Abstract
\(\textsf {DY}^\star \) is a recently proposed formal verification framework for the symbolic security analysis of cryptographic protocol code written in the \(\textsf {F}^\star \) programming language. Unlike automated symbolic provers, \(\textsf {DY}^\star \) accounts for advanced protocol features like unbounded loops and mutable recursive data structures as well as low-level implementation details like protocol state machines and message formats, which are often at the root of real-world attacks. Protocols modeled in \(\textsf {DY}^\star \) can be executed, and hence, tested, and they can even interoperate with real-world counterparts. \(\textsf {DY}^\star \) extends a long line of research on using dependent type systems but takes a fundamentally new approach by explicitly modeling the global trace-based semantics within the framework, hence bridging the gap between trace-based and type-based protocol analyses. With this, one can uniformly, precisely, and soundly model, for the first time using dependent types, long-lived mutable protocol state, equational theories, fine-grained dynamic corruption, and trace-based security properties like forward secrecy and post-compromise security.
In this paper, we provide a tutorial-style introduction to \(\textsf {DY}^\star \) : We illustrate how to model and prove the security of the ISO-DH protocol, a simple key exchange protocol based on Diffie-Hellman.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Note that we format all \(\textsf {F}^\star \) code in this paper using a pretty-printer, i.e., some syntactic constructs are displayed using well-known mathematical symbols for readability, such as \(\rightarrow \), \(\forall \), \(\exists \), and \(\lambda \), instead of their textual representations.
- 2.
Note that the code excerpts we show in this paper are a bit simplified for presentation purposes (see [4] for the full code). Further note that we here use so-called refinement types provided by \(\textsf {F}^\star \) to further restrict types. For example, the result pk of the function vk is of type bytes, which is —by refinement— further required to satisfy the predicate
 , which states that the byte string pk must be labeled as public. We also make use of so-called implicit arguments, which are marked by
, which states that the byte string pk must be labeled as public. We also make use of so-called implicit arguments, which are marked by
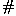 . In many cases, these parameters can be dropped when calling the function, as \(\textsf {F}^\star \) can derive them from the context.
. In many cases, these parameters can be dropped when calling the function, as \(\textsf {F}^\star \) can derive them from the context. - 3.
Sessions and versions are stored in two separate sequences s and v (of the same length). For each session
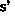 that is stored at index j in s, the corresponding version identifier
that is stored at index j in s, the corresponding version identifier
 is stored at the same index j in v.
is stored at the same index j in v.
References
Armando, A., et al.: The AVISPA tool for the automated validation of internet security protocols and applications. In: Etessami, K., Rajamani, S.K. (eds.) CAV 2005. LNCS, vol. 3576, pp. 281–285. Springer, Heidelberg (2005). https://doi.org/10.1007/11513988_27
Barbosa, M., et al.: SoK: computer-aided cryptography. In: IEEE S&P, pp. 777–795 (2021)
Bengtson, J., Bhargavan, K., Fournet, C., Gordon, A.D., Maffeis, S.: Refinement types for secure implementations. ACM TOPLAS 33(2), 8:1-8:45 (2011)
Bhargavan, K., et al.: DY\(^\star \) Code Repository. https://github.com/REPROSEC/dolev-yao-star/tree/festschrift-guttman
Bhargavan, K., et al.: DY\(^\star \): a modular symbolic verification framework for executable cryptographic protocol code. In: IEEE EuroS&P ’21, pp. 523–542 (2021)
Bhargavan, K., et al.: An in-depth symbolic security analysis of the ACME standard. In: ACM CCS ’21 (2021)
Bhargavan, K., Blanchet, B., Kobeissi, N.: Verified models and reference implementations for the TLS 1.3 standard candidate. In: IEEE S&P, pp. 483–502 (2017)
Bhargavan, K., Fournet, C., Gordon, A.D.: Modular verification of security protocol code by typing. In: ACM POPL, pp. 445–456 (2010)
Blanchet, B.: Security protocol verification: symbolic and computational models. In: POST, pp. 3–29 (2012)
