Abstract
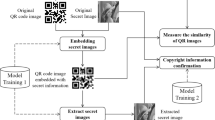
An application that significantly improves the traceability of the manufacturing sector and agriculture is the two-dimensional barcode (QR code). The QR code, however, is simple to copy and fake. Therefore, we suggest a novel strategy to prevent tampering with this code. The method entails two stages: concealing a security element in the QR code, and assessing how closely the QR code on the goods resembles genuine ones. For the first problem, error-correcting coding is used to encode and decode the secret feature in order to manage faults in noisy communication channels. A deep neural network is used to both conceal and decode the encoded data in the QR code. The suggested network has the ability to be resilient to actual distortions brought on by the printing and photographing processes. For the latter problem, we measure the similarity of QR codes using the Siamese network design. To assess if a QR code is real or false, the extracted secret feature and the outcome of the QR code similarity estimation are merged. With an average accuracy of 98%, the suggested method performs well and may be used to validate QR codes in practical applications.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
https://temchonggiavietnam.com/tem-chong-hang-gia/tem-chong-hang-gia-bo-cong-an/
Bose, R., Ray-Chaudhuri, D.: On a class of error correcting binary group codes. Inf. Control 3, 68–79 (1960)
He, K., Zhang, X., Ren, S., Sun, J.: Deep residual learning for image recognition. In: 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR) (2016)
Huiskes, M.J., Lew, M.S.: The mir flickr retrieval evaluation (2008)
Lancaster, I.: Anti-counterfeiting holograms (2009)
Luo, X., Zhan, R., Chang, H., Yang, F., Milanfar, P.: Distortion agnostic deep watermarking. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR) (2020)
Malla, B., Dugar, A.: Product authentication using QR codes: a mobile application to combat counterfeiting. Wireless Pers. Commun. 90, 381–398 (2016)
Schroff, F., Kalenichenko, D., Philbin, J.: Facenet: a unified embedding for face recognition and clustering. In: 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR) (2015)
Shih, F.Y.: Digital Watermarking and Steganography: Fundamentals and Techniques, 2nd edn. CRC Press, Boco Raton (2017)
Tran, T., Hong, S.: RFID anti-counterfeiting for retailing systems. J. Appl. Math. Phys. 3, 1 (2015)
Tuyls, P., Batina, L.: RFID-tags for anti-counterfeiting. In: Pointcheval, D. (ed.) CT-RSA 2006. LNCS, vol. 3860, pp. 115–131. Springer, Heidelberg (2006). https://doi.org/10.1007/11605805_8
Cu, V.L., Nguyen, T., Burie, J.C., Ogier, J.M.: A robust watermarking approach for security issue of binary documents using fully convolutional networks. Int. J. Document Anal. Recogn. (IJDAR) 23, 219–239 (2020)
Wan, S., Yang, G., Qi, L., Li, L., Yan, X., Lu, Y.: Multiple security anti-counterfeit applications to QR code payment based on visual secret sharing and QR code. Math. Biosc. Eng. 16, 6367–6385 (2019)
Xiao, C., Zhang, C., Zheng, C.: Fontcode: embedding information in text documents using glyph perturbation. CoRR (2017)
Xie, S., Tan, H.Z.: An anti-counterfeiting architecture for traceability system based on modified two-level quick response codes. Electronics 10, 320 (2021)
Yiu, N.C.K.: An NFC-enabled anti-counterfeiting system for wine industry. CoRR (2016)
Yiu, N.C.K.: Decentralizing supply chain anti-counterfeiting systems using blockchain technology. CoRR (2021)
Zhu, J., Kaplan, R., Johnson, J., Fei-Fei, L.: Hidden: hiding data with deep networks. In: Computer Vision - ECCV 2018 (2018)
Acknowledgements
This study is funded in part by the Can Tho University, Code: T2022-126.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Loc, C.V., De, T.C., Burie, JC., Ogier, JM. (2023). An Approach for Tamper-Proof QR Code Using Deep Learning Based-Data Hiding. In: Nguyen, N.T., et al. Recent Challenges in Intelligent Information and Database Systems. ACIIDS 2023. Communications in Computer and Information Science, vol 1863. Springer, Cham. https://doi.org/10.1007/978-3-031-42430-4_11
Download citation
DOI: https://doi.org/10.1007/978-3-031-42430-4_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-42429-8
Online ISBN: 978-3-031-42430-4
eBook Packages: Computer ScienceComputer Science (R0)