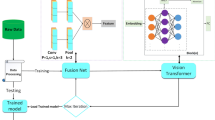
Abstract
Recent approaches based on feature transformation to images with further application of the pre-trained deep analysis models have been adopted for different cyber security tasks such as malware detection, intrusion and anomaly detection. The transfer learning (TL) is a technique for solving a new task using experience or knowledge transfer from a solution of the related task. Such approach allows speeding up the process of the problem solution or increasing its performance. This paper reviews existing approaches based on transfer learning with particular focus on data preprocessing step, discusses their advantages and disadvantages. The paper ends up with the proposed approach to feature extraction based on the traffic packets transformation to images, and evaluates its efficiency using Secure Water Treatment data set (SWaT) that models functioning of the modern water treatment facility.
This research is being supported by the grant of RSF #22-21-00724 in St. Petersburg Federal Research Center of the Russian Academy of Sciences.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Alrabaee, S., Karbab, E.M.B., Wang, L., Debbabi, M.: BinEye: towards efficient binary authorship characterization using deep learning. In: Sako, K., Schneider, S., Ryan, P.Y.A. (eds.) ESORICS 2019. LNCS, vol. 11736, pp. 47–67. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-29962-0_3
Chollet, F.: Xception: deep learning with depthwise separable convolutions. In: 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 1800–1807 (2017)
Chollet, F.: A transfer learning with deep neural network approach for network intrusion detection. Int. J. Intell. Comput. Res. (IJICR) 12, 087–1095 (2021)
Debnath, B., O’Brient, M., Kumar, S., Behera, A.: Attention-driven body pose encoding for human activity recognition. In: 2020 25th International Conference on Pattern Recognition (ICPR), pp. 5897–5904 (2021). https://doi.org/10.1109/ICPR48806.2021.9412487
Goh, J., Adepu, S., Junejo, K.N., Mathur, A.: A Dataset to support research in the design of secure water treatment systems. In: Havarneanu, G., Setola, R., Nassopoulos, H., Wolthusen, S. (eds.) CRITIS 2016. LNCS, vol. 10242, pp. 88–99. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-71368-7_8
He, K., Zhang, X., Ren, S., Sun, J.: Deep residual learning for image recognition. In: 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 770–778 (2016). https://doi.org/10.1109/CVPR.2016.90
Howard, A., et al.: Searching for mobilenetv3. In: 2019 IEEE/CVF International Conference on Computer Vision (ICCV), pp. 1314–1324 (2019). https://doi.org/10.1109/ICCV.2019.00140
Masum, M., Shahriar, H.: TL-NID: deep neural network with transfer learning for network intrusion detection. In: 2020 15th International Conference for Internet Technology and Secured Transactions (ICITST), pp. 1–7 (2020). https://doi.org/10.23919/ICITST51030.2020.9351317
Moustafa, N., Slay, J.: UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In: 2015 Military Communications and Information Systems Conference (MilCIS), pp. 1–6 (2015). https://doi.org/10.1109/MilCIS.2015.7348942
Nataraj, L., Karthikeyan, S., Jacob, G., Manjunath, B.S.: Malware images: visualization and automatic classification. In: Proceedings of the 8th International Symposium on Visualization for Cyber Security. VizSec 2011. Association for Computing Machinery, New York (2011). https://doi.org/10.1145/2016904.2016908
Noever, D.A., Noever, S.E.M.: Image classifiers for network intrusions. CoRR abs/2103.07765 (2021). https://arxiv.org/abs/2103.07765
Park, S., Kim, M., Lee, S.: Anomaly detection for http using convolutional autoencoders. IEEE Access 6, 70884–70901 (2018). https://doi.org/10.1109/ACCESS.2018.2881003
Rong, C., Gou, G., Cui, M., Xiong, G., Li, Z., Guo, L.: TransNet: unseen malware variants detection using deep transfer learning. In: Park, N., Sun, K., Foresti, S., Butler, K., Saxena, N. (eds.) SecureComm 2020. LNICST, vol. 336, pp. 84–101. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-63095-9_5
Russakovsky, O., et al.: ImageNet large scale visual recognition challenge. Int. J. Comput. Vision 115(3), 211–252 (2015). https://doi.org/10.1007/s11263-015-0816-y
Wang, W., et al.: Anomaly detection of industrial control systems based on transfer learning. Tsinghua Sci. Technol. 26(6), 821–832 (2021). https://doi.org/10.26599/TST.2020.9010041
Wu, P., Guo, H., Buckland, R.: A transfer learning approach for network intrusion detection. In: 2019 IEEE 4th International Conference on Big Data Analytics (ICBDA), pp. 281–285 (2019). https://doi.org/10.1109/ICBDA.2019.8713213
Zhao, J., Shetty, S., Pan, J.W., Kamhoua, C., Kwiat, K.: Transfer learning for detecting unknown network attacks. Int. J. Comput. Vision (2019). https://doi.org/10.1186/s13635-019-0084-4
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Golubev, S., Novikova, E. (2023). Image-Based Intrusion Detection in Network Traffic. In: Braubach, L., Jander, K., Bădică, C. (eds) Intelligent Distributed Computing XV. IDC 2022. Studies in Computational Intelligence, vol 1089. Springer, Cham. https://doi.org/10.1007/978-3-031-29104-3_6
Download citation
DOI: https://doi.org/10.1007/978-3-031-29104-3_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-29103-6
Online ISBN: 978-3-031-29104-3
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)