Abstract
Smart contracts are the building blocks of the “code is law” paradigm: the smart contract’s code indisputably describes how its assets are to be managed - once it is created, its code is typically immutable. Faulty smart contracts present the most significant evidence against the practicality of this paradigm; they are well-documented and resulted in assets worth vast sums of money being compromised. To address this issue, the Ethereum community proposed (i) tools and processes to audit/analyse smart contracts, and (ii) design patterns implementing a mechanism to make contract code mutable. Individually, (i) and (ii) only partially address the challenges raised by the “code is law” paradigm. In this paper, we combine elements from (i) and (ii) to create a systematic framework that moves away from “code is law” and gives rise to a new “specification is law” paradigm. It allows contracts to be created and upgraded but only if they meet a corresponding formal specification. The framework is centered around a trusted deployer: an off-chain service that formally verifies and enforces this notion of conformance. We have prototyped this framework, and investigated its applicability to contracts implementing three widely used Ethereum standards: the ERC20 Token Standard, ERC3156 Flash Loans and ERC1155 Multi Token Standard, with promising results.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
In fact, the function
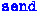 also delegates control to
also delegates control to
 but it does in such a restricted way that it cannot perform any side-effect computation. So, for the purpose of this paper and to simplify our exposition, we ignore this delegation.
but it does in such a restricted way that it cannot perform any side-effect computation. So, for the purpose of this paper and to simplify our exposition, we ignore this delegation. - 2.
The Ethereum concept of gas, i.e. execution resources, is purposely abstracted away/disregarded in our exposition.
- 3.
Instead of using the proxy pattern initialize function to initialise the state of the proxy instance, we place the code that carries out the desired initialisation directly into the proxy’s constructor. Our approach benefits from the inherent behaviour of constructors - which only execute once and at creation time - instead of having to implement this behaviour for the non-constructor function initialize. Our Trusted Deployer, available at https://github.com/formalblocks/safeevolution, automatically generates the code for such a proxy.
- 4.
The prototype is implemented as a standalone tool available at https://github.com/formalblocks/safeevolution. We do not provide a service running inside a Trusted Execution Environment yet but such a service will be provided in the future.
- 5.
All the instructions, the specifications, the sample contracts, and scripts used in this evaluation can be found at https://github.com/formalblocks/safeevolution.
References
Ethereum White Paper. https://github.com/ethereum/wiki/wiki/White-Paper Accessed 5 Aug 2022
Ahrendt, W., Bubel, R.: Functional verification of smart contracts via strong data integrity. In: Margaria, T., Steffen, B. (eds.) ISoLA 2020. LNCS, vol. 12478, pp. 9–24. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-61467-6_2
Alt, L., Reitwiessner, C.: SMT-based verification of solidity smart contracts. In: Margaria, T., Steffen, B. (eds.) ISoLA 2018. LNCS, vol. 11247, pp. 376–388. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03427-6_28
Antonino, P., Ferreira, J., Sampaion, A., Roscoe, A.W.:Specification is law: safe deployment of ethereum smart contracts - technical report. Technical report (2022). https://github.com/formalblocks/safeevolution
Antonino P., Roscoe, A. W.: Formalising and verifying smart contracts with solidifier: a bounded model checker for solidity. CoRR, abs/2002.02710 (2020)
Antonino P., Roscoe, A. W.: Solidifier: bounded model checking solidity using lazy contract deployment and precise memory modelling. In: Proceedings of the 36th Annual ACM Symposium on Applied Computing, pp. 1788–1797 (2021)
Atzei, N., Bartoletti, M., Cimoli, T.: A survey of attacks on ethereum smart contracts (SoK). In: Maffei, M., Ryan, M. (eds.) POST 2017. LNCS, vol. 10204, pp. 164–186. Springer, Heidelberg (2017). https://doi.org/10.1007/978-3-662-54455-6_8
Azzopardi, S., Ellul, J., Pace, G.J.: Monitoring smart contracts: contractlarva and open challenges beyond. In: Colombo, C., Leucker, M. (eds.) RV 2018. LNCS, vol. 11237, pp. 113–137. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03769-7_8
Barnett, M., Chang, B.-Y.E., DeLine, R., Jacobs, B., Leino, K.R.M.: Boogie: a modular reusable verifier for object-oriented programs. In: de Boer, F.S., Bonsangue, M.M., Graf, S., de Roever, W.-P. (eds.) FMCO 2005. LNCS, vol. 4111, pp. 364–387. Springer, Heidelberg (2006). https://doi.org/10.1007/11804192_17
Dickerson, T., Gazzillo, P., Herlihy, M., Saraph, V., Koskinen, E.: Proof-carrying smart contracts. In: Zohar, A., et al. (eds.) FC 2018. LNCS, vol. 10958, pp. 325–338. Springer, Heidelberg (2019). https://doi.org/10.1007/978-3-662-58820-8_22
Dihego, J., Antonino, P., Sampaio, A.: Algebraic laws for process subtyping. In: Groves, L., Sun, J. (eds.) ICFEM 2013. LNCS, vol. 8144, pp. 4–19. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-41202-8_2
