Abstract
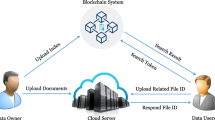
Nowadays there are more key technologies, such as cloud computing, big data, blockchain, and different techniques that process the data via a well-established purpose. The security of data should be a significant aspect of any type of system, therefore the systems should implement security techniques that solve this aspect. A relatively new encryption technique is searchable encryption, which enables the user to submit search queries based on chosen criteria (for example, keywords) to the cloud server on which the encrypted data (in the form of encrypted documents) is stored. Another emerging technology is blockchain, a decentralized approach for data sharing, based on a direct communication between two peers. To protect the data and its integrity, blockchain uses cryptographic mechanisms and strong mathematics computations as challenges that need to be solved by the nodes that adheres to the blockchain network. In this paper, we propose a searchable encryption scheme, which can be used in the cloud environment, based on elliptic curves and symmetric bilinear mapping for its algorithms and blockchain to store the indexes structure and to process the search query. Using elliptic curves, the proposed scheme is efficient, as it is proven in the literature that elliptic curve cryptography is usually faster than other encryption systems with the same level of security.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
2021 State of the Cloud Report |Flexera. https://info.flexera.com/CM-REPORT-State-of-the-Cloud?lead_source=Website%20Visitor&id=Blog
Gartner Predicts the Future of Cloud and Edge Infrastructure. www.gartner.com/smarterwithgartner/gartner-predicts-the-future-of-cloud-and-edge-infrastructure
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system. In: Decentralized Business Review, p. 21260 (2008)
Li, X., Jiang, P., Chen, T., Luo, X., Wen, Q.: A survey on the security of blockchain systems. Futur. Gener. Comput. Syst. 107, 841–853 (2020)
Washington, L.C.: Elliptic Curves: Number Theory and Cryptography. CRC Press, New York (2008)
Koblitz, N., Menezes, A.: Pairing-based cryptography at high security levels. In: Smart, N.P. (ed.) Cryptography and Coding 2005. LNCS, vol. 3796, pp. 13–36. Springer, Heidelberg (2005). https://doi.org/10.1007/11586821_2
Chen, Z., Wu, A., Li, Y., Xing, Q., Geng, S.: Blockchain-enabled public key encryption with multi-keyword search in cloud computing. In: Security and Communication Networks (2021)
Lauter, K.: The advantages of elliptic curve cryptography for wireless security. IEEE Wirel. Commun. 11(1), 62–67 (2004)
Shang, Z., Oya, S., Peter, A., Kerschbaum, F.: Obfuscated access and search patterns in searchable encryption. arXiv preprint arXiv:2102.09651 (2021)
Wang, H., Sui, G., Zhao, Y., Chen, K.: Efficient SSE with forward ID-privacy and authentication in the multi-data-owner settings. IEEE Access 9, 10443–10459 (2020)
Khazaei, S.: Fuzzy retrieval of encrypted data by multi-purpose data-structures. Signal Data Process. 17(4), 123–138 (2021)
Patranabis, S., Mukhopadhyay, D.: Forward and backward private conjunctive searchable symmetric encryption. Cryptology ePrint Archive (2020)
Song, D.X., Wagner, D., Perrig, A.: Practical techniques for searches on encrypted data. In: Proceeding 2000 IEEE Symposium on Security and Privacy, S&P 2000, pp. 44–55 (2000)
Goh, E.J.: Secure indexes. IACR Cryptol. ePrint Arch. (2003). https://eprint.iacr.org/2003/216
Stefanov, E., Papamanthou, C., Shi, E.: Practical dynamic searchable encryption with small leakage. Cryptology ePrint Archive (2013)
Etemad, M., Kupcu, A., Papamanthou, C., Evans, D.: Efficient dynamic searchable encryption with forward privacy. arXiv preprint arXiv:1710.00208 (2017)
Liu, Z., et al.: Eurus: towards an efficient searchable symmetric encryption with size pattern protection. IEEE Trans. Depend. Secure Comput., 1 (2020). https://doi.org/10.1109/TDSC.2020.3043754
Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 506–522. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24676-3_30
Park, D.J., Kim, K., Lee, P.J.: Public key encryption with conjunctive field keyword search. In: Lim, C.H., Yung, M. (eds.) WISA 2004. LNCS, vol. 3325, pp. 73–86. Springer, Heidelberg (2005). https://doi.org/10.1007/978-3-540-31815-6_7
Huang, Q., Li, H.: An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inf. Sci. 403, 1–14 (2017)
He, D., Ma, M., Zeadally, S., Kumar, N., Liang, K.: Certificateless public key authenticated encryption with keyword search for industrial internet of things. IEEE Trans. Industr. Inform. 14(8), 3618–3627 (2017)
Liu, Z.-Y., Tseng, Y.-F., Tso, R., Chen, Y.-C., Mambo, M.: Identity-certifying authority-aided identity-based searchable encryption framework in cloud system. IEEE Syst. J., 1–12 (2021). https://doi.org/10.1109/JSYST.2021.3103909
Szabo, N.: Formalizing and securing relationships on public networks. First Monday (1997)
Enge, A.: Bilinear pairings on elliptic curves. Enseign. Math. 61(1), 211–243 (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Mihailescu, M.I., Nita, S.L. (2022). Blockchain Search Using Searchable Encryption Based on Elliptic Curves. In: Barolli, L., Hussain, F., Enokido, T. (eds) Advanced Information Networking and Applications. AINA 2022. Lecture Notes in Networks and Systems, vol 451. Springer, Cham. https://doi.org/10.1007/978-3-030-99619-2_45
Download citation
DOI: https://doi.org/10.1007/978-3-030-99619-2_45
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-99618-5
Online ISBN: 978-3-030-99619-2
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)