Abstract
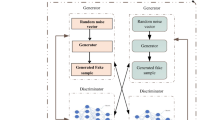
The role of remote resources, such as the ones provided by Cloud infrastructures, is of paramount importance for the implementation of cost effective, yet reliable software systems to provide services to third parties. Cost effectiveness is a direct consequence of a correct estimation of resource usage, to be able to define a budget and estimate the right price to put own services on the market. Attacks that overload resources with non legitimate requests, being them explicit attacks or just malicious, non harmful resource engagements, may push the use of Cloud resources beyond estimation, causing additional costs, or unexpected energy usage, or a lower overall quality of services, so intrusion detection devices or firewalls are set to avoid undesired accesses. We propose the use of Generative Adversarial Neural Networks (GANs) to setup a method for shaping request based attacks capable of reaching resources beyond defenses. The approach is studied by using a publicly available traffic data set, to test the concept and demonstrate its potential applications.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Amato, F., Mazzeo, A., Moscato, V., Picariello, A.: Semantic management of multimedia documents for e-government activity, pp. 1193–1198 (2009). https://doi.org/10.1109/CISIS.2009.195
Amato, F., Moscato, V., Picariello, A., Piccialli, F.: SOS: a multimedia recommender system for online social networks. Future Gen. Comput. Syst. 93, 914–923 (2019). https://doi.org/10.1016/j.future.2017.04.028
Amato, F., Di Martino, B., Marulli, F., Moscato, F.: A federation of cognitive cloud services for trusting data sources. In: Conference on Complex, Intelligent, and Software Intensive Systems pp. 1022–1031. Springer, Heidelberg (2018)
Brunese, L., Mercaldo, F., Reginelli, A., Santone, A.: Formal methods for prostate cancer gleason score and treatment prediction using radiomic biomarkers. Magn. Reson. Imaging (2019)
Brunese, L., Mercaldo, F., Reginelli, A., Santone, A.: Prostate gleason score detection and cancer treatment through real-time formal verification. IEEE Access 7, 186236–186246 (2019)
Canfora, G., Martinelli, F., Mercaldo, F., Nardone, V., Santone, A., Visaggio, C.A.: Leila: formal tool for identifying mobile malicious behaviour. IEEE Trans. Softw. Eng. 45(12), 1230–1252 (2018)
D’Angelo, G., Palmieri, F., Rampone, S.: Detecting unfair recommendations in trust-based pervasive environments. Inf. Sci. 486, 31–51 (2019)
De Francesco, N., Lettieri, G., Santone, A., Vaglini, G.: Grease: a tool for efficient “nonequivalence” checking. ACM Trans. Softw. Eng. Methodol. (TOSEM) 23(3), 24 (2014)
De Maesschalck, R., Jouan-Rimbaud, D., Massart, D.L.: The mahalanobis distance. Chemometr. Intell. Lab. Syst. 50(1), 1–18 (2000)
Dei Rossi, G.L., Iacono, M., Marin, A.: Evaluating the impact of eDoS attacks to cloud facilities. In: 9th EAI International Conference on Performance Evaluation Methodologies and Tools. ACM (2016)
Fiore, U., De Santis, A., Perla, F., Zanetti, P., Palmieri, F.: Using generative adversarial networks for improving classification effectiveness in credit card fraud detection. Inf. Sci. 479, 448–455 (2019)
Giménez, A.C.T., Marañón, G.: Cisc2010 dataset (2012)
Goodfellow, I.J., Pouget-Abadie, J., Mirza, M., Xu, B., Warde-Farley, D., Ozair, S., Courville, A., Bengio, Y.: Generative adversarial networks (2014)
Gribaudo, M., Iacono, M., Manini, D.: Performance evaluation of massively distributed microservices based applications. In: Proceedings of 31st European Conference on Modelling and Simulation, ECMS 2017, pp. 598–604 (2017)
Gribaudo, M., Iacono, M., Manini, D.: Performance evaluation of replication policies in microservice based architectures. Electron. Notes Theoret. Comput. Sci. 337, 45–65 (2018)
Li, J., Zhou, L., Li, H., Yan, L., Zhu, H.: Dynamic traffic feature camouflaging via generative adversarial networks. In: 2019 IEEE Conference on Communications and Network Security (CNS), pp. 268–276, June 2019
Maciá-Fernández, G., Camacho, J., Magán-Carrión, R., García-Teodoro, P., Theron, R.: UGR ’16: a new dataset for the evaluation of cyclostationarity-based network IDSs. Comput. Secur. 73, 411–424 (2018)
Martinelli, F., Marulli, F., Mercaldo, F.: Evaluating convolutional neural network for effective mobile malware detection. Procedia Comput. Sci. 112, 2372–2381 (2017)
Marulli, F., Visaggio, C.A.: Adversarial deep learning for energy management in buildings. In: Proceedings of the 2019 Summer Simulation Conference, p. 50. Society for Computer Simulation International (2019)
Mercaldo, F., Santone, A.: Deep learning for image-based mobile malware detection. J. Comput. Virol. Hacking Tech. 1–15 (2020)
Mikolov, T., Sutskever, I., Chen, K., Corrado, G.S., Dean, J.: Distributed representations of words and phrases and their compositionality. In: Advances in Neural Information Processing Systems, pp. 3111–3119 (2013)
Palmieri, F., Fiore, U., Castiglione, A., De Santis, A.: On the detection of card-sharing traffic through wavelet analysis and support vector machines. Appl. Soft Comput. J. 13(1), 615–627 (2013)
Santone, A.: Automatic verification of concurrent systems using a formula-based compositional approach. Acta Informatica 38(8), 531–564 (2002)
Wichers, D., Williams, J.: OWASP Top-10 2017. OWASP Foundation (2017)
Acknowledgments
This work has been partially supported by MIUR - SecureOpenNets and EU SPARTA and CyberSANE projects. This work was also partially funded by the project “Attrazione e Mobilità dei Ricercatori” Italian PON Programme (PON_AIM 2018 num. AIM1878214-2).
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Campanile, L. et al. (2020). Towards the Use of Generative Adversarial Neural Networks to Attack Online Resources. In: Barolli, L., Amato, F., Moscato, F., Enokido, T., Takizawa, M. (eds) Web, Artificial Intelligence and Network Applications. WAINA 2020. Advances in Intelligent Systems and Computing, vol 1150. Springer, Cham. https://doi.org/10.1007/978-3-030-44038-1_81
Download citation
DOI: https://doi.org/10.1007/978-3-030-44038-1_81
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-44037-4
Online ISBN: 978-3-030-44038-1
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)