Abstract
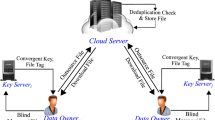
Cloud Storage Providers (CSPs) offer solutions to relieve users from locally storing vast amounts of data, including personal and sensitive ones. While users may desire to retain some privacy on the data they outsource, CSPs are interested in reducing the total storage space by employing compression techniques such as deduplication. We propose a new cryptographic primitive that simultaneously realizes both requirements: Multi-Key Revealing Encryption (MKRE). The goal of MKRE is to disclose the result of a pre-defined function over multiple ciphertexts, even if the ciphertexts were generated using different keys, while revealing nothing else about the data. We present a formal model and a security definition for MKRE and provide a construction of MKRE for generalized deduplication that only uses symmetric key primitives in a black-box way. Our construction allows (a) cloud providers to reduce the storage space by using generalized deduplication to compress encrypted data across users, and (b) each user to maintain a certain privacy level for the outsourced information. Our scheme can be proven secure in the random oracle model (and we argue that this is a necessary evil). We develop a proof-of-concept implementation of our solution. For a test data set, our MKRE construction achieves secure generalized deduplication with a compression ratio of 87% for 1 KB file chunks and 82.2% for 8 KB chunks. Finally, our experiments show that, compared to generalized deduplication setup with un-encrypted files, adding privacy via MKRE introduces a compression overhead of less than \(3\%\) and reduces the storage throughput by at most \(6.9\%\).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The term “Revealing Encryption” was first introduced in an oral presentation by Adam O’Neill.
- 2.
Revealing encryption can be seen as a special case of functional encryption where a single decryption key is published together with the public parameters when the system is initialized.
- 3.
Similarly, MKRE can be seen as a special case of multi-input functional encryption.
- 4.
In this work, we perform generalized deduplication based on Hamming codes, however, the principles we develop are general and can be easily transferred to any transformation function.
- 5.
- 6.
To improve readability and have an homogeneous language when extending RE to multiple users (MKRE), we use \(\mathsf {Reveal}\) instead of Eval in [15]. Also, in Sect. 4 we will split the algorithm \(\mathsf {Setup}\) from [15] into a global set up procedure, called \(\mathsf {Setup}\), and a user-dependent \(\mathsf {KeyGen}\).
References
Agrawal, S., Clear, M., Frieder, O., Garg, S., O’Neill, A., Thaler, J.: Ad hoc multi-input functional encryption (2019). https://eprint.iacr.org/2019/356
Agrawal, S., Gorbunov, S., Vaikuntanathan, V., Wee, H.: Functional encryption: new perspectives and lower bounds. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8043, pp. 500–518. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40084-1_28
Bellare, M., Boldyreva, A., O’Neill, A.: Deterministic and efficiently searchable encryption. In: Menezes, A. (ed.) CRYPTO 2007. LNCS, vol. 4622, pp. 535–552. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74143-5_30
Bellare, M., et al.: Hedged public-key encryption: how to protect against bad randomness. In: Matsui, M. (ed.) ASIACRYPT 2009. LNCS, vol. 5912, pp. 232–249. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-10366-7_14
Bellare, M., Keelveedhi, S., Ristenpart, T.: DupLESS: server-aided encryption for deduplicated storage. In: USENIX Security Symposium, pp. 179–194 (2013)
Bellare, M., Keelveedhi, S., Ristenpart, T.: Message-locked encryption and secure deduplication. In: Johansson, T., Nguyen, P.Q. (eds.) EUROCRYPT 2013. LNCS, vol. 7881, pp. 296–312. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-38348-9_18
Bendlin, R., Nielsen, J.B., Nordholt, P.S., Orlandi, C.: Lower and upper bounds for deniable public-key encryption. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 125–142. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-25385-0_7
Boyd, C., Davies, G.T., Gjøsteen, K., Raddum, H., Toorani, M.: Security notions for cloud storage and deduplication. In: Baek, J., Susilo, W., Kim, J. (eds.) ProvSec 2018. LNCS, vol. 11192, pp. 347–365. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-01446-9_20
Canetti, R., Feige, U., Goldreich, O., Naor, M.: Adaptively secure multi-party computation. In: ACM STOC, pp. 639–648 (1996)
Chenette, N., Lewi, K., Weis, S.A., Wu, D.J.: Practical order-revealing encryption with limited leakage. Fast Softw. Encryption 2016, 474–493 (2016)
Chotard, J., Dufour Sans, E., Gay, R., Phan, D.H., Pointcheval, D.: Decentralized multi-client functional encryption for inner product. In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018. LNCS, vol. 11273, pp. 703–732. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03329-3_24
Curtmola, R., Garay, J.A., Kamara, S., Ostrovsky, R.: Searchable symmetric encryption: improved definitions and efficient constructions. J. Comput. Secur. 19(5), 895–934 (2011)
