Abstract
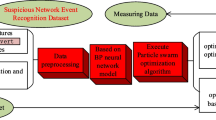
The traditional automatic defense network active attack data location and early warning method has the shortcoming of poor localization performance, so the research of automatic defense network active attack data location and warning method is put forward. The active attack data is detected by the space distance of the network node data, and the active attack data is judged whether there is active attack data in the network, which is based on the detected active attack data. The multi-objective binary particle swarm optimization (BPSO) algorithm is used to obtain the optimal task allocation scheme for active attack data location. Based on it, the algorithm of extreme learning machine is used to realize the location and early warning of active attack data. Through the experiment, put forward the automatic Compared with traditional methods, the convergence value of active attack data location and early warning method of defensive network increases 23.61 and the error rate of location decreases by 15. It is fully explained that the proposed automatic defense network active attack data location and early warning method has better localization performance.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
He, Y.: Research on active security defense system of campus network based on honeypot technology. Comput. Fans 12(4), 21–22 (2016)
Zhu, C., Zhao, D.: A packet allocation protection method for network attack crime prevention. Sci. Technol. Bull. 32(8), 203–206 (2016)
Dong, X., Lin, L., Zhang, X., et al.: Application of active defense technology in communication network security engineering. Inf. Secur. Technol. 7(1), 80–84 (2016)
Pujiang, L.L.: Research on network security early warning and defense system based on three-domain model. Inf. Secur. Technol. 8(8), 68–72 (2017)
Jiang, S., Luo, T.: Research on detection method of network small disturbance intrusion source location under non-uniform noise environment. Sci. Technol. Eng. 17(5), 247–251 (2017)
Luo, X.W., Tao, H.: Research on Simulation of attack signal location and recognition in wireless communication networks. Comput. Simul. 33(11), 320–323 (2016)
He, C.: Design of computer network security active defense model in big data era. J. Ningbo Vocat. Tech. Coll. 20(4), 97–99 (2016)
Di, Z.: Research on the current situation and defense measures of network security management in Colleges and Universities. Electron. Technol. Softw. Eng. 56(13), 221–221 (2016)
Liu, S., Li, Z., Zhang, Y., et al.: Introduction of key problems in long-distance learning and training. Mob. Networks Appl. 24(1), 1–4 (2019)
Chaocheng, Q., Jianhong, Q.: Network security defense model of metal trading based on attack detection. World Nonferrous Metals 23(7), 77–78 (2016)
Huang, R., Huang, R.: Simulation research on privacy information protection of network users. Comput. Simul. 51(11), 319–322 + 423 (2017)
Liu, S., Bai, W., Srivastava, G., Machado, J.A.T.: Property of self-similarity between baseband and modulated signals. Mob. Networks Appl. 25(4), 1537–1547 (2019). https://doi.org/10.1007/s11036-019-01358-9
Shuai, L., Weiling, B., Nianyin, Z., et al.: A fast fractal based compression for MRI images. IEEE Access 7, 62412–62420 (2019)
Shuke, Yu.: Research on target intrusion detection based on mobile wireless sensor networks. Digital Commun. World 59(12), 6–8 (2017)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Huang, Jz., Xie, Wd. (2021). Research on Automatic Defense Network Active Attack Data Location and Early Warning Method. In: Liu, S., Xia, L. (eds) Advanced Hybrid Information Processing. ADHIP 2020. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 347. Springer, Cham. https://doi.org/10.1007/978-3-030-67871-5_24
Download citation
DOI: https://doi.org/10.1007/978-3-030-67871-5_24
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-67870-8
Online ISBN: 978-3-030-67871-5
eBook Packages: Computer ScienceComputer Science (R0)