Abstract
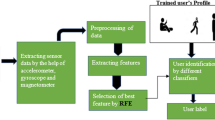
Mobile phone has become an important asset when it comes to information security since it has become a virtual safe. However, to protect the information inside the mobile, the manufacturers use the technologies as password protection, face recognition or fingerprint protection. Nevertheless, it is clear that these security methods can be bypassed. That is when the urge of a post-authentication is coming to the surface. In order to protect the phone from an unauthorized or illegitimate user this method is proposed as a solution. The aim of the proposed solution is to detect the illegitimate user by monitoring the behavior of the user by four main parameters. They are: 1) Keystroke dynamics with a customized keyboard; 2) location detection; 3) voice recognition; 4) Application usage. In the initial state machine learning is used to train this mobile application with the authentic user’s behavior and they are stored in a central database. After the initial training period the application is monitoring the usage and comparing it with the already saved data of the user. Another unique feature of this is the prevention mechanism it executes when an illegitimate user is detected. Furthermore, this application is proposed as an inbuilt application in order to avoid the deletion of app or uninstallation of the app by the intruder. With this Application which is introduced as “AuthDNA” will help you to protect the sensitive information of your mobile device in a case of theft and bypassing of initial authentication.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others

References
Ahirrao, S.A., Ballal, S.S., Sawant, D.K.: Android based remote surveillance system and content sharing between PC and mobile. Int. J. Comput. Appl. Technol. Res. 4, 153–156 (2015). http://ijcat.com/archives/volume4/issue2/ijcatr04021013.pdf
Basavaraju, P., Varde, A.S.: Supervised learning techniques in mobile device apps for androids. In: School on Machine Learning for Data Mining and Search, SIGIR/SIGKDD. ACM SIGKDD Explorations Newsletter (March 2017). https://dl.acm.org/doi/10.1145/3068777.3068782
Bhatti, H.J., Rad, B.B.: Databases in cloud computing. Int. J. Inf. Technol. Comput. Sci. 9(4), 9–17 (2017). https://www.researchgate.net/publication/315993485_Databases_in_Cloud_Computing
Farzad, T., Azam, A., Asadollah, S., Reza, E.A.: A comparison of lightweight databases in mobile systems. J. Comput. 3(7), 147–152 (2011). https://www.researchgate.net/publication/236969019_A_Comparison_of_Lightweight_Databases_in_Mobile_Systems
Kim, J., Kim, H., Kang, P.: Keystroke dynamics-based user authentication using freely typed text based on user-adaptive feature extraction and novelty detection. Appl. Soft Comput. J. (2018). https://doi.org/10.1016/j.asoc.2017.09.045
Sujithra, M., Padmavathi, G., Narayanan, S.: Mobile device data security: a cryptographic approach by outsourcing mobile data to cloud. Procedia Comput. Sci. 47, 480–485 (2015)
Sekar, B., Liu, J.B.: Location based mobile apps development on android platform. IEEE (2014). https://ieeexplore.ieee.org/document/6931527
Venayagamoorthy, G.K., Moonasar, V., Sandrasegaran, K.: Voice recognition using neural networks. In: South African Symposium on Communications and Signal Processing, 8 September, 1998. IEEE, Rondebosch (1998). https://ieeexplore.ieee.org/document/736916
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Chandrasekara, P., Abeywardana, H., Rajapaksha, S., Parameshwaran, S., Yapa Abeywardana, K. (2020). Behavior and Biometrics Based Masquerade Detection Mobile Application. In: Arai, K., Kapoor, S., Bhatia, R. (eds) Intelligent Computing. SAI 2020. Advances in Intelligent Systems and Computing, vol 1230. Springer, Cham. https://doi.org/10.1007/978-3-030-52243-8_32
Download citation
DOI: https://doi.org/10.1007/978-3-030-52243-8_32
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-52242-1
Online ISBN: 978-3-030-52243-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)