Douceur, J.R., Adya, A., Bolosky, W.J., Simon, D., Theimer, M., Simon, P.: Reclaiming space from duplicate files in a serverless distributed file system. ICDCS 2002, 617–624 (2002)
Goldwasser, S., et al.: Multi-input functional encryption. In: Nguyen, P.Q., Oswald, E. (eds.) EUROCRYPT 2014. LNCS, vol. 8441, pp. 578–602. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-642-55220-5_32
Haagh, H., Ji, Y., Li, C., Orlandi, C., Song, Y.: Revealing encryption for partial ordering. In: O’Neill, M. (ed.) IMACC 2017. LNCS, vol. 10655, pp. 3–22. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-71045-7_1
Hamming, R.W.: Error detecting and error correcting codes. Bell Syst. Tech. J. 29(2), 147–160 (1950)
Katz, J., Sahai, A., Waters, B.: Predicate encryption supporting disjunctions, polynomial equations, and inner products. J. Cryptol. 26, 191–224 (2013)
Li, J., Chen, X., Li, M., Li, J., Lee, P.P., Lou, W.: Secure deduplication with efficient and reliable convergent key management. IEEE Trans. Parallel Distrib. Syst. 25(6), 1615–1625 (2013)
Li, X., Li, J., Huang, F.: A secure cloud storage system supporting privacy-preserving fuzzy deduplication. Soft Comput. 20(4), 1437–1448 (2015). https://doi.org/10.1007/s00500-015-1596-6
Libert, B., Ţiţiu, R.: Multi-client functional encryption for linear functions in the standard model from LWE. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019. LNCS, vol. 11923, pp. 520–551. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34618-8_18
Liu, J., Asokan, N., Pinkas, B.: secure deduplication of encrypted data without additional independent servers. In: ACM CCS, pp. 874–885 (2015)
Liu, J., Duan, L., Li, Y., Asokan, N.: Secure deduplication of encrypted data: refined model and new constructions. In: Smart, N.P. (ed.) CT-RSA 2018. LNCS, vol. 10808, pp. 374–393. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-76953-0_20
Lucani, D.E., Nielsen, L., Orlandi, C., Pagnin, E., Vestergaard, R.: Secure generalized deduplication via multi-key revealing encryption. Cryptology ePrint Archive, Report 2020/799 (2020). https://eprint.iacr.org/2020/799 (full version of this work)
Michalevsky, Y., Joye, M.: Decentralized policy-hiding ABE with receiver privacy. In: Lopez, J., Zhou, J., Soriano, M. (eds.) ESORICS 2018. LNCS, vol. 11099, pp. 548–567. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-98989-1_27
Nielsen, J.B.: Separating random oracle proofs from complexity theoretic proofs: the non-committing encryption case. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 111–126. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_8
Nielsen, L., Vestergaard, R., Yazdani, N., Talasila, P., Lucani, D.E., Sipos, M.: Alexandria: a proof-of-concept implementation and evaluation of generalised data deduplication. In: IEEE GLOBECOM Workshop on Advances in Edge Computing (2019)
Oracle: What Is ZFS? (2019). https://docs.oracle.com/cd/E23823_01/html/819-5461/zfsover-2.html. Accessed 12 Oct 2019
Planet Labs Inc: download samples of our, high resolution imagery, for monitoring, tasking and large area mapping (2019). https://info.planet.com/download-free-high-resolution-skysat-image-samples/. Accessed 17 Jun 2019
Stefanov, E., Papamanthou, C., Shi, E.: Practical dynamic searchable encryption with small leakage. NDSS 71, 72–75 (2014)
The OpenSSL Project: OpenSSL: the open source toolkit for SSL/TLS. www.openssl.org. Accessed 23 Sep 2019
Vestergaard, R., Lucani, D.E., Zhang, Q.: A randomly accessible lossless compression scheme for time-series data. In: IEEE INFOCOM (2020)
Vestergaard, R., Zhang, Q., Lucani, D.E.: Generalized deduplication: bounds, convergence, and asymptotic properties. In: IEEE GLOBECOM (2019)
Vestergaard, R., Zhang, Q., Lucani, D.E.: Lossless compression of time series data with generalized deduplication. In: IEEE GLOBECOM (2019)
Xia, W., et al.: A comprehensive study of the past, present, and future of data deduplication. Proc. IEEE 104(9), 1681–1710 (2016)
Zhao, Y., Chow, S.S.M.: Updatable block-level message-locked encryption. IEEE Trans. Dependable Secure Comput. (2019)
Acknowledgements
This work was partially financed by: the SCALE-IoT project (Grant No. DFF-7026-00042B) and FoCC (Grant No. DFF-6108-00169) granted by the Danish Council for Independent Research; the AUFF Starting Grant AUFF-2017-FLS-7-1; Aarhus University’s DIGIT Centre; the strategic research area ELLIIT; the Concordium Blockhain Research Center, Aarhus University, Denmark; the European Research Council (ERC) under the European Unions’s Horizon 2020 research and innovation programme under grant agreement No 803096 (SPEC).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Lucani, D.E., Nielsen, L., Orlandi, C., Pagnin, E., Vestergaard, R. (2020). Secure Generalized Deduplication via Multi-Key Revealing Encryption. In: Galdi, C., Kolesnikov, V. (eds) Security and Cryptography for Networks. SCN 2020. Lecture Notes in Computer Science(), vol 12238. Springer, Cham. https://doi.org/10.1007/978-3-030-57990-6_15
Download citation
DOI: https://doi.org/10.1007/978-3-030-57990-6_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-57989-0
Online ISBN: 978-3-030-57990-6
eBook Packages: Computer ScienceComputer Science (R0)