Abstract
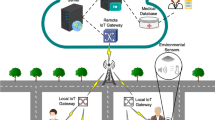
With the emergence of 5G (5th Generation mobile communication technology), the integration of AI (Artificial Intelligence) and IoT (Internet of Things) has gained momentum, facilitating the rapid development of AIoT (Artificial Intelligence of Things). Through sensor-enabled data collection, smart terminals are able to analyze, forecast, and make decisions based on data using AI technology. However, smart terminals may inadvertently contribute corrupted and forged data, or malicious terminals may intentionally spread false data, which poses a significant threat to the credibility of AIoT services. Therefore, evaluating the trustworthiness of smart terminals plays a crucial role in ensuring high-quality sensing data and reducing the risk of AIoT. To address this issue, we propose a novel cloud-edge-terminal collaborative AIoT trust model (CET-AoTM). CET-AoTM aggregates the cumulative experience attribute of smart terminals in AIoT and evaluates their credibility by leveraging the collaborative architecture of cloud-edge-terminal. In order to solve the challenge that a large number of new smart terminals lack historical interaction due to the high dynamic nature of AIoT, CET-AoTM evaluates the credibility of the terminals based on the fuzzy attributes such as location attribute, propagation attribute and communication attribute of the smart terminals as a supplement to the trust framework. And a demand-driven cloud-edge-terminal collaboration mechanism is designed to flexibly adapt to different service requirements. The experimental results show that the proposed method has high detection rate under low historical interaction scenario, which is not inferior to popular approaches at prensent.
First Author and Second Author contribute equally to this work.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bhattacharjee, S., Ghosh, N., Shah, V.K., Das, S.K.: QnQ: quality and quantity based unified approach for secure and trustworthy mobile crowdsensing. IEEE Trans. Mob. Comput. 19, 200–216 (2018)
Bouguettaya, A., Neiat, A.G., Bahutair, M.: Multi-perspective trust management framework for crowdsourced IoT services. IEEE Trans. Serv. Comput. 15, 2396–2409 (2021)
Chang, Z., Liu, S., Xiong, X., Cai, Z., Tu, G.: A survey of recent advances in edge-computing-powered artificial intelligence of things. IEEE Internet Things J. 8, 13849–13875 (2021)
Yu, C., Chen, J., Xia, G.: Coordinated control of intelligent fuzzy traffic signal based on edge computing distribution. Sensors (Basel, Switzerland) 22, 5953 (2022)
Chien, C.: Fuzzy logic in control systems: fuzzy logic controller. IEEE Trans. Syst. Man Cybern. 20, 404–418 (1990)
Olson, D.L., Delen, D.: Advanced Data Mining Techniques. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-76917-0
Duchi, J., Hazan, E., Singer, Y.: Adaptive subgradient methods for online learning and stochastic optimization. J. Mach. Learn. Res. 12, 257–269 (2011)
Hu, L., Miao, Y., Wu, G., Hassan, M.M., Humar, I.: iRobot-factory: an intelligent robot factory based on cognitive manufacturing and edge computing. Future Gener. Comput. Syst. 90, 569–577 (2019)
Jsang, A.: An algebra for assessing trust in certification chains. J. Acoust. Soc. Am. (1999)
Kamruzzaman, G.C.K.D.: IoT sensor numerical data trust model using temporal correlation. IEEE Internet Things J. 7, 2573–2581 (2020)
Krintz, C., Wolski, R., Golubovic, N., Bakir, F.: Estimating outdoor temperature from CPU temperature for IoT applications in agriculture. In: The Internet of Things (2018)
Liang, J., Zhang, M., Leung, V.C.M.: A reliable trust computing mechanism based on multi-source feedback and fog computing in social sensor cloud. IEEE Internet Things J. 7, 5481–5490 (2020)
Mohiuddin, I., Almajed, H.N., Guizani, N., Din, I.U., Al-Mogren, A.S.: FTM-IoMT: fuzzy-based trust management for preventing Sybil attacks in internet of medical things. IEEE Internet Things J. 8(6), 4485–4497 (2020)
Pourghebleh, B., Wakil, K., Navimipour, N.J.: A comprehensive study on the trust management techniques in the internet of things. IEEE Internet Things J. 6, 9326–9337 (2019)
Qureshi, K.N., Iftikhar, A., Bhatti, S.N., Piccialli, F., Jeon, G.: Trust management and evaluation for edge intelligence in the internet of things. Eng. Appl. Artif. Intell. 94, 103756 (2020)
Haykin, S., Network, N.: A comprehensive foundation. Neural Netw. 2, 41 (2004)
Simpson, S.V., Nagarajan, G.: A fuzzy based co-operative blackmailing attack detection scheme for edge computing nodes in MANET-IoT environment. Futur. Gener. Comput. Syst. 125(11), 544–563 (2021)
Truong, N.B., Lee, G.M., Um, T.W., Mackay, M.: Trust evaluation mechanism for user recruitment in mobile crowd-sensing in the internet of things. IEEE Trans. Inf. Forensics Secur. 14, 2705–2719 (2019)
Wang, F., Gong, W., Liu, J.: On spatial diversity in WiFi-based human activity recognition: a deep learning-based approach. IEEE Internet Things J. 6(2), 2035–2047 (2018)
Wei, L., Yang, Y., Wu, J., Long, C., Li, B.: Trust management for internet of things: a comprehensive study. IEEE Internet Things J. 9, 7664–7679 (2022)
Yu, C., Xia, G., Wang, Z.: Trust evaluation of computing power network based on improved particle swarm neural network. In: 2021 17th International Conference on Mobility, Sensing and Networking (MSN)
Acknowledgements
This work is supported by the National Natural Science Foundation of China under Grant 61972407.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Yu, C. et al. (2023). CET-AoTM: Cloud-Edge-Terminal Collaborative Trust Evaluation Scheme for AIoT Networks. In: Monti, F., Rinderle-Ma, S., Ruiz Cortés, A., Zheng, Z., Mecella, M. (eds) Service-Oriented Computing. ICSOC 2023. Lecture Notes in Computer Science, vol 14420. Springer, Cham. https://doi.org/10.1007/978-3-031-48424-7_11
Download citation
DOI: https://doi.org/10.1007/978-3-031-48424-7_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-48423-0
Online ISBN: 978-3-031-48424-7
eBook Packages: Computer ScienceComputer Science (R0)