Abstract
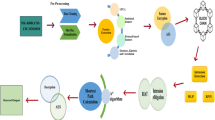
Detecting and securing against malicious activity in cyber-physical systems (CPS) while optimizing resource utilization pose significant challenges. In this paper we propose an innovative approach that combines water wave optimization (WWO) for feature selection, deep recurrent neural networks (RNN) for training, and blockchain-based security to enhance the efficiency and accuracy of malicious activity detection in CPS. The WWO technique is applied to extract the most relevant features from the intricate and high-dimensional CPS data, effectively reducing dimensionality and improving computational efficiency. These selected features are then inputted into a deep RNN model, capable of capturing temporal dependencies and patterns within the data, thus enabling effective identification of malicious activities. To strengthen the security of the CPS system, we integrate blockchain technology as a foundation for secure data storage and management. By leveraging blockchain, we establish a decentralized and tamper-proof ledger that ensures the integrity and transparency of detected activities. The immutability of the blockchain provides robust protection against malicious tampering or unauthorized modifications, enhancing the overall security of the CPS system. We evaluate our proposed system architecture using a real-world CPS dataset, showcasing its superiority in accuracy and efficiency compared to traditional feature selection methods. The WWO-based feature selection significantly reduces the feature space while preserving critical discriminative information necessary for detection. The deep RNN model, trained on the selected features, achieves high accuracy in classifying and identifying malicious activities. Moreover, our approach exhibits robustness and adaptability in the face of evolving attack patterns. By training the deep RNN on a diverse and extensive dataset, the model becomes more resilient to unknown attacks, thereby enhancing CPS security. The integration of water wave optimization for feature selection, deep RNN for training, and blockchain-based security offers a promising avenue for improving malicious activity detection in CPS.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References:
Liu, Y., Chen, G.: A comparative study of feature selection techniques for malicious activity detection in cyber-physical systems. IEEE Trans. Industr. Inf. 14(10), 4455–4464 (2018)
Sharma, A., Bali, K.: Malicious activity detection in cyber-physical systems using recurrent neural networks. In: Proceedings of the International Conference on Machine Learning, Big Data, and Business Analytics, pp. 192–204 (2019)
Yan, H., Zhang, J.: Blockchain-enabled security for cyber-physical systems: a review. IEEE Trans. Industr. Inf. 15(1), 503–510 (2019)
Wang, X., Chen, J., Cao, L.: A hybrid feature selection and machine learning framework for malicious activity detection in cyber-physical systems. Futur. Gener. Comput. Syst. 76, 69–79 (2017)
Gai, K., Qian, Y.: Blockchain-based security for cyber-physical systems: a survey. IEEE Trans. Industr. Inf. 16(6), 4441–4451 (2020)
Liu, W., Zhu, X., Cheng, X.: Hybrid feature selection algorithm for malicious activity detection in cyber-physical systems. J. Ambient. Intell. Humaniz. Comput. 9(5), 1763–1774 (2018)
Raza, S., Sher, M., Malik, A.: Secure data sharing framework for cyber-physical systems based on blockchain technology. IEEE Trans. Industr. Inf. 15(6), 3480–3488 (2019)
Bao, W., Xu, J., Cao, J.: A blockchain-based access control system for cyber-physical systems. IEEE Trans. Industr. Inf. 14(11), 4870–4879 (2018)
Almohaimeed, A., Alharbi, A., Alzahrani, A.: A hybrid deep learning model for malicious activity detection in cyber-physical systems. Futur. Gener. Comput. Syst. 112, 238–247 (2020)
Li, X., Huang, X., Wang, X.: Malicious activity detection in cyber-physical systems using machine learning and blockchain technology. In: Proceedings of the International Conference on Machine Learning and Cybernetics, pp. 1087–1092 (2017)
