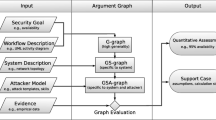
Abstract
To combat cybercrime, a clearer understanding of the attacks and the offenders is necessary. When there is little available data about attack incidents, which is usually the case for new technology, one can make estimations about the necessary investments an offender would need to compromise the system. The next step would be to implement measures that increase these costs to a level that makes the attack unattractive. Our research method follows the principles of design science, where cycles of research activities are used to create artefacts intended to solve real-world problems. Our artefacts are an approach for creating a resource costs model (RCM) and an accompanying modelling tool implemented as a web application. These are used to find the required attacker resources at each stage of the cyber kill chain. End user feedback show that structured visualisation of the required resources raises the awareness of the cyberthreat. This approach has its strength and provides best accuracy with specific attacks, but is more limited when there are many possible attack vectors of different types.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Assante, M.J., Lee, R.M.: The industrial control system cyber kill chain. SANSInstitute InfoSec Reading Room 1 (2015)
Bagnato, A., Kordy, B., Meland, P.H., Schweitzer, P.: Attribute decoration of attack-defense trees. Int. J. Secure Softw. Eng. (IJSSE) 3(2), 1–35 (2012)
Buldas, A., Laud, P., Priisalu, J., Saarepera, M., Willemson, J.: Rational choice of security measures via multi-parameter attack trees. In: Lopez, J. (ed.) CRITIS 2006. LNCS, vol. 4347, pp. 235–248. Springer, Heidelberg (2006). https://doi.org/10.1007/11962977_19
Casey, T.: Threat agent library helps identify information security risks. Intel White Paper 2 (2007)
Cohoen, L.E., Felson, M.: Social change and crime rate trends: a routine activity approach. Am. Sociol. Rev. 44(4), 588–608 (1979)
Ekblom, P., Tiley, N.: Going equipped. Br. J. Criminol. 40(3), 376–398 (2000)
Gadyatskaya, O., Trujillo-Rasua, R.: New directions in attack tree research: catching up with industrial needs. In: Liu, P., Mauw, S., Stølen, K. (eds.) GraMSec 2017. LNCS, vol. 10744, pp. 115–126. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-74860-3_9
Grabosky, P.N.: Virtual criminality: old wine in new bottles? Soc. Legal Stud. 10(2), 243–249 (2001)
Haga, K.: Breaking the cyber kill chain by modelling resource costs. Master’s thesis, NTNU, Trondheim, Norway (2020)
Hahn, A., Thomas, R.K., Lozano, I., Cardenas, A.: A multi-layered and kill-chain based security analysis framework for cyber-physical systems. Int. J. Crit. Infrastruct. Prot. 11, 39–50 (2015)
Hevner, A., Chatterjee, S.: Design science research in information systems. In: Design Research in Information Systems, pp. 9–22. Springer, Boston (2010). https://doi.org/10.1007/978-1-4419-5653-8_2
Hong, J.B., Kim, D.S.: Performance analysis of scalable attack representation models. In: Janczewski, L.J., Wolfe, H.B., Shenoi, S. (eds.) SEC 2013. IAICT, vol. 405, pp. 330–343. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-39218-4_25
Hutchins, E.M.: The cyber kill chain. Technical report, Lockheed Martin (2020). https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html. Accessed 12 Apr 2020
Hutchins, E.M., Cloppert, M.J., Amin, R.M.: Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. Leading Issues Inf. Warfare Secur. Res. 1(1), 80 (2011)
Jensen, P.G., Larsen, K., Legay, A., Poulsen, D.: Quantitative evaluation of attack defense trees using stochastic timed automata. In: International Workshop on Graphical Models for Security, pp. 75–90. HAL Id: hal-01640091 (2017)
Jordan, B., Piazza, R., Wounder, J.: Stix version 2.0. part 1: Stix core concepts. Technical report, OASIS Committee Specifications 01 (2017) http://docs.oasis-open.org/cti/stix/v2.0/stix-v2.0-part1-stix-core.html. Accessed 13 Apr 2020
Kordy, B., Piètre-Cambacédès, L., Schweitzer, P.: Dag-based attack and defense modeling: don’t miss the forest for the attack trees. Comput. Sci. Rev. 13, 1–38 (2014)
Kshetri, N.: The simple economics of cybercrimes. IEEE Secur. Privacy 4(1), 33–39 (2006)
