Abstract
Botnets are one of the most prevailing threats for cyber-physical devices around the world. The evolution of botnet attacks has been rampant and diverse with vast scalability. One of the variants is targeting the IoT ecosystem involving devices not limiting to sensors, actuators, and all kinds of smart devices. Modern-day botnet threats have multiple functionalities rather than targeting devices for DDoS. In this paper, we used the two latest IoT Botnet data sets: IoT-23 and MedBIoT, which consists of modern-day attacks that helped us classify them for more than two classes. We have considered 6 variants of IoT botnet attacks from both the data sets and categorise them into 3 classes. We have used ensemble approaches for multi-class classification where random forest outperformed with an accuracy of 99.88. We have also generated new samples using conditional generative adversarial networks (CTGAN) for testing the efficacy and robustness of our models built.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Malicious includes: Bruteforcing, command injection, and Spreading for DDoS.
References
Marzano, A., et al.: The evolution of Bashlite and Mirai IoT botnets. In: 2018 IEEE Symposium on Computers and Communications (ISCC). IEEE (2018)
Mirsky, Y., et al.: Kitsune: an ensemble of autoencoders for online network intrusion detection. arXiv preprint arXiv:1802.09089 (2018)
Meidan, Y., et al.: N-BaIoT-network-based detection of IoT botnet attacks using deep autoencoders. IEEE Pervasive Comput. 17(3), 12–22 (2018)
Moustafa, N., Slay, J.: UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In: 2015 Military Communications and Information Systems Conference (MilCIS). IEEE (2015)
Koroniotis, N., et al.: Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 100, 779–796 (2019)
Hyunjae K., Dong H.A., Gyung M.L., Jeong D.Y., Kyung H.P., Huy K.K.: IoT network intrusion dataset (2019). http://ocslab.hksecurity.net/Datasets/iot-network-intrusion-dataset
Ullah, I., Mahmoud, Q.H.: Two-level flow-based anomalous activity detection system for IoT networks. Electronics 9(3), 530 (2020)
Parmisano, A., Garcia, S., Erquiaga, M.J.: A labeled dataset with malicious and benign IoT network traffic. Stratosphere Laboratory, January 2020. https://www.stratosphereips.org/datasets-iot23
Zeek Network Security Monitor (2019). https://docs.zeek.org/en/current/intro/
Guerra-Manzanares, A., Medina-Galindo, J., Bahsi, H., Nõmm, S.: MedBIoT: generation of an IoT botnet dataset in a medium-sized IoT network. In: Proceedings of the 6th International Conference on Information Systems Security and Privacy (ICISSP), vol. 1, ISBN 978-989-758-399-5, pp. 207–218 (2020). https://doi.org/10.5220/0009187802070218
Xu, L., et al.: Modeling tabular data using conditional GAN. In: Advances in Neural Information Processing Systems (2019)
Crookston, N.L., Finley, A.O.: yaImpute: an R package for kNN imputation. J. Stat. Softw. 23(10), 16 p. (2008)
Xu, L., Veeramachaneni, K.: Synthesizing tabular data using generative adversarial networks. arXiv preprint arXiv:1811.11264 (2018)
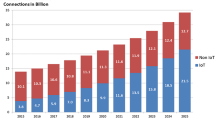
Estimation statistics relating IoT. https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/
Anand, P.M., Gireesh Kumar, T., Sai Charan, P.V.: An ensemble approach for algorithmically generated domain name detection using statistical and lexical analysis. Procedia Comput. Sci. 171, 1129–1136 (2020)
Meidan, Y., et al.: ProfilIoT: a machine learning approach for IoT device identification based on network traffic analysis. In: Proceedings of the Symposium on Applied Computing (2017)
Ani, R., et al.: IoT based patient monitoring and diagnostic prediction tool using ensemble classifier. In: 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI). IEEE (2017)
Perrone, G., et al.: The day after Mirai: a survey on MQTT security solutions after the largest cyber-attack carried out through an army of IoT devices. In: IoTBDS (2017)
Kumar, A., Lim, T.J.: EDIMA: early detection of IoT malware network activity using machine learning techniques. In: 2019 IEEE 5th World Forum on Internet of Things (WF-IoT). IEEE (2019)
Statistics relating to attacks on IoT ecosystem (2021). https://threatpost.com/half-iot-devices-vulnerable-severe-attacks/153609/
Thomas, A., Gireesh Kumar, T., Mohan, A.K.: Neighbor attack detection in Internet of Things. In: Bhattacharyya, S., Chaki, N., Konar, D., Chakraborty, U.K., Singh, C.T. (eds.) Advanced Computational and Communication Paradigms. AISC, vol. 706, pp. 187–196. Springer, Singapore (2018). https://doi.org/10.1007/978-981-10-8237-5_18
Torii IoT Botnet (2018). https://blog.avast.com/new-torii-botnet-threat-research
Sai Charan, P.V., Gireesh Kumar, T., Mohan Anand, P.: Advance persistent threat detection using Long Short Term Memory (LSTM) neural networks. In: Somani, A.K., Ramakrishna, S., Chaudhary, A., Choudhary, C., Agarwal, B. (eds.) ICETCE 2019. CCIS, vol. 985, pp. 45–54. Springer, Singapore (2019). https://doi.org/10.1007/978-981-13-8300-7_5
Information about Muhstik IoT Botnet (2020). https://unit42.paloaltonetworks.com/muhstik-botnet-attacks-tomato-routers-to-harvest-new-iot-devices/
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Chunduri, H., Gireesh Kumar, T., Charan, P.V.S. (2021). A Multi Class Classification for Detection of IoT Botnet Malware. In: Chaubey, N., Parikh, S., Amin, K. (eds) Computing Science, Communication and Security. COMS2 2021. Communications in Computer and Information Science, vol 1416. Springer, Cham. https://doi.org/10.1007/978-3-030-76776-1_2
Download citation
DOI: https://doi.org/10.1007/978-3-030-76776-1_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-76775-4
Online ISBN: 978-3-030-76776-1
eBook Packages: Computer ScienceComputer Science (R0)