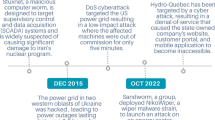
Abstract
In recent years, there has been an increasing need to understand the SCADA networks that oversee our essential infrastructures. While previous studies have focused on networks in a single sector, few have taken a comparative approach across multiple critical infrastructures. This paper dissects operational SCADA networks of three essential services: power grids, gas distribution, and water treatment systems. Our analysis reveals some distinct and shared behaviors of these networks, shedding light on their operation and network configuration.
Our findings challenge some of the previous perceptions about the uniformity of SCADA networks and emphasize the need for specialized approaches tailored to each critical infrastructure. With this research, we pave the way for better network characterization for cybersecurity measures and more robust designs in intrusion detection systems.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
S-format is a control field packet used for controlling the transport of information (ASDU packets). This protects against loss and duplication of I-format messages.
- 2.
U-format control field used to control the connection between stations. It is used as a start-stop mechanism for information flow. As a heartbeat to check connection. Also, as a mechanism for changeover between connections without loss of data when there are multiple connections available between stations.
- 3.
w specifies the maximum number of received I-format APDUs that the receiver should ACK at the latest. e.g., a \(w=8\) means that the controller will send to the agent an S-format message to ACK the last 8 I-format messages it receives.
References
IEC 60870-5-104, June 2006. https://webstore.iec.ch/publication/3746
Modbus application protocol specification v1.1b3, April 2012. https://www.modbus.org
Babay, A., et al.: Deploying intrusion-tolerant SCADA for the power grid. In: 2019 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), pp. 328–335 (2019). https://doi.org/10.1109/DSN.2019.00043
Babay, A., Tantillo, T., Aron, T., Platania, M., Amir, Y.: Network-attack-resilient intrusion-tolerant SCADA for the power grid. In: 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), pp. 255–266 (2018). https://doi.org/10.1109/DSN.2018.00036
Barbosa, R.R.R., Sadre, R., Pras, A.: Difficulties in modeling SCADA traffic: a comparative analysis. In: Taft, N., Ricciato, F. (eds.) PAM 2012. LNCS, vol. 7192, pp. 126–135. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-28537-0_13
Barbosa, R.R.R., Sadre, R., Pras, A.: Exploiting traffic periodicity in industrial control networks. Int. J. Crit. Infrastruct. Prot. 13, 52–62 (2016). https://doi.org/10.1016/j.ijcip.2016.02.004. https://linkinghub.elsevier.com/retrieve/pii/S1874548216300221
Cheung, S., Dutertre, B., Fong, M., Lindqvist, U., Valdes, A., Skinner, K.: Using model-based intrusion detection for SCADA networks. In: Proceeding of the SCADA Security Scientific Symposium, p. 12 (2007)
Clarke, G., Reynders, D., Wright, E.: Practical Modern SCADA Protocols: DNP3, 60870.5 and Related Systems, January 2004
Formby, D., Walid, A., Beyah, R.: A case study in power substation network dynamics. Proc. ACM Meas. Anal. Comput. Syst. 1(1) (2017). https://doi.org/10.1145/3084456
Hadžiosmanović, D., Sommer, R., Zambon, E., Hartel, P.H.: Through the eye of the PLC: semantic security monitoring for industrial processes, pp. 126–135 (2014). https://doi.org/10.1145/2664243.2664277
Harsh, V., Jyothi, S.A., Godfrey, P.B.: Spineless data centers. In: HotNets 2020, New York, NY, USA, pp. 67–73. Association for Computing Machinery (2020). https://doi.org/10.1145/3422604.3425945
Hodo, E., Grebeniuk, S., Ruotsalainen, H., Tavolato, P.: Anomaly detection for simulated IEC-60870-5-104 trafiic. In: Proceedings of the 12th International Conference on Availability, Reliability and Security, ARES 2017, New York, NY, USA. Association for Computing Machinery (2017). https://doi.org/10.1145/3098954.3103166
Hoffman, A.J.: On the line graph of the complete bipartite graph. Ann. Math. Stat. 35(2), 883–885 (1964). https://doi.org/10.1214/aoms/1177703593
Hoyos, J., Dehus, M., Brown, T.X.: Exploiting the goose protocol: a practical attack on cyber-infrastructure. In: 2012 IEEE Globecom Workshops, pp. 1508–1513 (2012). https://doi.org/10.1109/GLOCOMW.2012.6477809