Zhang, Z., Guo, Y., Li, S.: Feature selection and malicious activity detection in cyber-physical systems using genetic algorithm and machine learning. IEEE Access 7, 82468–82478 (2019)
Zhao, Y., Han, Z., Cao, Y.: An intelligent intrusion detection system for cyber-physical systems based on deep learning. IEEE Trans. Industr. Inf. 14(7), 3206–3215 (2018)
Xu, C., Dai, Y.: Blockchain-based auditable access control for cyber-physical Systems. IEEE Trans. Industr. Inf. 15(1), 463–472 (2019)
Karim, A., Abbas, H.: A hybrid model for malicious activity detection in cyber-physical systems using particle swarm optimization and deep learning. Futur. Gener. Comput. Syst. 87, 693–703 (2018)
Li, C., Yang, F., Zhang, W.: Blockchain-based Integrity Verification for Cyber-Physical Systems. IEEE Trans. Industr. Inf. 16(5), 3194–3203 (2020)
Zhao, Y., Han, Z.: Deep learning-based malicious activity detection in industrial cyber-physical systems. IEEE Trans. Industr. Inf. 16(1), 188–198 (2020)
Wang, T., Zhang, J.: A blockchain-enabled trust model for secure data sharing in cyber-physical systems. IEEE Trans. Industr. Inf. 16(3), 1892–1901 (2020)
Zhou, C., Liu, F.: Malicious activity detection in cyber-physical systems using hybrid particle swarm optimization and extreme learning machine. IEEE Access 6, 30886–30894 (2018)
Yang, X., Xu, D., Ren, K.: Blockchain-based data integrity auditing for cyber-physical systems. IEEE Trans. Industr. Inf. 15(10), 5533–5543 (2019)
Li, Y., Jiang, X., Dai, S.: A deep learning approach for intrusion detection using recurrent neural networks. In: 2017 IEEE Trustcom/BigDataSE/ICESS, pp. 278–285 (2017)
Kim, Y., Park, J., Kim, J., Kim, S.: Long short-term memory recurrent neural network for network traffic classification. In: 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), pp. 201–206 (2016)
Abdulhamid, S.M., Atiya, A.F.: Feature selection with a novel improved water wave optimization algorithm. In: 2018 10th International Conference on Machine Learning and Computing (ICMLC), pp. 150–155 (2018)
Buczak, A.L., Guven, E.: A survey of network flow applications. J. Netw. Comput. Appl. 60, 125–144 (2016)
Abdessalem, R.B., Nolle, L.: Detecting malicious activity in IoT networks using machine learning algorithms. In: Proceedings of the 11th International Conference on Availability, Reliability and Security (ARES), pp. 55–63 (2016)
Ronao, C.A., Cho, S.B.: Human activity recognition with smartphone sensors using deep learning neural networks. Expert Syst. Appl. 59, 235–244 (2016)
Saxe, J., McCloskey, S., Berger, J.: Deep neural network based intrusion detection in software defined networking. In: 2015 11th International Conference on Network and Service Management (CNSM), pp. 400–405 (2015)
Salehahmadi, Z., Dehghantanha, A., Choo, K.K.R., Conti, M.: Intrusion detection system for the Internet of Things utilizing a deep learning approach. J. Netw. Comput. Appl. 103, 1–10 (2018)
Erkol, B., Yilmaz, Y., Bicakci, K., Anarim, E.: Anomaly detection in IoT networks using deep neural networks. In: Proceedings of the 8th International Conference on Internet of Things, pp. 68–73 (2017)
Liu, Y., Xiang, Y., Fan, Y.: A survey of deep neural network architectures and their applications. Neurocomputing 234, 11–26 (2018)
Tan, S.H., Ristaniemi, T.: Recent advances in feature selection and its applications. Expert Syst. Appl. 42(8), 4378–4409 (2015)
Abdullah, R., Tawalbeh, L., Khreishah, A.: Survey of machine learning algorithms for network anomaly detection. J. Netw. Comput. Appl. 60, 19–31 (2019)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Kamble, A., Malemath, V.S., Muddapu, S. (2024). Blockchain-Enhanced Federated Learning for Secure Malicious Activity Detection in Cyber-Physical Systems. In: Santosh, K., et al. Recent Trends in Image Processing and Pattern Recognition. RTIP2R 2023. Communications in Computer and Information Science, vol 2027. Springer, Cham. https://doi.org/10.1007/978-3-031-53085-2_25
Download citation
DOI: https://doi.org/10.1007/978-3-031-53085-2_25
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-53084-5
Online ISBN: 978-3-031-53085-2
eBook Packages: Computer ScienceComputer Science (R0)