Abstract
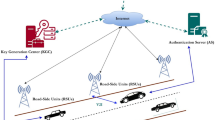
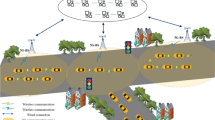
The data of applications in connected and autonomous vehicles are important, which is usually collected by service providers to improve their services, such as object detection model. But, wireless communication is susceptible to various kinds of attacks. Thus, the data of the application module needs to be securely shared to the corresponding service provider. However, current schemes are with limited performance while a service provider collects multiple application data at the same time. By adopting signcryption and chaotic map, an efficient authentication and key agreement scheme is proposed, while batch authentication is achieved for efficient message authentication of multiple applications, and the efficient revocation is realized based on Chinese remainder theorem under the assistance of trusted execution environment supported vehicle computing/communication unit. The formal security proof shows that the scheme is secure under the random oracle model, and the experiment results shows that the scheme is more efficient than related schemes and can meet the requirements of CAV.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The applications here can also be in-vehicle modules connected by CAN bus.
References
Kim, K., Kim, J.S., Jeong, S., Park, J.H., Kim, H.K.: Cybersecurity for autonomous vehicles: review of attacks and defense. Comput. Secur. 103, 102150 (2021)
Zhang, Q., et al.: Openvdap: an open vehicular data analytics platform for cavs. In: 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), pp. 1310–1320 (2018)
Sroka, P., Kliks, A.: Towards edge intelligence in the automotive scenario: a discourse on architecture for database-supported autonomous platooning. J. Commun. Netw. 24(2), 192–208 (2022)
Liu, S., Tang, J., Zhang, Z., Gaudiot, J.: Computer architectures for autonomous driving. Computer 50(8), 18–25 (2017)
He, J., et al.: Cooperative connected autonomous vehicles (CAV): research, applications and challenges. In: 2019 IEEE 27th International Conference on Network Protocols (ICNP), pp. 1–6. IEEE (2019)
Ma, Y., Wang, Z., Yang, H., Yang, L.: Artificial intelligence applications in the development of autonomous vehicles: a survey. IEEE/CAA J. Automatica Sinica 7(2), 315–329 (2020)
Wei, W., Yang, R., Gu, H., Zhao, W., Chen, C., Wan, S.: Multi-objective optimization for resource allocation in vehicular cloud computing networks. IEEE Trans. Intell. Transp. Syst. 23(12), 25536–25545 (2021)
Cui, J., Wei, L., Zhang, J., Xu, Y., Zhong, H.: An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 20(5), 1621–1632 (2018)
Zhang, Q., Wu, J., Zhong, H., He, D., Cui, J.: Efficient anonymous authentication based on physically unclonable function in industrial internet of things. IEEE Trans. Inf. Forensics Secur. 18, 233–247 (2023)
Li, T., Shang, M., Wang, S., Filippelli, M., Stern, R.: Detecting stealthy cyberattacks on automated vehicles via generative adversarial networks. In: 2022 IEEE 25th International Conference on Intelligent Transportation Systems (ITSC), pp. 3632–3637. IEEE (2022)
Zhang, Q., Zhong, H., Cui, J., Ren, L., Shi, W.: Ac4av: a flexible and dynamic access control framework for connected and autonomous vehicles. IEEE Internet Things J. 8(3), 1946–1958 (2021)
Mousavinejad, E., Yang, F., Han, Q.L., Ge, X., Vlacic, L.: Distributed cyber attacks detection and recovery mechanism for vehicle platooning. IEEE Trans. Intell. Transport. Syst. 21, 3821–3834 (2019)
Chattopadhyay, A., Lam, K.Y., Tavva, Y.: Autonomous vehicle: security by design. IEEE Trans. Intell. Transport. Syst. 22, 7015–7029 (2020)
Wazid, M., Das, A.K., Kumar, N., Vasilakos, A.V., Rodrigues, J.J.: Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 6(2), 3572–3584 (2018)
