Abstract
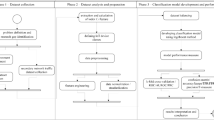
With the advances in Internet of Things (IoT) technologies, more and more smart sensors and devices are connected to the Internet. Since the original idea of smart devices is better connection with each other, very limited security mechanism has been designed. Due to the diverse behaviors for various types of devices, it would be costly to manually design separate security mechanism. To prevent these devices from potential threats, It would be helpful if we could learn the characteristics of diverse device types based on the network packets generated. In this paper, we propose a machine learning approach to device type identification through network traffic analysis for anomaly detection in IoT. First, characteristics of different types of IoT devices are extracted from the generated network packets and learned using unsupervised and supervised learning methods. Second, we apply feature selection methods to the model learned from device type identification module to improve the performance of classification. In our experiments, the performance of device type identification on real data in a smart factory using supervised learning is better than unsupervised learning. The best performance can be achieved by XGBoost with an accuracy of 97.6% and micro-averaging F1 score of 97.6%. This shows the potential of the proposed approach for automatically identifying devices for anomaly detection in smart factories. Further investigation is needed to verify the proposed approach using more types of devices.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Pappu, R.S.: Physical one-way functions. Ph.D. dissertation, Massachusetts Institute of Technology (2001)
Huang, Z., Wang, Q.: A PUF-based unified identity verification framework for secure IoT hardware via device authentication. World Wide Web 23(2), 1057–1088 (2019). https://doi.org/10.1007/s11280-019-00677-x
Alrashdi, I., Alqazzaz, A., Aloufi, E., Alharthi, R., Zohdy, M., Ming, H.: AD-IoT: anomaly detection of IoT cyberattacks in smart city using machine learning. In: Proceedings of IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), pp. 305–310 (2019)
Hasan, M., Islam, M., Zarif, I.I., Hashem, M.M.A.: Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 7, 100059 (2019)
Diro, A.A., Chilamkurti, N.: Distributed attack detection scheme using deep learning approach for internet of things. Future Gener. Comput. Syst. 82, 761–768 (2018)
Koroniotis, N., Moustafa, N., Sitnikova, E., Turnbull, B.: Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 100, 779–796 (2019)
Duque Anton, S.D., Kanoor, S., Fraunholz, D., Schotten, H.D.: Evaluation of machine learning-based anomaly detection algorithms on an industrial Modbus/TCP data set. In: Proceedings of the 13th International Conference on Availability, Reliability and Security (ARES 2018), pp. 41:1–41:9. ACM (2018)
Zolanvari, M., Teixeira, M.A., Gupta, L., Khan, K.M., Jain, R.: Machine learning-based network vulnerability analysis of industrial internet of things. IEEE Internet Things J. 6(4), 6822–6834 (2019)
Ngo, M.V., Chaouchi, H., Luo, T., Quek, T.Q.S.: Adaptive anomaly detection for IoT data in hierarchical edge computing. In: Proceedings of the AAAI Workshop on Artificial Intelligence of Things (AIoT) (2020)
Miettinen, M., Marchal, S., Hafeez, I., Sadeghi, A., Asokan, N., Tarkoma, S.: IoT sentinel: automated device-type identification for security enforcement in IoT. In: Proceedings of 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS 2017), pp. 2177–2184 (2017)
Shahid, M.R., Blanc, G., Zhang, Z., Debar, H.: IoT devices recognition through network traffic analysis. In: Proceedings of the IEEE International Conference on Big Data (BigData 2018), pp. 5187–5192 (2018)
Chiba, D., Tobe, K., Moriy, T., Goto, S.: Detecting malicious websites by learning IP address features. In: Proceedings of the 2012 IEEE/IPSJ 12th International Symposium on Applications and the Internet (SAINT 2012), pp. 29–39 (2012)
Kingma, D.P., Ba, J.: Adam: a method for stochastic optimization. In: Proceedings of ICLR 2015 (2015)
Acknowledgement
This study is conducted under the “Artificial Intelligence Oriented for Cyber Security Technology Collaboration Project (1/4)” of the Institute of Information Industry which is subsidized by the Ministry of Economic Affairs of the Republic of China.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Tien, CW., Huang, TY., Chen, P.C., Wang, JH. (2021). Identifying Device Types for Anomaly Detection in IoT. In: Renault, É., Boumerdassi, S., Mühlethaler, P. (eds) Machine Learning for Networking. MLN 2020. Lecture Notes in Computer Science(), vol 12629. Springer, Cham. https://doi.org/10.1007/978-3-030-70866-5_22
Download citation
DOI: https://doi.org/10.1007/978-3-030-70866-5_22
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-70865-8
Online ISBN: 978-3-030-70866-5
eBook Packages: Computer ScienceComputer Science (R0)