Abstract
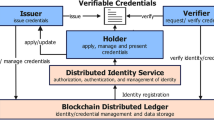
Self sovereign identity is a form of decentralised credential management. During credential verification, data exchange only happens between the data owner and the verifier without passing through any third parties. While this approach offers a privacy-centric solution, it poses a challenge. How do verifiers trust that the credential is vouched by a trusted source? More specifically, how do verifiers know that the issuer has the reputation or is authorised to issue the credential? In this paper, we propose a trust registry design that handles the aspect of human trust in self sovereign identity. We also introduce an incentivisation mechanism for the trust registry in order to motivate each stakeholder to participate actively and honestly.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Opengsn gas station network. https://docs.opengsn.org/#architecture. Accessed: 25 Feb 2022
Asgaonkar, A., Krishnamachari, B.: Token curated registries-a game theoretic approach. arXiv preprint arXiv:1809.01756 (2018)
Becker, G.: Merkle signature schemes, merkle trees and their cryptanalysis. Ruhr-University Bochum. Tech. Rep. 12, 19 (2008)
Blum, M., Feldman, P., Micali, S.: Non-interactive zero-knowledge and its applications. In: Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali, pp. 329–349 (2019)
Davie, M., Gisolfi, D., Hardman, D., Jordan, J., O’Donnell, D., Reed, D.: The trust over IP stack. IEEE Commun. Stand. Mag. 3(4), 46–51 (2019)
Du, W., Zhan, Z.: A practical approach to solve secure multi-party computation problems. In: Proceedings of the 2002 Workshop on New Security Paradigms, pp. 127–135 (2002)
Dumas, J.G., Lafourcade, P., Orfila, J.B., Puys, M.: Dual protocols for private multi-party matrix multiplication and trust computations. Comput. Secur. 71, 51–70 (2017)
Hasan, H.R., Salah, K., Jayaraman, R., Yaqoob, I., Omar, M.: Blockchain architectures for physical internet: a vision, features, requirements, and applications. IEEE Netw. 35(2), 174–181 (2020)
Impagliazzo, R., Naor, M.: Efficient cryptographic schemes provably as secure as subset sum. J. Cryptol. 9(4), 199–216 (1996). https://doi.org/10.1007/BF00189260
Jøsang, A., Gray, E., Kinateder, M.: Simplification and analysis of transitive trust networks. Web Intell. Agent Syst. Int. J. 4(2), 139–161 (2006)
Litos, O.S.T., Zindros, D.: Trust is risk: a decentralized financial trust platform. In: International Conference on Financial Cryptography and Data Security, pp. 340–356. Springer (2017)
Mühle, A., Grüner, A., Gayvoronskaya, T., Meinel, C.: A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 30, 80–86 (2018)
Naehrig, M., Lauter, K., Vaikuntanathan, V.: Can homomorphic encryption be practical? In: Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop, pp. 113–124 (2011)
Preukschat, A., Reed, D.: Self-Sovereign Identity. Manning Publications (2021)
Tobin, A., Reed, D.: The inevitable rise of self-sovereign identity. The Sovrin Foundation 29 (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Eer, K.J., Diaz, J., Kohlweiss, M. (2023). Bottom-Up Trust Registry in Self Sovereign Identity. In: Prieto, J., Benítez Martínez, F.L., Ferretti, S., Arroyo Guardeño, D., Tomás Nevado-Batalla, P. (eds) Blockchain and Applications, 4th International Congress . BLOCKCHAIN 2022. Lecture Notes in Networks and Systems, vol 595. Springer, Cham. https://doi.org/10.1007/978-3-031-21229-1_39
Download citation
DOI: https://doi.org/10.1007/978-3-031-21229-1_39
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-21228-4
Online ISBN: 978-3-031-21229-1
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)