Abstract
The Feistel construction is one of the most studied ways of building block ciphers. Several generalizations were proposed in the literature, leading to the Generalized Feistel Network (GFN) construction, in which the round function operates on each pair of blocks in parallel until all branches are permuted. At FSE’10, Suzaki and Minematsu studied the diffusion of such construction, raising the question of how many rounds are required so that each block of the ciphertext depends on all blocks of the plaintext. Exhausting all possible permutations up to 16 blocks, they observed that there were always optimal permutations mapping even-number input blocks to odd-number output blocks and vice versa. Recently, both Cauchois et al. and Derbez et al. proposed new algorithms to build optimal even-odd permutations for up to 36 blocks. In this paper, we present a new algorithm based on iterative path building to search for optimal Feistel permutation. This algorithm is much faster in exhausting optimal non-even-odd permutations than all the previous approaches. Our first result is a computational proof that no non-even-odd permutation reaches a better diffusion round than optimal even-odd permutations up to 32 blocks. Furthermore, it is well known that permutations with an optimal diffusion round do not always lead to optimal permutations against differential cryptanalysis. We investigate several new criteria to build permutations leading to more secure GFN.
The work presented in this article was funded by the French National Research Agency as part of the DeCrypt project (ANR- 18-CE39-0007).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Banik, S.: WARP : revisiting GFN for lightweight 128-bit block cipher. In: Dunkelman, O., Jacobson, Jr., M.J., O’Flynn, C. (eds.) SAC 2020. LNCS, vol. 12804, pp. 535–564. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-81652-0_21
Beaulieu, R., Shors, D., Smith, J., Treatman-Clark, S., Weeks, B., Wingers, L.: The SIMON and SPECK families of lightweight block ciphers. IACR Cryptology ePrint Archive 2013, 404 (2013). http://eprint.iacr.org/2013/404
Cauchois, V., Gomez, C., Thomas, G.: General diffusion analysis: How to find optimal permutations for generalized type-ii feistel schemes. IACR Trans. Symmetric Cryptol. 2019(1), 264–301 (2019). https://doi.org/10.13154/tosc.v2019.i1.264-301, https://doi.org/10.13154/tosc.v2019.i1.264-301
Derbez, P., Fouque, P.-A.: Automatic search of meet-in-the-middle and impossible differential attacks. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016. LNCS, vol. 9815, pp. 157–184. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53008-5_6
Derbez, P., Fouque, P., Lambin, B., Mollimard, V.: Efficient search for optimal diffusion layers of generalized feistel networks. IACR Trans. Symmetric Cryptol. 2019(2), 218–240 (2019). https://doi.org/10.13154/tosc.v2019.i2.218-240
DES: Data Encryption Standard. FIPS PUB 46, Federal information processing standards publication 46 (1977)
Nyberg, K.: Generalized feistel networks. In: Kim, K., Matsumoto, T. (eds.) ASIACRYPT 1996. LNCS, vol. 1163, pp. 91–104. Springer, Heidelberg (1996). https://doi.org/10.1007/BFb0034838
Shi, D., Sun, S., Derbez, P., Todo, Y., Sun, B., Hu, L.: Programming the demirci-selçuk meet-in-the-middle attack with constraints. In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018. LNCS, vol. 11273, pp. 3–34. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03329-3_1
Shibutani, K., Isobe, T., Hiwatari, H., Mitsuda, A., Akishita, T., Shirai, T.: Piccolo: an ultra-lightweight blockcipher. In: Preneel, B., Takagi, T. (eds.) CHES 2011. LNCS, vol. 6917, pp. 342–357. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-23951-9_23
Suzaki, T., Minematsu, K.: Improving the generalized feistel. In: Hong, S., Iwata, T. (eds.) FSE 2010. LNCS, vol. 6147, pp. 19–39. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13858-4_2
Suzaki, T., Minematsu, K., Morioka, S., Kobayashi, E.: TWINE: a lightweight block cipher for multiple platforms. In: Knudsen, L.R., Wu, H. (eds.) SAC 2012. LNCS, vol. 7707, pp. 339–354. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-35999-6_22
Zheng, Y., Matsumoto, T., Imai, H.: On the construction of block ciphers provably secure and not relying on any unproved hypotheses. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 461–480. Springer, New York (1990). https://doi.org/10.1007/0-387-34805-0_42
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix a Proofs of Proposition 3 and 4
Appendix a Proofs of Proposition 3 and 4
Proposition 3. Let \(\pi \) be an even-odd permutation \(\pi \), X-\(DR(\pi )\) is the smallest integer R such that: \(\forall c\in {V_{\textsf{o}}}, d\in {V_{\textsf{e}}}\), there are X paths of length \(R-3\) from c to d in \(G_\pi \).
