Abstract
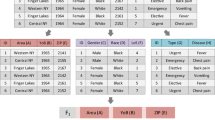
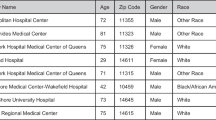
Vertical fragmentation is a promising technique for outsourced data storage. It can protect data privacy while conserving original data without any transformation. Previous vertical fragmentation approaches need to predefine sensitive associations in data as the optimization objective, therefore unavailable for the data lacking related prior knowledge. Inspired by the anonymity measurement in anonymity approaches such as k-anonymity, an anonymity-driven vertical fragmentation problem is defined in this paper. To tackle this problem, a set-based distributed differential evolution (S-DDE) algorithm is proposed. An island model containing four sub-populations is adopted to improve population diversity and search efficiency. Two set-based update operators, i.e., set-based mutation operator and set-based crossover operator, are designed to transfer the calculation of discrete values to corresponding sets in vertical fragmentation. Extensive experiments are carried out, and the performance of S-DDE on anonymity-driven vertical fragmentation is verified. The computation efficiency of S-DDE is investigated, and the effectiveness of the generated vertical fragmentation solution by S-DDE is confirmed.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Aggarwal, G., et al.: Two can keep a secret: a distributed architecture for secure database services. In: CIDR 2005 (2005)
Ciriani, V., De Capitani di Vimercati, S., Foresti, S., Jajodia, S., Paraboschi, S., Samarati, P.: Fragmentation and encryption to enforce privacy in data storage. In: Biskup, J., López, J. (eds.) ESORICS 2007. LNCS, vol. 4734, pp. 171–186. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74835-9_12
Ciriani, V., Vimercati, S.D.C.D., Foresti, S., Jajodia, S., Paraboschi, S., Samarati, P.: Combining fragmentation and encryption to protect privacy in data storage. ACM Trans. Inf. Syst. Secur. 13(3), 22 (2010)
Gao, Z., Pan, Z., Zuo, C., Gao, J., Xu, Z.: An optimized deep network representation of multimutation differential evolution and its application in seismic inversion. IEEE Trans. Geosci. Remote Sens. 57(7), 4720–4734 (2019). https://doi.org/10.1109/tgrs.2019.2892567
Ge, Y.F., et al.: Distributed differential evolution based on adaptive mergence and split for large-scale optimization. IEEE Trans. Cybern. 48(7), 2166–2180 (2018). https://doi.org/10.1109/tcyb.2017.2728725
Köhler, J., Jünemann, K., Hartenstein, H.: Confidential database-as-a-service approaches: taxonomy and survey. J. Cloud Comput. 4(1), 1 (2015)
Li, J., Yao, W., Zhang, Y., Qian, H., Han, J.: Flexible and fine-grained attribute-based data storage in cloud computing. IEEE Trans. Serv. Comput. 10(5), 785–796 (2017). https://doi.org/10.1109/tsc.2016.2520932
Li, M., Sun, X., Wang, H., Zhang, Y., Zhang, J.: Privacy-aware access control with trust management in web service. World Wide Web 14(4), 407–430 (2011). https://doi.org/10.1007/s11280-011-0114-8
Machanavajjhala, A., Gehrke, J., Kifer, D., Venkitasubramaniam, M.: L-diversity: privacy beyond k-anonymity. In: 22nd International Conference on Data Engineering. IEEE (2006). https://doi.org/10.1109/icde.2006.1
Peng, M., Zeng, G., Sun, Z., Huang, J., Wang, H., Tian, G.: Personalized app recommendation based on app permissions. World Wide Web 21(1), 89–104 (2017). https://doi.org/10.1007/s11280-017-0456-y
Price, K., Storn, R.M., Lampinen, J.A.: Differential evolution: a practical approach to global optimization. Springer Science & Business Media, Heidelberg (2006)
Price, K.V.: Differential evolution. In: Handbook of Optimization, pp. 187–214. Springer, Heidelberg (2013)
Rani, K., Sagar, R.K.: Enhanced data storage security in cloud environment using encryption, compression and splitting technique. In: 2017 2nd International Conference on Telecommunication and Networks (TEL-NET). IEEE (2017). https://doi.org/10.1109/tel-net.2017.8343557
SWEENEY, L.: K-anonymity: a model for protecting privacy. Int. J. Uncertainty, Fuzziness Knowl. Based Syst. 10(05), 557–570 (2002). https://doi.org/10.1142/s0218488502001648
UbaidurRahman, N.H., Balamurugan, C., Mariappan, R.: A novel dna computing based encryption and decryption algorithm. Procedia Comput. Sci. 46, 463–475 (2015)
De Capitani di Vimercati, S., Foresti, S., Jajodia, S., Livraga, G., Paraboschi, S., Samarati, P.: Loose associations to increase utility in data publishing. J. Comput. Secur. 23(1), 59–88 (2015)
Wang, H., Wang, Y., Taleb, T., Jiang, X.: Special issue on security and privacy in network computing. World Wide Web 23(2), 951–957 (2020). https://doi.org/10.1007/s11280-019-00704-x
Wang, H., Zhang, Z., Taleb, T.: Special issue on security and privacy of IoT. World Wide Web 21(1), 1–6 (2018)
Xu, X., Xiong, L., Liu, J.: Database fragmentation with confidentiality constraints: a graph search approach. In: 2015 ACM Conference on Data and Application Security and Privacy, pp. 263–270 (2015)
Yu, Y., Au, M.H., Ateniese, G., Huang, X., Susilo, W., Dai, Y., Min, G.: Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans. Inf. Forensics Secur. 12(4), 767–778 (2017)
Zhang, F., Wang, Y., Liu, S., Wang, H.: Decision-based evasion attacks on tree ensemble classifiers. World Wide Web (2020). https://doi.org/10.1007/s11280-020-00813-y
Zhang, J., Tao, X., Wang, H.: Outlier detection from large distributed databases. World Wide Web 17(4), 539–568 (2014)
Zhang, Y., Chen, X., Li, J., Wong, D.S., Li, H., You, I.: Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing. Inf. Sci. 379, 42–61 (2017). https://doi.org/10.1016/j.ins.2016.04.015
Zheng, L.M., Zhang, S.X., Zheng, S.Y., Pan, Y.M.: Differential evolution algorithm with two-step subpopulation strategy and its application in microwave circuit designs. IEEE Trans. Industr. Inf. 12(3), 911–923 (2016). https://doi.org/10.1109/tii.2016.2535347
Zhou, X.G., Peng, C.X., Liu, J., Zhang, Y., Zhang, G.J.: Underestimation-assisted global-local cooperative differential evolution and the application to protein structure prediction. IEEE Trans. Evol. Comput., 1 (2019). https://doi.org/10.1109/tevc.2019.2938531
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Ge, YF., Cao, J., Wang, H., Zhang, Y., Chen, Z. (2020). Distributed Differential Evolution for Anonymity-Driven Vertical Fragmentation in Outsourced Data Storage. In: Huang, Z., Beek, W., Wang, H., Zhou, R., Zhang, Y. (eds) Web Information Systems Engineering – WISE 2020. WISE 2020. Lecture Notes in Computer Science(), vol 12343. Springer, Cham. https://doi.org/10.1007/978-3-030-62008-0_15
Download citation
DOI: https://doi.org/10.1007/978-3-030-62008-0_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-62007-3
Online ISBN: 978-3-030-62008-0
eBook Packages: Computer ScienceComputer Science (R0)