Abstract
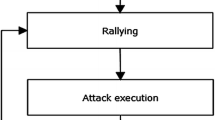
Botnets are a dangerous threat to computer networks. A botnet consists of a bot-master and bot-client connected and communicated through command and control (C&C) servers. When the bot attacks and infects the target computer, it performs several activities. Nevertheless, the introduced model may not detect the connection between one activity and others as a whole botnet attack scenario. The connection between activities is required to get the attack step carried out by each bot. This paper proposes a new approach to detect linkages between bot activities by analyzing the network traffic flows and obtaining a bot attack scenario. The analysis is carried out by finding the frequency of each activity that is sequentially connected. The results show that the proposed model successfully detects interrelated bot activity scenarios based on its pattern.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Aleksieva, Y., Valchanov, H., Aleksieva, V.: An approach for host based botnet detection system. In: Proceedings of the 2019 16th Conference on Electrical Machines, Drives and Power Systems, ELMA 2019, June, pp. 6–8 (2019)
Álvarez Cid-Fuentes, J., Szabo, C., Falkner, K.: An adaptive framework for the detection of novel botnets. Comput. Secur. 79, 148–161 (2018)
Wang, C.Y., et al.: BotCluster: a session-based P2P botnet clustering system on NetFlow. Comput. Netw. 145, 175–189 (2018)
Mathur, L., Raheja, M., Ahlawat, P.: Botnet Detection via mining of network traffic flow. Procedia Comput. Sci. 132, 1668–1677 (2018)
Khan, R.U., Zhang, X., Kumar, R., Sharif, A., Golilarz, N.A., Alazab, M.: An adaptive multi-layer botnet detection technique using machine learning classifiers. Appl. Sci. 9(11), 2375 (2019). https://doi.org/10.3390/app9112375
Eslahi, M.: Bots and botnets: an overview of characteristics , detection and challenges, pp. 23–25, 2012.
Al-Hakbani, M.M., Dahshan, M.H.: Avoiding honeypot detection in peer-to-peer botnets. In: 2015 IEEE International Conference on Engineering and Technology, ICETECH 2015, March 2015
Choi, H., Lee, H., Lee, H., Kim, H.: Botnet detection by monitoring group activities in DNS traffic. In: 7th IEEE International Conference on Computer and Information Technology, CIT 2007, pp. 715–720 (2007)
Choi, H., Lee, H., Kim, H.: BotGAD: detecting botnets by capturing group activities in network traffic. In: Proceedings of the 4th IEEE International Conference on Software Testing, Verification and Validation (ICST), Middlew, pp. 1–8 (2009)
Chowdhury, S., Khanzadeh, M., Akula, R., Zhang, F., Zhang, S., Medal, H., Marufuzzaman, M., Bian, L.: Botnet detection using graph-based feature clustering. J. Big Data 4(1), 14 (2017). https://doi.org/10.1186/s40537-017-0074-7
Hoang, X., Nguyen, Q.: Botnet detection based on machine learning techniques using DNS query data. Future Internet 10(5), 43 (2018)
Hung, C., Sun, H.: A botnet detection system based on machine-learning using flow-based features. In: The 12th International Conference on Emerging Security Information, Systems and Technologies A, SECURWARE 2018, The Twelft, pp. 122–127 (2018)
Garcia, S., Zunino, A., Campo, M.: Survey on network-based botnet detection methods. Sec. Commun. Netw. 7(5), 878–903 ( 2014)
Dollah, R.F.M., Faizal, M.A., Arif, F., Mas’ud, M.Z., Xin, L.K.: Machine learning for HTTP botnet detection using classifier algorithms. J. Telecommun. Electron. Comput. Eng. 10(1–7), 27–30 (2018)
Beigi, E.B., Jazi, H.H., Stakhanova, N., Ghorbani, A.A.: Towards effective feature selection in machine learning-based botnet detection approaches. In: 2014 IEEE Conference on Communications and Network Security, pp. 247–255 (2014)
Garc, S., Grill, M., Stiborek, J., Zunino, A.: An empirical comparison of botnet detection methods. Comput. Secur. 45, 100–123 (2014)
Hanguang, L., Yu, N.: Intrusion detection technology research based on apriori algorithm. Phys. Procedia 24, 1615–1620 (2012)
Ohrui, M., Kikuchi, H., Rosyid, N.R., Terada, M.: Mining botnet coordinated attacks using Apriori-Prefixspan hybrid algorithm. J. Inf. Process. 21(4), 607–616 (2013)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Hostiadi, D.P., Ahmad, T., Wibisono, W. (2021). A New Approach to Detecting Bot Attack Activity Scenario. In: Abraham, A., et al. Proceedings of the 12th International Conference on Soft Computing and Pattern Recognition (SoCPaR 2020). SoCPaR 2020. Advances in Intelligent Systems and Computing, vol 1383. Springer, Cham. https://doi.org/10.1007/978-3-030-73689-7_78
Download citation
DOI: https://doi.org/10.1007/978-3-030-73689-7_78
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-73688-0
Online ISBN: 978-3-030-73689-7
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)