Abstract
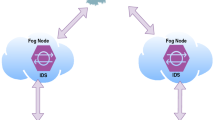
The fog-based attack detection systems can surpass cloud-based detection models due to their fast response and closeness to IoT devices. However, current fog-based detection systems are not lightweight to be compatible with ever-increasing IoMT big data and fog devices. To this end, a lightweight fog-based attack detection system is proposed in this study. Initially, a fog-based architecture is proposed for an IoMT system. Then the detection system is proposed which uses incremental ensemble learning, namely Weighted Hoeffding Tree Ensemble (WHTE), to detect multiple attacks in the network traffic of industrial IoMT system. The proposed model is compared to six incremental learning classifiers. Results of binary and multi-class classifications showed that the proposed system is lightweight enough to be used for the edge and fog devices in the IoMT system. The ensemble WHTE took trade-off between high accuracy and low complexity while maintained a high accuracy, low CPU time, and low memory usage.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Farahani, B., Firouzi, F., Chang, V., Badaroglu, M., Constant, N., Mankodiya, K.: Towards fog-driven IoT eHealth: promises and challenges of IoT in medicine and healthcare. Futur. Gener. Comput. Syst. 78, 659–676 (2018)
Alsubaei, F., Abuhussein, A., Shiva, S.: A framework for ranking IoMT solutions based on measuring security and privacy. In: Arai, K., Bhatia, R., Kapoor, S. (eds.) FTC 2018. AISC, vol. 880, pp. 205–224. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-02686-8_17
He, D., Ye, R., Chan, S., Guizani, M., Xu, Y.: Privacy in the Internet of Things for smart healthcare. IEEE Commun. Mag. 56(4), 38–44 (2018)
Yaacoub, J.-P.A., et al.: Securing internet of medical things systems: limitations, issues and recommendations. Futur. Gener. Comput. Syst. 105, 581–606 (2020). https://doi.org/10.1016/j.future.2019.12.02812
Rathore, H., Al-Ali, A.K., Mohamed, A., Du, X., Guizani, M.: A novel deep learning strategy for classifying different attack patterns for deep brain implants. IEEE Access 7, 24154–24164 (2019)
Hameed, S.S., et al.: A hybrid lightweight system for early attack detection in the IoMT fog. Sensors 21(24), 8289 (2021)
Cisco, C.: Fog computing and the Internet of Things: extend the cloud to where the things are. Элeктpoнный pecypc]. https://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-overview.pdf(дaтa oбpaщeния: 10.03. 2019) (2015)
Group, O.C.A.W.: OpenFog reference architecture for fog computing. OPFRA001 20817, 162 (2017)
Alrashdi, I., Alqazzaz, A., Alharthi, R., Aloufi, E., Zohdy, M.A., Ming, H.: FBAD: fog-based attack detection for IoT healthcare in smart cities. In: 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON). IEEE, pp. 0515–0522 (2019)
Kumar, P., Gupta, G.P., Tripathi, R.: An ensemble learning and fog-cloud architecture-driven cyber-attack detection framework for IoMT networks. Comput. Commun. 166, 110–124 (2021). https://doi.org/10.1016/j.comcom.2020.12.003
Hameed, S.S., Hassan, W.H., Latiff, L.A.: An efficient fog-based attack detection using ensemble of MOA-WMA for Internet of Medical Things. In: Saeed, F., Mohammed, F., Al-Nahari, A. (eds.) IRICT 2020. LNDECT, vol. 72, pp. 774–785. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-70713-2_70
Tavallaee, M., Bagheri, E., Lu, W., Ghorbani, A.A.: A detailed analysis of the KDD CUP 99 data set. In: 2009 IEEE symposium on computational intelligence for security and defense applications, pp. 1–6. IEEE (2009)
Sarhan, M., Layeghy, S., Moustafa, N., Portmann, M.: Netflow datasets for machine learning-based network intrusion detection systems. arXiv preprint arXiv:2011.09144 (2020)
Alaei, P., Noorbehbahani, F.: Incremental anomaly-based intrusion detection system using limited labeled data. In: 2017 3th International Conference on Web Research (ICWR), pp. 178–184. IEEE (2017)
Gama, J., Medas, P., Rodrigues, P.: Learning decision trees from dynamic data streams. In: Proceedings of the 2005 ACM Symposium on Applied computing, pp. 573–577 (2005)
Holmes, G., Kirkby, R., Pfahringer, B.: Stress-testing hoeffding trees. In: Jorge, A.M., Torgo, L., Brazdil, P., Camacho, R., Gama, J. (eds) European Conference on Principles of Data Mining and Knowledge Discovery, PKDD 2005. Lecture Notes in Computer Science, vol. 3721. Springer, Berlin, Heidelberg (2005). https://doi.org/10.1007/11564126_50
Oza, N.C., Russell, S.J.: Online bagging and boosting. In: International Workshop on Artificial Intelligence and Statistics, pp. 229–236. PMLR (2001)
Kolter, J.Z., Maloof, M.A.: Dynamic weighted majority: an ensemble method for drifting concepts. J. Mach. Learn. Res. 8, 2755–2790 (2007)
Littlestone, N., Warmuth, M.K.: The weighted majority algorithm. Inf. Comput. 108(2), 212–261 (1994)
Acknowledgments
The authors sincerely thank Universiti Teknologi Malaysia (UTM) under Malaysia Research University Network (MRUN) Vot 4L876, for the completion of the research. This work was also partially supported/funded by the Ministry of Higher Education under the Fundamental Research Grant Scheme (FRGS/1/2018/ICT04/UTM/01/1) and Universiti Tenaga Nasional (UNITEN). The work and the contribution were also supported by the SPEV project “Smart Solutions in Ubiquitous Computing Environments”, University of Hradec Kralove, Faculty of Informatics and Management, Czech Republic (under ID: UHK-FIM-SPEV-2022–2102). We are also grateful for the support of student Michal Dobrovolny in consultations regarding application aspects.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this paper
Cite this paper
Hameed, S.S., Selamat, A., Latiff, L.A., Razak, S.A., Krejcar, O. (2022). WHTE: Weighted Hoeffding Tree Ensemble for Network Attack Detection at Fog-IoMT. In: Fujita, H., Fournier-Viger, P., Ali, M., Wang, Y. (eds) Advances and Trends in Artificial Intelligence. Theory and Practices in Artificial Intelligence. IEA/AIE 2022. Lecture Notes in Computer Science(), vol 13343. Springer, Cham. https://doi.org/10.1007/978-3-031-08530-7_41
Download citation
DOI: https://doi.org/10.1007/978-3-031-08530-7_41
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-08529-1
Online ISBN: 978-3-031-08530-7
eBook Packages: Computer ScienceComputer Science (R0)