Abstract
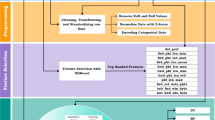
Cloud computing is currently a thriving technology. Due to their critical nature, it is necessary to consider all kinds of intrusions and abuses that typically plague cloud environments. In order to maintain its resilient-state, a cloud system should have tools capable of detecting known and updated threats, but also unknown attacks (0-day). This paper presents a two-level deep learning architecture for detecting multiple attack classes. In particular, it is an extension of a previous study with a dual objective: reducing the false alarm rate and improving the detection rate, and testing the system with different types of attacks. The problem is treated as a semi-supervised task, and the anomaly detector exploits deep autoencoder building blocks. The model is described and tested on the recent CICIDS2017 and CSE-CIC-IDS2018 datasets. The performance comparison with our previous study shows a lower false alarm rate and the validity of the model for multiple attack classes.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Abadi, M., et al.: TensorFlow: large-scale machine learning on heterogeneous systems (2015). http://tensorflow.org/
Argyris, C.: Double loop learning in organizations. Harv. Bus. Rev. 55(5), 115–125 (1977)
Bengio, Y.: Learning deep architectures for AI. Found. Trends Mach. Learn. 2(1), 1–127 (2009)
Catillo, M., Rak, M., Villano, U.: Discovery of DoS attacks by the ZED-IDS anomaly detector. J. High Speed Netw. 25(4), 349–365 (2019)
Chandola, V., Banerjee, A., Kumar, V.: Anomaly detection: a survey. ACM Comput. Surv. 41(3), 1–58 (2009)
Chollet, F., et al.: Keras (2015). https://github.com/fchollet/keras
El-Yaniv, R., Souroujon, O.: Iterative double clustering for unsupervised and semi-supervised learning. In: Dietterich, T.G., Becker, S., Ghahramani, Z. (eds.) Advances in Neural Information Processing Systems 14, pp. 1025–1032. MIT Press (2002)
Goodfellow, I., Bengio, Y., Courville, A.: Deep Learning (2016)
Hajimirzaei, B., Navimipour, N.: Intrusion detection for cloud computing using neural networks and artificial bee colony optimization algorithm. ICT Express 5(1), 56–59 (2018)
Idhammad, M., Karim, A., Belouch, M.: Distributed intrusion detection system for cloud environments based on data mining techniques. Procedia Comput. Sci. 127, 35–41 (2018)
Keegan, N., Ji, S.Y., Chaudhary, A., Concolato, C., Yu, B., Jeong, D.H.: A survey of cloud-based network intrusion detection analysis. Hum.-Centric Comput. Inf. Sci. 6, 1–16 (2016)
Lashkari, A.H., Zang, Y., Owhuo, G., Mamun, M.S.I., Gil, G.D.: Cicflowmeter (formerly iscxflowmeter)—a network traffic flow analyzer. http://www.netflowmeter.ca/netflowmeter.html
Mehmood, Y., Shibli, M.A., Habiba, U., Masood, R.: Intrusion detection system in cloud computing: challenges and opportunities. In: 2013 2nd National Conference on Information Assurance (NCIA), pp. 114–125 (2013)
Mell, P., Grance, T.: The NIST definition of cloud computing. NIST Special Publication 800, 145 (2011)
Moctar, C.B.O.M.E., Konaté, K.: A survey of security challenges in cloud computing. In: 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), pp. 843–849 (2017)
Moustafa, N., Hu, J., Slay, J.: A holistic review of network anomaly detection systems: a comprehensive survey. J. Netw. Comput. Appl. 128, 33–55 (2018)
Riaz, A., Qadir, J., Younis, U., ur Rasool, R., Ahmad, H.F., Kiani, A.K.: Intrusion detection systems in cloud computing: a contemporary review of techniques and solutions. J. Inf. Sci. Eng. 33, 611–634 (2017)
Sharafaldin, I., Lashkari, A.H., Ghorbani, A.A.: Toward generating a new intrusion detection dataset and intrusion traffic characterization. In: Proceedings of the 4th International Conference on Information Systems Security and Privacy - Volume 1: ICISSP, pp. 108–116. INSTICC, SciTePress (2018)
Slonim, N., Tishby, N.: Document clustering using word clusters via the information bottleneck method. In: Proceedings of the 23rd Annual International ACM SIGIR Conference on Research and Development in Information Retrieval, pp. 208–215. Association for Computing Machinery, New York (2000)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Catillo, M., Rak, M., Villano, U. (2020). 2L-ZED-IDS: A Two-Level Anomaly Detector for Multiple Attack Classes. In: Barolli, L., Amato, F., Moscato, F., Enokido, T., Takizawa, M. (eds) Web, Artificial Intelligence and Network Applications. WAINA 2020. Advances in Intelligent Systems and Computing, vol 1150. Springer, Cham. https://doi.org/10.1007/978-3-030-44038-1_63
Download citation
DOI: https://doi.org/10.1007/978-3-030-44038-1_63
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-44037-4
Online ISBN: 978-3-030-44038-1
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)