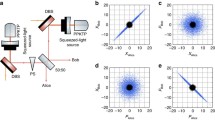
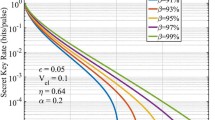
Abstract
Regarding the security concerns arising from the threat that quantum computing algorithms pose on some today’s most efficient and widely implemented public-key cryptographic systems, it has become necessary to find alternative cryptographic techniques to support private (or symmetric) key cryptographic schemes by means of key distribution. In this article we survey the emerging technology of quantum key distribution (QKD), which enables two separate parties to distill a random secret key only known by them and whose security relies on the principles of quantum physics, with the advantage of also enabling the detection of potential eavesdroppers. Among the different existing approaches to QKD, a distinction is made between discrete and continuous variable protocols. We focus here on continuous variable (CV-QKD) protocols, which consist of encoding information in optical coherent states that can be transmitted by fiber by means of off-the-shelf devices widely used in today’s telecommunications industry. An important advantage is that these components have a significantly lower cost in comparison to those used in other QKD protocols. The present study highlights some information-theoretic aspects of CV-QKD while putting special efforts into the security analysis of these protocols (such as parameter estimation or error correction techniques) derived from the practical implementation, as well as the challenges this technology faces in its still ongoing development.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
There are two variants of protocols for the preparation, transmission and measurement of states, PM (Prepare-and-Measure) and E-B (Entanglement-Based). Both are indistinguishable from the point of view of Bob and Eve, and equivalent concerning the security analysis. The second one, however, is more difficult to implement while the analysis of the first is more cumbersome, which therefore makes it convenient to benefit from their equivalences to simplify both the implementation and the analysis; the protocol is implemented in the PM version while the security analysis is performed considering a virtualization of the equivalent E-B protocol.
- 2.
It should be noted that, in the practical implementation, the protocol is initialized assuming typical experimental values -i.e. reasonable guesses- of T and \(\xi \) and the chosen value for the variance will be that which maximizes the a priori expected secret key rate. The real values will be estimated after transmission during the PE phase and the bounds on the secret key rate adjusted.
- 3.
Classes of attacks will be highlighted in the following section.
- 4.
Since standard telecommunications systems widely implement discrete constellations with 64, 128 and 256 states.
- 5.
As a result of the quantum nature of the exchanged states.
- 6.
For the reader unfamiliar with this notation, in the quantum formalism the Greek letter \(\rho \) is used to denote the density matrix -or density operator- that represents all the possibly available information about the state of a quantum object.
- 7.
\(\frac{\partial S(B;E)}{\partial t } < 0 \) y \(\frac{\partial S(B;E)}{\partial \sigma ^2 } > 0\).
- 8.
Explicit expressions for the three eigenvalues are known and can be found in [7].
- 9.
A typical value for the true excess noise can be \(\varDelta _{\textrm{m}} \xi = 1/100\). Similarly, it is often chosen \(\epsilon = \epsilon _{\textrm{PE}} = 10^{-10}\) and therefore \(z_{\epsilon _{\textrm{PE}}/2} \approx 6.5\).
- 10.
For example, the amount m of samples required to transmit a secret key rate over 100 km would be of the order of \(10^{10}\) [7].