Dihego, J., Sampaio, A., Oliveira, M.: A refinement checking based strategy for component-based systems evolution. J. Syst. Softw. 167, 110598 (2020)
Frank, J., Aschermann, C., Holz, T.: ETHBMC: a bounded model checker for smart contracts. In: 29th USENIX Security Symposium (USENIX Security 2020), pp. 2757–2774. USENIX Association (2020)
Grishchenko, I., Maffei, M., Schneidewind, C.: Ethertrust: sound static analysis of ethereum bytecode. Technische Universität Wien, Technical report (2018)
Groce, A., Feist, J., Grieco, G., Colburn, M.: What are the actual flaws in important smart contracts (and how can we find them)? In: Bonneau, J., Heninger, N. (eds.) FC 2020. LNCS, vol. 12059, pp. 634–653. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-51280-4_34
Hajdu, Á., Jovanović, D.: SMT-friendly formalization of the solidity memory model. In: FC 2020. LNCS, vol. 12059, pp. 224–250. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-44914-8_9
Hajdu, Á., Jovanović, D.: solc-verify: a modular verifier for solidity smart contracts. In: Chakraborty, S., Navas, J.A. (eds.) VSTTE 2019. LNCS, vol. 12031, pp. 161–179. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-41600-3_11
Hildenbrandt, E., et al.: KEVM: a complete formal semantics of the ethereum virtual machine. In: CSF 2018, pp. 204–217. IEEE (2018)
Bin, H., et al.: A comprehensive survey on smart contract construction and execution: paradigms, tools, and systems. Patterns 2(2), 100179 (2021)
Leino K. R. M.: This is boogie 2. Manuscript KRML 178(131), 9 (2008)
Liskov, B.H., Wing, J.M.: A behavioral notion of subtyping. ACM Trans. Program. Lang. Syst. 16(6), 1811–1841 (1994)
Liu, C., Liu, H., Cao, Z., Chen, Z., Chen, B., Roscoe, B.: ReGuard: finding reentrancy bugs in smart contracts. In: ICSE 2018, pp. 65–68. ACM (2018)
Luu, L., Chu, D.-H., Olickel, H., Saxena, P., Hobor, A.: Making smart contracts smarter. In: CCS 2016, pp. 254–269. ACM (2016)
Maene, P., Götzfried, J., de Clercq, R., Müller, T., Freiling, F., Verbauwhede, I.: Hardware-based trusted computing architectures for isolation and attestation. IEEE Trans. Comput. 67(3), 361–374 (2018)
Meyer, B.: Applying ‘design by contract’. Computer 25(10), 40–51 (1992)
Nguyen, T.D., Pham, L.H., Sun, J.: SGUARD: towards fixing vulnerable smart contracts automatically. In: 2021 IEEE Symposium on Security and Privacy (SP), pp. 1215–1229 (2021)
Permenev, A., Dimitrov, D., Tsankov, P., Drachsler-Cohen, D., Vechev, M.: VerX: safety verification of smart contracts. In: SP 2020, pp. 18–20 (2020)
Rodler, M., Li, W., Karame, G. O., Davi, L.: EVMPatch: timely and automated patching of ethereum smart contracts. In: (USENIX Security 2021), pp. 1289–1306. USENIX Association (2021)
AMD SEV-SNP. Strengthening VM isolation with integrity protection and more (2020)
Siegel, D.: Understanding the DAO attack. https://www.coindesk.com/understanding-dao-hack-journalists. Accessed 22 July 2021
OpenZeppelin team. Proxy Upgrade Pattern. https://docs.openzeppelin.com/upgrades-plugins/1.x/proxies. Accessed 5 Aug 2022
Tolmach, P., Li, Y., Lin, S.W., Liu, Y., Li, Z.: A survey of smart contract formal specification and verification. ACM Comput. Surv. 54(7), 1–38 (2021)
Torres, C. F., Jonker, H., State, R.: Elysium: Automagically healing vulnerable smart contracts using context-aware patching. CoRR, abs/2108.10071 (2021)
Tsankov, P., Dan, A., Drachsler-Cohen, D., Gervais, A., Buenzli, F., Vechev. M.: Securify: practical security analysis of smart contracts. In: CCS 2018, pp. 67–82. ACM (2018)
Vogelsteller, F., Buterin, V.: EIP-20: token standard. https://eips.ethereum.org/EIPS/eip-20. Accessed 5 Aug 2022
Wang, Y., et al.: Formal verification of workflow policies for smart contracts in azure blockchain. In: Chakraborty, S., Navas, J.A. (eds.) VSTTE 2019. LNCS, vol. 12031, pp. 87–106. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-41600-3_7
Wüst, K., Matetic, S., Egli, S., Kostiainen, K., Capkun, S.: ACE: asynchronous and concurrent execution of complex smart contracts. In: CCS 2020, pp. 587–600 (2020)
Yu, X.L., Al-Bataineh, O., Lo, D., Roychoudhury, A.: Smart contract repair. ACM Trans. Softw. Eng. Methodol. 29(4), 1–32 (2020)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Antonino, P., Ferreira, J., Sampaio, A., Roscoe, A.W. (2022). Specification is Law: Safe Creation and Upgrade of Ethereum Smart Contracts. In: Schlingloff, BH., Chai, M. (eds) Software Engineering and Formal Methods. SEFM 2022. Lecture Notes in Computer Science, vol 13550. Springer, Cham. https://doi.org/10.1007/978-3-031-17108-6_14
Download citation
DOI: https://doi.org/10.1007/978-3-031-17108-6_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-17107-9
Online ISBN: 978-3-031-17108-6
eBook Packages: Computer ScienceComputer Science (R0)





 also delegates control to
also delegates control to
 but it does in such a restricted way that it cannot perform any side-effect computation. So, for the purpose of this paper and to simplify our exposition, we ignore this delegation.
but it does in such a restricted way that it cannot perform any side-effect computation. So, for the purpose of this paper and to simplify our exposition, we ignore this delegation.