Abstract
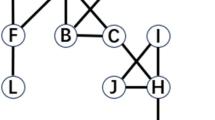
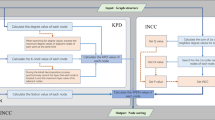
Aiming at the problem of the insufficient resolution and accuracy of the key node recognition methods in complex networks, a Comprehensive Degree Based Key Node Recognition Method (CDKNR) in complex networks is proposed. Firstly, the K-shell method is adopted to layer the network and obtain the K-shell (Ks) value of each node, and the influence of the global structure of the network is measured by the Ks value. Secondly, the concept of Comprehensive Degree (CD) is proposed, and a dynamically adjustable influence coefficient μi is set, and the Comprehensive Degree of each node is obtained by measuring the influence of the local structure of the network through the number of neighboring nodes and sub-neighboring nodes and influence coefficient μi. Finally, the importance of nodes is distinguished according to the Comprehensive Degree. Compared with several classical methods and risk assessment method, the experimental results show that the proposed method can effectively identify the key nodes, and has high accuracy and resolution in different complex networks. In addition, the CDKNR can provide a basis for risk assessment of network nodes, important node protection and risk disposal priority ranking of nodes in the network.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Yu, E.: A Re-ranking algorithm for identifying influential nodes in complex networks. IEEE Access 8, 211281–211290 (2020)
Yu, E.Y.: Identifying critical nodes in complex networks via graph convolutional networks. Knowl.-Based Syst. 198, 1–8 (2020)
Yan, X.L.: Identifying influential spreaders in complex networks based on entropy weight method and gravity law. Chin. Phys. B 29(4), 582–590 (2020)
Ullah, A.: Identification of Influential nodes via effective distance-based centrality mechanism in complex networks. Complexity 2021(11), 1–6 (2021)
Qiu, L.Q.: Ranking influential nodes in complex networks based on local and global structures. Appl. Intell. 1–14 (2021)
Liu, J.G.: Ranking the spreading influence in complex networks. Physica A Stat. Mech. Appl. 392(18), 4154–4159 (2013)
Zeng, A.: Ranking spreaders by decomposing complex networks. Phys. Lett. A 377(14), 1031–1035 (2013)
Namtirtha, A.: Weighted kshell degree neighborhood: a new method for identifying the influential spreaders from a variety of complex network connectivity structures. Expert Syst. Appl. 139, 1–15 (2020)
Wen, T.: Identification of influencers in complex networks by local information dimensionality. Inf. Sci. 512, 549–562 (2020)
Berahmand, K.: A new local and multidimensional ranking measure to detect spreaders in social networks. Comput. 101(11), 1711–1733 (2019)
Bae, J.: Identifying and ranking influential spreaders in complex networks by neighborhood coreness. Phys. A: Statal Mech. Appl. 395, 549–559 (2014)
Kitsak, M.: Identification of influential spreaders in complex networks. Nat. Phys. 6(11), 888–893 (2010)
Ibnoulouafi, A.: M-Centrality: identifying key nodes based on global position and local degree variation. J. Stat. Mech. Theory Exp. (7), 1–30 (2018)
Maji, G.: Influential spreaders identification in complex networks with potential edge weight based k-shell degree neighborhood method. J. Comput. Sci. 39, 1–9 (2020)
Maji, G.: A systematic survey on influential spreaders identification in complex networks with a focus on K-shell based techniques. Expert Syst. Appl. 161, 1–18 (2020)
Zhang, D.Y.: Identifying and quantifying potential super-spreaders in social networks. Sci. Rep. 9(1), 1–11 (2019)
China National Standardization Administration Committee: Information Security Risk Assessment Specification: GB/T 20984–2007[S]. China Standard Press, Beijing (2007)
Peng, J.H.: Utility based security risk measurement model. J. Beijing Univ. Posts Telecommun. 29(2), 59–61 (2006)
Acknowledgments
This work was supported by the Civil Aviation Joint Research Fund Project of the National Natural Science Foundation of China under Grant no. U1833107.
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Xie, L., Sun, H., Yang, H., Zhang, L. (2021). Comprehensive Degree Based Key Node Recognition Method in Complex Networks. In: Gao, D., Li, Q., Guan, X., Liao, X. (eds) Information and Communications Security. ICICS 2021. Lecture Notes in Computer Science(), vol 12918. Springer, Cham. https://doi.org/10.1007/978-3-030-86890-1_20
Download citation
DOI: https://doi.org/10.1007/978-3-030-86890-1_20
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-86889-5
Online ISBN: 978-3-030-86890-1
eBook Packages: Computer ScienceComputer Science (R0)