Blanchet, B.: Modeling and verifying security protocols with the applied Pi calculus and ProVerif. Found. Trends Priv. Secur. 1(1–2), 1–135 (2016)
Cohn-Gordon, K., Cremers, C.J.F., Dowling, B., Garratt, L., Stebila, D.: A formal security analysis of the signal messaging protocol. In: IEEE EuroS&P, pp. 451–466 (2017)
Cremers, C., Horvat, M., Hoyland, J., Scott, S., van der Merwe, T.: A comprehensive symbolic analysis of TLS 1.3. In: ACM CCS, pp. 1773–1788 (2017)
Dolev, D., Yao, A.C.: On the security of public key protocols. IEEE Trans. Inf. Theor. 29(2), 198–208 (1983)
Dougherty, D.J., Guttman, J.D.: An algebra for symbolic diffie-hellman protocol analysis. In: Palamidessi, C., Ryan, M.D. (eds.) TGC 2012. LNCS, vol. 8191, pp. 164–181. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-41157-1_11
Fett, D., Küsters, R., Schmitz, G.: A comprehensive formal security analysis of OAuth 2.0. In: ACM CCS, pp. 1204–1215 (2016)
Fett, D., Küsters, R., Schmitz, G.: The web SSO standard OpenID connect: in-depth formal security analysis and security guidelines. In: IEEE CSF, pp. 189–202 (2017)
Guttman, J.: Security protocol design via authentication tests. In: IEEE CSFW, pp. 92–103 (2002)
Guttman, J., Thayer, F.: Protocol independence through disjoint encryption. In: IEEE CSFW, pp. 24–34 (2000)
Guttman, J.D., Thayer, F.J.: Authentication tests and the structure of bundles. Theor. Comput. Sci. 283(2), 333–380 (2002)
ISO/IEC 9798–3:2019(E): IT Security techniques - Entity authentication - Part 3: Mechanisms using digital signature techniques. Technical report (2019)
Kobeissi, N., Bhargavan, K., Blanchet, B.: Automated verification for secure messaging protocols and their implementations: a symbolic and computational approach. In: IEEE EuroS&P, pp. 435–450 (2017)
Krawczyk, H.: SIGMA: the ‘SIGn-and-MAc’ approach to authenticated diffie-hellman and its use in the IKE protocols. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 400–425. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45146-4_24
Lowe, G.: An attack on the needham-schroeder public-key authentication protocol. Inf. Process. Lett. 56(3), 131–133 (1995)
Lowe, G.: Breaking and fixing the needham-schroeder public-key protocol using FDR. In: TACAS, pp. 147–166 (1996)
Meier, S., Schmidt, B., Cremers, C., Basin, D.: The TAMARIN prover for the symbolic analysis of security protocols. In: Sharygina, N., Veith, H. (eds.) CAV 2013. LNCS, vol. 8044, pp. 696–701. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-39799-8_48
Needham, R.M., Schroeder, M.D.: Using encryption for authentication in large networks of computers. Commun. ACM 21(12), 993–999 (1978)
Ramsdell, J.D., Dougherty, D.J., Guttman, J.D., Rowe, P.D.: A hybrid analysis for security protocols with state. In: IFM, pp. 272–287 (2014)
REPROSEC: REPROSEC Project (2021). https://reprosec.org/
Swamy, N., Chen, J., Fournet, C., Strub, P., Bhargavan, K., Yang, J.: Secure distributed programming with value-dependent types. J. Funct. Program. 23(4), 402–451 (2013)
Swamy, N., et al.: Dependent types and multi-monadic effects in F\(^\star \). In: ACM POPL, pp. 256–270 (2016)
Thayer, F.J., Herzog, J.C., Guttman, J.D.: Strand spaces: proving security protocols correct. J. Comput. Secur. 7(1), 191–230 (1999)
Acknowledgments
This work was partially supported by the Deutsche Forschungsgemeinschaft (DFG) through Grants KU 1434/10-2 and KU 1434/12-1, the European Research Council (ERC) through Grant CIRCUS-683032, and the Office of Naval Research (ONR) through Grant N000141812618.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Bhargavan, K. et al. (2021). A Tutorial-Style Introduction to \(\textsf {DY}^\star \). In: Dougherty, D., Meseguer, J., Mödersheim, S.A., Rowe, P. (eds) Protocols, Strands, and Logic. Lecture Notes in Computer Science(), vol 13066. Springer, Cham. https://doi.org/10.1007/978-3-030-91631-2_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-91631-2_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-91630-5
Online ISBN: 978-3-030-91631-2
eBook Packages: Computer ScienceComputer Science (R0)





 , which states that the byte string
, which states that the byte string 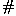 . In many cases, these parameters can be dropped when calling the function, as
. In many cases, these parameters can be dropped when calling the function, as 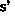 that is stored at index
that is stored at index  is stored at the same index
is stored at the same index