References
Bennett, C.H., Brassard, G.: An update on quantum cyptography. In: Blakley, G.R., Chaum, D. (eds.) CRYPTO 1984. LNCS, vol. 196, pp. 475–480. Springer, Heidelberg (1985). https://doi.org/10.1007/3-540-39568-7_39
Brunner, H.H. et al.: A low-complexity heterodyne CV-QKD architecture. In: 2017 19th International Conference on Transparent Optical Networks (ICTON), pp. 1–4 (2017). https://doi.org/10.1109/ICTON.2017.8025030, ISSN: 2161-2064
Denys, A., Brown, P., Leverrier, A.: Explicit asymptotic secret key rate of continuous-variable quantum key distribution with an arbitrary modulation. Quantum 5, 540 (2021). https://doi.org/10.22331/q-2021-09-13-540. https://quantum-journal.org/papers/q-2021-09-13-540/, publisher: Verein zur Förderung des Open Access Publizierens in den Quantenwissenschaften
Grosshans, F., Grangier, P.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002). https://doi.org/10.1103/PhysRevLett.88.057902
Huang, D., Huang, P., Lin, D., Wang, C., Zeng, G.: High-speed continuous-variable quantum key distribution without sending a local oscillator. Opt. Lett. 40(16), 3695–3698 (2015) https://doi.org/10.1364/OL.40.003695. https://opg.optica.org/ol/abstract.cfm?uri=ol-40-16-3695, publisher: Optica Publishing Group
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P., Diamanti, E.: Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photonics 7(5), 378–381 (2013). https://doi.org/10.1038/nphoton.2013.63. https://www.nature.com/articles/nphoton.2013.63, number: 5 Publisher: Nature Publishing Group
Leverrier, A.: Theoretical study of continuous-variable quantum key distribution. phdthesis, Télécom ParisTech (2009). https://pastel.archives-ouvertes.fr/tel-00451021
Leverrier, A., García-Patrón, R., Renner, R., Cerf, N.J.: Security of continuous-variable quantum key distribution against general attacks. Phys. Rev. Lett. 110(3), (2013). https://doi.org/10.1103/PhysRevLett.110.030502, publisher: American Physical Society
Leverrier, A., Grangier, P.: Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 102(18),(2009). https://doi.org/10.1103/PhysRevLett.102.180504, publisher: American Physical Society
Pan, Y., et al.: Experimental demonstration of high-rate discrete-modulated continuous-variable quantum key distribution system. Opt. Lett. 47(13), 3307–3310 (2022) https://doi.org/10.1364/OL.456978. https://opg.optica.org/ol/abstract.cfm?uri=ol-47-13-3307, publisher: Optica Publishing Group
Ren, S., Yang, S., Wonfor, A., White, I., Penty, R.: Demonstration of high-speed and low-complexity continuous variable quantum key distribution system with local local oscillator. Sci. Rep. 11(1), 9454 (2021) https://doi.org/10.1038/s41598-021-88468-1. https://www.nature.com/articles/s41598-021-88468-1, number: 1 Publisher: Nature Publishing Group
Renner, R.: Security of quantum key distribution. phdthesis, ETH Zurich (2006). arXiv:quant-ph/0512258
Silberhorn, C., Ralph, T.C., Lütkenhaus, N., Leuchs, G.: Continuous variable quantum cryptography: beating the 3 DB loss limit. Phys. Rev. Lett. 89(16), (2002). https://doi.org/10.1103/PhysRevLett.89.167901, publisher: American Physical Society
Weedbrook, C., Lance, A.M., Bowen, W.P., Symul, T., Ralph, T.C., Lam, P.K.: Quantum cryptography without switching. Phys. Rev. Lett. 93(17),(2004). https://doi.org/10.1103/PhysRevLett.93.170504, publisher: American Physical Society
Zhang, Y., et al.: Continuous-variable QKD over 50 km commercial fiber. Quant. Sci. Technol. 4(3), (2019). https://doi.org/10.1088/2058-9565/ab19d1, publisher: IOP Publishing
Acknowledgements
This work had the support of Grant PID2020-118178RB-C22 funded by AEI/10.13039/501100011033, and by the Community of Madrid (Spain) under the CYNAMON project (P2018/TCS-4566), co-financed with European Social Fund and EU FEDER funds. We also acknowledge the support of the Spanish National Research Council (CSIC), project 202050E232, and CSIC’s Interdisciplinary Thematic Platform (PTI+) on Quantum Technologies (PTI-QTEP+). This study was supported by CSIC’s program for the Spanish Recovery, Transformation and Resilience Plan funded by the Recovery and Resilience Facility of the European Union, established by the Regulation (EU) 2020/2094; and MCIN with funding from European Union NextGenerationEU (PRTR-C17.I1).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Garcia-Callejo, A., Ruiz-Chamorro, A., Cano, D., Fernandez, V. (2023). A Review on Continuous-Variable Quantum Key Distribution Security. In: Bravo, J., Ochoa, S., Favela, J. (eds) Proceedings of the International Conference on Ubiquitous Computing & Ambient Intelligence (UCAmI 2022). UCAmI 2022. Lecture Notes in Networks and Systems, vol 594. Springer, Cham. https://doi.org/10.1007/978-3-031-21333-5_107
Download citation
DOI: https://doi.org/10.1007/978-3-031-21333-5_107
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-21332-8
Online ISBN: 978-3-031-21333-5
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)