Kumar, R., Ruijters, E., Stoelinga, M.: Quantitative attack tree analysis via priced timed automata. In: Sankaranarayanan, S., Vicario, E. (eds.) FORMATS 2015. LNCS, vol. 9268, pp. 156–171. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-22975-1_11
Lund, M.S., Hareide, O.S., Jøsok, Ø.: An attack on an integrated navigation system. NECESSE 3(2), 149–163 (2018)
Manky, D.: Cybercrime as a service: a very modern business. Comput. Fraud Secur. 2013(6), 9–13 (2013)
McQueen, M.A., Boyer, W.F., Flynn, M.A., Beitel, G.A.: Quantitative cyber risk reduction estimation methodology for a small scada control system. In: Proceedings of the 39th Annual Hawaii International Conference on System Sciences (HICSS 2006), vol. 9, pp. 226–226. IEEE (2006)
Meadows, C.: A representation of protocol attacks for risk assessment. In: Proceedings of the DIMACS Workshop on Network Threats, pp. 1–10 (1998)
Nagaraju, V., Fiondella, L., Wandji, T.: A survey of fault and attack tree modeling and analysis for cyber risk management. In: 2017 IEEE International Symposium on Technologies for Homeland Security (HST), pp. 1–6. IEEE (2017)
Nykodym, N., Taylor, R., Vilela, J.: Criminal profiling and insider cyber crime. Comput. Law Secur. Rev. 21(5), 408–414 (2005)
Pendse, S.G.: Ethical hazards: a motive, means, and opportunity approach to curbing corporate unethical behavior. J. Bus. Ethics 107(3), 265–279 (2012)
Pols, P.: The unified kill chain: Designing a unified kill chain for analyzing, comparing and defending against cyber attacks. Cyber Security Academy (2017)
Preuß, J., Furnell, S.M., Papadaki, M.: Considering the potential of criminal profiling to combat hacking. J. Comput. Virol. 3(2), 135–141 (2007)
Ries, E.: The lean startup : how constant innovation creates radically successful businesses. Portfolio Penguin (2011)
Rogers, M.K.: The psyche of cybercriminals: a psycho-social perspective. In: Ghosh, S., Turrini, E. (eds.) Cybercrimes: A Multidisciplinary Analysis, pp. 217–235. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-13547-7_14
Saini, V., Duan, Q., Paruchuri, V.: Threat modeling using attack trees. J. Comput. Sci. Colleges 23(4), 124–131 (2008)
Schneier, B.: Attack trees. Dr. Dobb’s J. 24(12), 21–29 (1999)
Shinder, D.L., Tittel, E.: Chapter 3 - understanding the people on the scene. In: Scene of the Cybercrime, pp. 93–146. Syngress, Burlington (2002)
Simon, H.A.: The Sciences of the Artificial, 3rd edn. MIT Press, Cambridge (1996)
Van Ruitenbeek, E., Keefe, K., Sanders, W.H., Muehrcke, C.: Characterizing the behavior of cyber adversaries: the means, motive, and opportunity of cyberattacks. In: 40th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Supplemental (DSN 2010), pp. 17–18 (2010)
Walde, A., Hanus, E.G.: The feasibility of AIS- and GNSS-based attacks within the maritime industry. Master’s thesis, NTNU, Trondheim, Norway (2020)
Warikoo, A.: Proposed methodology for cyber criminal profiling. Inf. Secur. J. Global Perspect. 23(4–6), 172–178 (2014)
Wingrove, M.: Security flaws open ECDIS to cyber crime. Technical report, Riviera (2018). https://www.rivieramm.com/opinion/opinion/security-flaws-open-ecdis-to-cyber-crime-24334. Accessed 20 Apr 2020
Acknowledgment
The research leading to these results has partially been performed by the Cyber Security in Merchant Shipping Service Evolution (CySiMS-SE) project, which received funding from the Research Council of Norway under Grant No. 295969.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Tool screenshots
B Cybercriminal profiles
 Script kiddie (SK) has a low level of motivation, thus time consuming attacks are not attractive to this profile. The technical skills are limited to minimal and the profile only accepts a minimal cost. Script kiddies will only utilize resources that can be realized legally and have external access.
Script kiddie (SK) has a low level of motivation, thus time consuming attacks are not attractive to this profile. The technical skills are limited to minimal and the profile only accepts a minimal cost. Script kiddies will only utilize resources that can be realized legally and have external access.