Jung, S.S., Formby, D., Day, C., Beyah, R.: A first look at machine-to-machine power grid network traffic. In: 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), pp. 884–889 (2014). https://doi.org/10.1109/SmartGridComm.2014.7007760
Lin, C.-Y., Nadjm-Tehrani, S.: A comparative analysis of emulated and real IEC-104 spontaneous traffic in power system networks. In: Abie, H., et al. (eds.) CPS4CIP 2020. LNCS, vol. 12618, pp. 207–223. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-69781-5_14
Lin, C.Y., Nadjm-Tehrani, S., Asplund, M.: Timing-based anomaly detection in SCADA networks. In: D’Agostino, G., Scala, A. (eds.) Critical Information Infrastructures Security. LNCS, vol. 10707, pp. 48–59. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-99843-5_5
Mai, K., Qin, X., Ortiz, N., Molina, J., Cardenas, A.A.: Uncharted networks: a first measurement study of the bulk power system. In: Proceedings of the ACM Internet Measurement Conference, Virtual Event USA, pp. 201–213. ACM, October 2020. https://doi.org/10.1145/3419394.3423630
Maynard, P., McLaughlin, K., Haberler, B.: Towards understanding man-in-the-middle attacks on IEC 60870-5-104 SCADA networks. In: 2nd International Symposium for ICS & SCADA Cyber Security Research 2014. BCS Learning & Development, September 2014. https://doi.org/10.14236/ewic/ics-csr2014.5. https://ewic.bcs.org/content/ConWebDoc/53228
Mehner, S., Schuster, F., Hohlfeld, O.: Lights on power plant control networks. In: Hohlfeld, O., Moura, G., Pelsser, C. (eds.) PAM 2022. LNCS, vol. 13210, pp. 470–484. Springer, Cham (2022). https://doi.org/10.1007/978-3-030-98785-5_21
Qin, X., Rosso, M., Cardenas, A.A., Etalle, S., den Hartog, J., Zambon, E.: You can’t protect what you don’t understand: characterizing an operational gas SCADA network. In: 2022 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, pp. 243–250. IEEE, May 2022. https://doi.org/10.1109/SPW54247.2022.9833864. https://ieeexplore.ieee.org/document/9833864/
Roig, P.J., Alcaraz, S., Gilly, K., Juiz, C.: Modelling a leaf and spine topology for VM migration in fog computing. In: 2020 24th International Conference Electronics, pp. 1–6 (2020). https://doi.org/10.1109/IEEECONF49502.2020.9141611
Wressnegger, C., Kellner, A., Rieck, K.: ZOE: content-based anomaly detection for industrial control systems. In: 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), pp. 127–138 (2018). https://doi.org/10.1109/DSN.2018.00025
Yang, Y., McLaughlin, K., Littler, T., Sezer, S., Pranggono, B., Wang, H.F.: Intrusion detection system for IEC 60870–5-104 based SCADA networks. In: 2013 IEEE Power Energy Society General Meeting, pp. 1–5 (2013). https://doi.org/10.1109/PESMG.2013.6672100
Acknowledgements
This work was supported in part by NSF CNS-1929410, CNS-1931573 and by the INTERSECT project, Grant No. NWA.1162.18.301, funded by the Dutch Research Council (NWO). Any opinions, findings, conclusions, or recommendations expressed in this work are those of the author(s) and do not necessarily reflect the views of the funding organizations.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A IEC 60870-5-104
IEC 104 is an application layer protocol standardized by IEC 60870-5-104 [1]. Designed for the monitoring and control of industrial systems, it finds widespread application in sectors such as power grids and gas systems. Operating over TCP/IP, it employs a client/server model for communication.
There are distinct features of the IEC104 protocol:
(1) Message Types: Supports both synchronous and asynchronous messages, often referred to as spontaneous or periodic messages. (2) Balance and Unbalance Communications: In balanced communication, either the controller device or the agent device can initiate the interaction. In contrast, unbalanced communication allows only the controller device to initiate, with the agent responding. (3) Message Attributes: IEC104 messages can carry timestamps and quality attributes, enhancing the information’s reliability and context. (4) Synchronous and Asynchronous Modes: In the synchronous mode, the agent sends a new message after a fixed period. However, in the asynchronous mode, the agent sends a message whenever a variable’s value strays from a predefined deadband.