Bagga, P., Das, A.K., Wazid, M., Rodrigues, J.J., Choo, K.K.R., Park, Y.: On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 70(2), 1736–1751 (2021)
Ting, P., Tsai, J., Wu, T.: Signcryption method suitable for low-power IoT devices in a wireless sensor network. IEEE Syst. J. 12(3), 2385–2394 (2018)
Mandal, S., Bera, B., Sutrala, A.K., Das, A.K., Choo, K.R., Park, Y.: Certificateless-signcryption-based three-factor user access control scheme for IoT environment. IEEE Internet Things J. 7(4), 3184–3197 (2020)
Roy, S., Chatterjee, S., Das, A.K., Chattopadhyay, S., Kumari, S., Jo, M.: Chaotic map-based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing internet of things. IEEE Internet Things J. 5(4), 2884–2895 (2018)
Qiu, S., Wang, D., Xu, G., Kumari, S.: Practical and provably secure three-factor authentication protocol based on extended chaotic-maps for mobile lightweight devices. IEEE Trans. Depend. Secure Comput. 19(2), 1338–1351 (2022)
Tangade, S., Manvi, S.S., Lorenz, P.: Decentralized and scalable privacy-preserving authentication scheme in vanets. IEEE Trans. Veh. Technol. 67(9), 8647–8655 (2018)
Cui, J., Yu, J., Zhong, H., Wei, L., Liu, L.: Chaotic map-based authentication scheme using physical unclonable function for internet of autonomous vehicle. IEEE Trans. Intell. Transp. Syst. 24(3), 3167–3181 (2023)
Xu, G., Dong, J., Ma, C., Liu, J., Cliff, U.G.O.: A certificateless signcryption mechanism based on blockchain for edge computing. IEEE Internet Things J. (2022)
Bergamo, P., D’Arco, P., De Santis, A., Kocarev, L.: Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst. I Regul. Pap. 52(7), 1382–1393 (2005)
Zhang, L.: Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 37(3), 669–674 (2008)
Abbasinezhad-Mood, D., Ostad-Sharif, A., Mazinani, S.M., Nikooghadam, M.: Provably-secure escrow-less Chebyshev chaotic map-based key agreement protocol for vehicle to grid connections with privacy protection. IEEE Trans. Ind. Inf. 16, 7287–7294 (2020)
Lu, R., Heung, K., Lashkari, A.H., Ghorbani, A.A.: A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT. IEEE Access 5, 3302–3312 (2017)
Zhang, J., Cui, J., Zhong, H., Chen, Z., Liu, L.: PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Depend. Secure Comput. 18, 722–735 (2019)
Xiong, H., Chen, J., Mei, Q., Zhao, Y.: Conditional privacy-preserving authentication protocol with dynamic membership updating for vanets. IEEE Trans. Depend. Secure Comput. 19, 2089–2104 (2020)
Maene, P., Götzfried, J., De Clercq, R., Müller, T., Freiling, F., Verbauwhede, I.: Hardware-based trusted computing architectures for isolation and attestation. IEEE Trans. Comput. 67(3), 361–374 (2017)
Zhang, Q., Zhong, H., Shi, W., Liu, L.: A trusted and collaborative framework for deep learning in IoT. Comput. Netw. 193, 108055 (2021)
Acknowledgments
The work was supported in part by Open Fund of Anhui Province Key Laboratory of Cyberspace Security Situation Awareness and Evaluation, in part by the National Natural Science Foundation of China under Grant 62272002, Grant 62202005, and Grant 62202008, in part by the Excellent Youth Foundation of Anhui Scientific Committee under Grant 2108085J31, in part by the Natural Science Foundation of Anhui Province, China under Grant 2208085QF198.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Li, Y., Zhang, Q., Cao, W., Cui, J., Zhong, H. (2024). An Efficient Authentication and Key Agreement Scheme for CAV Internal Applications. In: Gao, H., Wang, X., Voros, N. (eds) Collaborative Computing: Networking, Applications and Worksharing. CollaborateCom 2023. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 562. Springer, Cham. https://doi.org/10.1007/978-3-031-54528-3_23
Download citation
DOI: https://doi.org/10.1007/978-3-031-54528-3_23
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-54527-6
Online ISBN: 978-3-031-54528-3
eBook Packages: Computer ScienceComputer Science (R0)