Proof
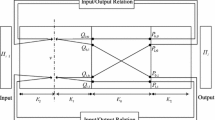
Let \(b,c\in {V_{\textsf{o}}}\) and \(a,d\in {V_{\textsf{e}}}\) with \((a,c),(d,b)\in E_{\pi }\). We have that \((a+1,a),(b,b-1)\in E_{\epsilon }\) with \(a+1\in {V_{\textsf{o}}}\) and \(b-1\in {V_{\textsf{e}}}\). Furthermore, we have \(g,h\in V\) such that \((b,g),(b-1,h)\in E_{\pi }\) (see the graph below with \(i=a+1\) and \(j=b-1\)).

1) From Definition 8, we know that there is X d-paths of length R from a to g, thus there is X paths of length \(R-3\) from c to d.
2) Now suppose that there is \(R'<X\)-\(DR(\pi )\) such that \(\forall ~ c\in {V_{\textsf{o}}},~ d\in {V_{\textsf{e}}}\) there is X paths of length \(R'-3\) from c to d. We then have X d-paths of length \(R'\) from i to g, from i to h and from a to h. Since we have these d-paths for all pairs \(a\in {V_{\textsf{e}}}, b\in {V_{\textsf{o}}}\) then we have full diffusion with X-\(DR(\pi )=R'\) and thus the contradiction X-\(DR(\pi )<X\)-\(DR(\pi )\). \(\square \)
Proposition 4. Let \(\pi \) be an even-odd permutation \(\pi \), X-\(SB(\pi )\) is the smallest integer R such that: \(\forall c\in {V_{\textsf{o}}}, d\in {V_{\textsf{e}}}\), there are X S-Boxes traversed by paths of length \(R-3\) from c to d in \(G_\pi \). A S-Box reached by two paths at the same time will be counted only once.
Proof
Let \(b,c\in {V_{\textsf{o}}}\) and \(a,d\in {V_{\textsf{e}}}\) with \((a,c),(d,b)\in E_{\pi }\). We have that \((a+1,a),(b,b-1)\in E_{\epsilon }\) with \(a+1\in {V_{\textsf{o}}}\) and \(b-1\in {V_{\textsf{e}}}\). Furthermore, we have \(g,h\in V\) such that \((b,g),(b-1,h)\in E_{\pi }\) (see the graph below with \(i=a+1\) and \(j=b-1\)).

1) From Definition 9, we know that there is X S-Boxes in all the d-paths of length R from a to g, thus there is X S-Boxes in all paths of length \(R-3\) from c to d.
2) Now suppose that there is \(R'<X\)-\(SB(\pi )\) such that \(\forall ~ c\in {V_{\textsf{o}}},~ d\in {V_{\textsf{e}}}\) there is X S-Boxes in all the paths of length \(R'-3\) from c to d. We then have X S-Boxes in all the d-paths of length \(R'\) from i to g, from i to h and from a to h. Since we have these d-paths for all pairs \(a\in {V_{\textsf{e}}}, b\in {V_{\textsf{o}}}\) then we have full diffusion with X-\(SB(\pi )=R'\) and thus the contradiction X-\(SB(\pi )<X\)-\(SB(\pi )\).
\(\square \)
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Delaune, S., Derbez, P., Gontier, A., Prud’homme, C. (2022). New Algorithm for Exhausting Optimal Permutations for Generalized Feistel Networks. In: Isobe, T., Sarkar, S. (eds) Progress in Cryptology – INDOCRYPT 2022. INDOCRYPT 2022. Lecture Notes in Computer Science, vol 13774. Springer, Cham. https://doi.org/10.1007/978-3-031-22912-1_5
Download citation
DOI: https://doi.org/10.1007/978-3-031-22912-1_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-22911-4
Online ISBN: 978-3-031-22912-1
eBook Packages: Computer ScienceComputer Science (R0)