Abstract
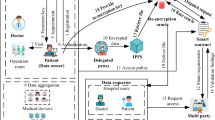
Contact tracing data contain highly sensitive information in which any form of leakage will significantly threaten the security and privacy of the individual. Encryption schemes can be used to ensure confidentiality; however, the usability of the retrieval system will be reduced considerably as the encrypted data does not support searchability. Hence, searchable encryption could be applied to contact tracing data. This paper introduces our implementation of a blockchain-based multi-keyword searchable encryption for COVID-19 contact tracing data. We used Advanced Encryption Standard as the symmetric primitive for encrypting datasets and Attribute-based Encryption as the asymmetric primitive for encrypting the search index. We incorporated Blockchain-based storage into our scheme to assure the integrity of the datasets and search index. It provides immutable storage and ensures data integrity and non-repudiation, as any form of access will be logged automatically. The results show that the scheme works efficiently without compromising any security goals. Compared to the existing searchable contact tracing schemes, it provides more features and maintains efficiency even if a large search index was used within the system.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The source code for the implementation can be accessed via GitHub repository: https://github.com/Wise-Neko/SWE1904870-FYP.
References
Chinese start-up leaked 400gb of scraped data exposing 200+ million facebook, instagram and linkedin users. https://www.safetydetectives.com/blog/socialarks-leak-report/. Accessed 11 Oct 2022
Microsoft leaves 250m customer service records open to the web. https://threatpost.com/microsoft-250m-customer-service-records-open/152086/. Accessed 11 Oct 2022
Mysejahtera. https://mysejahtera.malaysia.gov.my/. Accessed 30 Jan 2022
Tracetogether app. https://support.tracetogether.gov.sg/hc/en-sg. Accessed 30 Jan 2022
Avitabile, G., Botta, V., Iovino, V., Visconti, I.: Towards defeating mass surveillance and sars-cov-2: the pronto-c2 fully decentralized automatic contact tracing system. Cryptology ePrint Archive, Report 2020/493 (2020). https://ia.cr/2020/493
De Caro, A., Iovino, V.: jpbc: Java pairing based cryptography. In: 2011 IEEE Symposium on Computers and Communications (ISCC), pp. 850–855. IEEE (2011). https://doi.org/10.1109/ISCC.2011.5983948
Esteves-Verissimo, P., Decouchant, J., Völp, M., Esfahani, A., Graczyk, R.: Prilok: citizen-protecting distributed epidemic tracing. arXiv preprint arXiv:2005.04519 (2020)
Guo, W., Dong, X., Cao, Z., Shen, J.: Efficient attribute-based searchable encryption on cloud storage. In: Journal of Physics: Conference Series, vol. 1087, p. 052001. IOP Publishing (2018). https://doi.org/10.1088/1742-6596/1087/5/052001
Hee, Z., Salam, I.: Blockchain based contact tracing: a solution using bluetooth and sound waves for proximity detection. Cryptology ePrint Archive, Report 2022/209 (2022). https://eprint.iacr.org/2022/209
Jung, G., Lee, H., Kim, A., Lee, U.: Too much information: assessing privacy risks of contact trace data disclosure on people with covid-19 in south korea. Front. Public Health 8, 305 (2020). https://doi.org/10.3389/fpubh.2020.00305
McGrew, D., Viega, J.: The galois/counter mode of operation (GCM). Submission NIST Modes Oper. Process 20, 0278–0370 (2004)
Nabil, M., Sherif, A., Mahmoud, M., Alsmary, W., Alsabaan, M.: Privacy-preserving non-participatory surveillance system for covid-19-like pandemics. IEEE Access 9, 79911–79926 (2021). https://doi.org/10.1109/ACCESS.2021.3082910
Tahir, S., Tahir, H., Sajjad, A., Rajarajan, M., Khan, F.: Privacy-preserving covid-19 contact tracing using blockchain. J. Commun. Networks 23(5), 360–373 (2021). https://doi.org/10.23919/JCN.2021.000031
Tan, T.L., Salam, I., Singh, M.: Blockchain-based healthcare management system with two-side verifiability. PLOS ONE 17(4), 1–25 (2022). https://doi.org/10.1371/journal.pone.0266916
Troncoso, C., et al.: Decentralized privacy-preserving proximity tracing (2020). https://doi.org/10.48550/arXiv.2005.12273
Xu, H., Zhang, L., Onireti, O., Fang, Y., Buchanan, W.J., Imran, M.A.: Beeptrace: Blockchain-enabled privacy-preserving contact tracing for covid-19 pandemic and beyond. IEEE Internet Things J. 8(5), 3915–3929 (2020). https://doi.org/10.1109/JIOT.2020.3025953
Acknowledgements
This work was funded by Xiamen University Malaysia Research Fund (XMUMRF) under Grants XMUMRF/2019-C3/IECE/0005 and XMUMRF/2022-C9/IECE/0032.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix A Example of Search Function
Appendix A Example of Search Function
Table 4 shows a sample of the generated data, whereas Table 5 shows the example of keywords for the data. For each dataset, four keywords are registered for the corresponding data owner. The sample from Table 4 shows the datasets within a plaintext form, associated with the keywords in Table 5. If the data requester intends to search for this data file, they need to search for keywords that the data owner sets. For example, in this case, to retrieve the datasets from Table 4, the data requester can search either one of the four keywords: “OrganizationABC”, “Salak Tinggi”, “February”, and “2022” to get this file. The results will be more specific as more keywords are searched by the data requester. For example, if only “February” is searched, all datasets associated with “February” will be produced. They could be datasets with keywords (“February”, “2021”), or (“OrganizationABC”, “February”), and so on. Hence, if the data requester wishes for a specific set of datasets as the results, more keywords must be entered.
Table 6 shows an example of the organization array retrieved from the smart contract. In this example, the file hash value associated with the keyword"OrgA" is stored in indexes 0 and 3 in the structure. If the searched keyword is "OrgA", the tokens in the corresponding positions, i.e., 0 and 3, can be used to calculate whether the data requester fits the access policy. If the data requester is permitted access, they could request the ipfsHash value from the smart contract and access the encrypted file. If the data requester searches for two keywords, the same operation will be applied to two arrays, and their results will be compared. Table 7 shows an example of a location array retrieved from the smart contract. If the data requester’s desired keywords for organization value is “OrgA” and location value is “Klang”, the only fitted index is 0. Hence, in this case, only a token from index 0 needs to be computed to verify the access policy of the data requestor. The same logic applies to scenarios where more keywords were added within the system.
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this paper
Cite this paper
Ng, Z.Y., Salam, I. (2022). Blockchain-Based Multi-keyword Search on Encrypted COVID-19 Contact Tracing Data. In: Su, C., Gritzalis, D., Piuri, V. (eds) Information Security Practice and Experience. ISPEC 2022. Lecture Notes in Computer Science, vol 13620. Springer, Cham. https://doi.org/10.1007/978-3-031-21280-2_5
Download citation
DOI: https://doi.org/10.1007/978-3-031-21280-2_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-21279-6
Online ISBN: 978-3-031-21280-2
eBook Packages: Computer ScienceComputer Science (R0)