-efficient block storage integrity. In: NDSS (2005)
Fu, K.E.: Group sharing and random access in cryptographic storage file systems. Technical report, MASTER’S THESIS, MIT (1999)
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Dwivedi, A.K., Kumar, N., Pathela, M. (2020). Distributed and Lazy Auditing of Outsourced Data. In: Hung, D., D´Souza, M. (eds) Distributed Computing and Internet Technology. ICDCIT 2020. Lecture Notes in Computer Science(), vol 11969. Springer, Cham. https://doi.org/10.1007/978-3-030-36987-3_24
Download citation
DOI: https://doi.org/10.1007/978-3-030-36987-3_24
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-36986-6
Online ISBN: 978-3-030-36987-3
eBook Packages: Computer ScienceComputer Science (R0)