 Hacktivist (H) has a medium to high level of motivation anchored in the political cause they represent, thus they may conduct time consuming, targeted attacks. The technical skills of a hacktivist is limited to minimal. In order to fight for their cause, the hacktivist accepts some expenses. The hacktivist is willing to require resources illegally and have external access level.
Hacktivist (H) has a medium to high level of motivation anchored in the political cause they represent, thus they may conduct time consuming, targeted attacks. The technical skills of a hacktivist is limited to minimal. In order to fight for their cause, the hacktivist accepts some expenses. The hacktivist is willing to require resources illegally and have external access level.
 Vandal (V) has a low to medium motivation and will only invest a limited amount of time in attention seeking attacks. The technical skills of the vandal is limited to minimal and the profile accepts a low cost. Vandals will only utilize resources that can be realized legally and have external access.
Vandal (V) has a low to medium motivation and will only invest a limited amount of time in attention seeking attacks. The technical skills of the vandal is limited to minimal and the profile accepts a low cost. Vandals will only utilize resources that can be realized legally and have external access.
 Petty criminal (PC) has a medium motivation level, willing to invest some time in attacks that bring financial gain. They possess operational technical skills and accepts a medium cost. The petty criminal is willing to require resources illegally and has external access level.
Petty criminal (PC) has a medium motivation level, willing to invest some time in attacks that bring financial gain. They possess operational technical skills and accepts a medium cost. The petty criminal is willing to require resources illegally and has external access level.
 Mobster (M) has a medium to high level of motivation given that financial gain is possible, thus they may conduct time consuming attacks. The technical skills are operational and the profile accepts costly attacks. Mobsters won’t second guess illegal resources and have external access level.
Mobster (M) has a medium to high level of motivation given that financial gain is possible, thus they may conduct time consuming attacks. The technical skills are operational and the profile accepts costly attacks. Mobsters won’t second guess illegal resources and have external access level.
 Cyberwarrior (CW) is a state-sponsored actor with a high motivation level, thus will conduct persistent, highly time consuming attacks. The cyberwarrior has adept technical skills for launching any attack. In addition, the cyberwarrior is not limited by any costs and disposes resources that may be required illegally. As an immediate result of the adept skill level, the cyberwarrior has internal access.
Cyberwarrior (CW) is a state-sponsored actor with a high motivation level, thus will conduct persistent, highly time consuming attacks. The cyberwarrior has adept technical skills for launching any attack. In addition, the cyberwarrior is not limited by any costs and disposes resources that may be required illegally. As an immediate result of the adept skill level, the cyberwarrior has internal access.
 Terrorist (T) tends to be highly motivated and well-funded, thus can conduct time consuming and costly cyberattacks to front beliefs. The technical skills are limited to minimal. The Terrorist is willing to require resources illegally and have external access level.
Terrorist (T) tends to be highly motivated and well-funded, thus can conduct time consuming and costly cyberattacks to front beliefs. The technical skills are limited to minimal. The Terrorist is willing to require resources illegally and have external access level.
 Internal - Hostile (IN-H) has a medium motivation level and may launch attacks that require some time. The profile knows the system well, which yields an operational technical skill. Some expenses are acceptable, limited to legally acquired resources. Internals have internal access level by default.
Internal - Hostile (IN-H) has a medium motivation level and may launch attacks that require some time. The profile knows the system well, which yields an operational technical skill. Some expenses are acceptable, limited to legally acquired resources. Internals have internal access level by default.
 Internal - Non-hostile (IN-NH) launces cyberattacks by accident, thus not motivated at all to invest any time or money in a cyberattack and will only possess resources that can be legally realized. Given that accidental cyberattacks are possible yields an operational skill level and an internal access level.
Internal - Non-hostile (IN-NH) launces cyberattacks by accident, thus not motivated at all to invest any time or money in a cyberattack and will only possess resources that can be legally realized. Given that accidental cyberattacks are possible yields an operational skill level and an internal access level.
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Haga, K., Meland, P.H., Sindre, G. (2020). Breaking the Cyber Kill Chain by Modelling Resource Costs. In: Eades III, H., Gadyatskaya, O. (eds) Graphical Models for Security. GraMSec 2020. Lecture Notes in Computer Science(), vol 12419. Springer, Cham. https://doi.org/10.1007/978-3-030-62230-5_6
Download citation
DOI: https://doi.org/10.1007/978-3-030-62230-5_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-62229-9
Online ISBN: 978-3-030-62230-5
eBook Packages: Computer ScienceComputer Science (R0)