Inside these TCP packets of IEC 104, there is one or more Application Protocol Data Units (APDUs). Each APDU is composed of: (1) Application Protocol Control Information (APCI): This acts as the header of the message and is essential for the proper transmission and receipt of the message. (2) Application Service Data Unit (ASDU): This is the main content of the message and carries sensor and control data that is shared between the field agent and the controller.
APDUs are categorized into three types:
-
I-Format APDUs: These are the primary carriers of sensor and control data. An ASDU within this format includes a Data Unit Identifier and Information Objects. Each Information Object is a representation of a specific device in the field, and each one is linked to a unique address called the Information Object Address (IOA). Apart from this, the ASDU holds the Type Identification, which denotes the specific data format or command type, and the Cause Of Transmission (COT) that outlines the reason behind the message’s dispatch.
-
S-Format APDUs: These are simpler and serve as acknowledgments. They are dispatched after a specified number of I-Format APDUs are successfully received by the other end.
-
U-Format APDUs: These have a special role in managing the overall connection. They can command the beginning or cessation of I-Format APDUs and also transmit keep-alive requests to ensure the connection’s stability. When a new connection is initiated, it is in the “STOPDT” State by default.
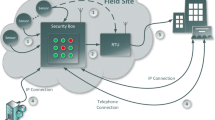
IEC 104 was designed with reliability in mind. Typically, a primary connection is established between a controller and an RTU. Alongside this, there is a secondary or backup connection with another controller server. While the primary connection handles the main data transfer and acknowledgments (I-Format and S-Format messages) and occasionally U-Frame, the secondary focuses on periodic keep-alive checks (U TESTFR messages) to test the status of the connection. If the backup server ever sends a communication initiation command, roles are swapped, with the backup server taking the primary role and vice-versa [18].
B Modbus/TCP
Modbus is a widely used industrial protocol that is easy to implement, maintain and has open specifications [2]. It has several versions, such as Modbus RTU for serial communication and Modbus/TCP for TCP/IP communication. This paper focuses on Modbus/TCP, which is a client/server architecture with a simple request/response protocol. The controller (client) is the only one that can initiate communication with the agent (server). The agent never sends a message unless requested by the controller. Modbus has four data types: input register, holding registers, discrete inputs, and coils. The two “register” types are 16-bit elements commonly used for measurement values, while discrete inputs and coils are one-bit elements used for status values. The message structure of Modbus consists of three parts: a header called Modbus Application Protocol (MBAP), a Function Code that identifies different operations, and a Payload (Data) that carries the content of the message. The format and size of the payload depend on the function code.
The MBAP includes the following components:
-
Transaction Identifier: A numerical identifier to match request and response messages.
-
Protocol Identifier: This is set to zero for Modbus/TCP.
-
Length: The number of bytes in the frame.
-
Unit ID: This is used in serial communication as the address of the device when multiple agents are connected to a single controller. It is set to zero for Modbus/TCP. This includes the Unit ID, Function Code, and Data.
In contrast to IEC 104, Modbus does not include timestamp or quality attributes in its packets. For instance, IEC 104 utilizes the attribute CP56Time2a as a timestamp in the ASDU process with a long time tag, such as “M_ME_TF_1” (No. 36), to register the time when the measurement was taken; thus, there is no assurance that the information object sent is current or that the data is accurate. Furthermore, Modbus does not have a standard method for data object description. For example, to determine if a register value represents a voltage value between 0 and 220 V.
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Ortiz, N., Rosso, M., Zambon, E., den Hartog, J., Cardenas, A.A. (2024). From Power to Water: Dissecting SCADA Networks Across Different Critical Infrastructures. In: Richter, P., Bajpai, V., Carisimo, E. (eds) Passive and Active Measurement. PAM 2024. Lecture Notes in Computer Science, vol 14537. Springer, Cham. https://doi.org/10.1007/978-3-031-56249-5_1
Download citation
DOI: https://doi.org/10.1007/978-3-031-56249-5_1
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-56248-8
Online ISBN: 978-3-031-56249-5
eBook Packages: Computer ScienceComputer Science (R0)