Abstract
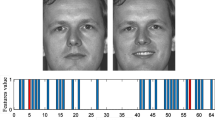
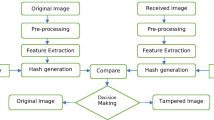
This paper describes Twizzle Benchmarking, a framework originally developed for evaluating and comparing the performance of perceptual image hashing algorithms. There are numerous perceptual hashing approaches with different characteristics in terms of robustness and sensitivity, which also use different techniques for feature extraction and distance measurements, making comparison difficult. For this reason, we have developed Twizzle Benchmarking, which enables comparison and evaluation regardless of the algorithm, distance calculation, data set or type of data. Furthermore, Twizzle is not limited to perceptual hashing approaches, but can be used for a variety of purposes and classification problems, such as multimedia forensics, face recognition or biometric authentication.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
References
Bulan, O., Mao, J., Sharma, G.: Geometric distortion signatures for printer identification (2009)
Davarzani, R., Mozaffari, S., Yaghmaie, K.: Perceptual image hashing using center-symmetric local binary patterns. Multimed. Tools Appl. 75(8), 4639–4667 (2015). https://doi.org/10.1007/s11042-015-2496-6
Ferreira, A., Navarro, L.C., Pinheiro, G., Santos, J.A.D., Rocha, A.: Laser printer attribution: exploring new features and beyond. Forensic Sci. Int. 247, 105–125 (2015)
Joshua S.W., Jeanna N.M., John L.S.: A method for the automated detection phishing websites through both site characteristics and image analysis (2012)
Kim, D.G., Lee, H.K.: Colour laser printer identification using halftone texture fingerprint. Electron. Lett. 51(13), 981–983 (2015)
McKinney, W.: Data structures for statistical computing in python (2010)
Sharif, M., Naz, F., Yasmin, M., Shahid, M.A., Rehman, A.: Face recognition: a survey. J. Eng. Sci. Technol. Rev. 10(2), 166–177 (2017)
Steinebach, M., Liu, H., Yannikos, Y.: Efficient cropping-resistant robust image hashing (2014)
Swaminathan, A., Mao, Y., Wu, M.: Robust and secure image hashing. IEEE Trans. Inf. Forensics Secur. 1(2), 215–230 (2006)
Tabatabaei, S.A.H., Ur-Rehman, O., Zivic, N., Ruland, C.: Secure and robust two-phase image authentication. IEEE Trans. Multimedia 17(7), 945–956 (2015)
Tang, Z., Zhang, X., Li, X., Zhang, S.: Robust image hashing with ring partition and invariant vector distance. IEEE Trans. Inf. Forensics Secur. 11(1), 200–214 (2016)
Venkatesan, R., Koon, S.M., Jakubowski, M.H., Moulin, P.: Robust image hashing (2000)
Wu, Y., Kong, X., You, X., Guo, Y.: Printer forensics based on page document’s geometric distortion (2009)
Yang, B., Gu, F., Niu, X.: Block mean value based image perceptual hashing (2006)
Zauner, C., Steinebach, M., Hermann, E.: Rihamark: perceptual image hash benchmarking (2011)
Zhang, H., Schmucker, M., Niu, X.: The design and application of PHABS: a novel benchmark platform for perceptual hashing algorithms (2007)
Zhao, W., Chellappa, R., Phillips, P.J., Rosenfeld, A.: Face recognition: a literature survey. ACM Comput. Surv. (CSUR) 35(4), 399–458 (2003)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Escher, S., Teufert, P., Herrmann, R., Strufe, T. (2020). Twizzle - A Multi-purpose Benchmarking Framework for Semantic Comparisons of Multimedia Object Pairs. In: Boureanu, I., et al. Computer Security. ESORICS 2020. Lecture Notes in Computer Science(), vol 12580. Springer, Cham. https://doi.org/10.1007/978-3-030-66504-3_13
Download citation
DOI: https://doi.org/10.1007/978-3-030-66504-3_13
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-66503-6
Online ISBN: 978-3-030-66504-3
eBook Packages: Computer ScienceComputer Science (R0)