Abstract
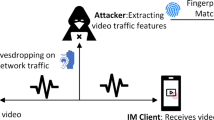
The video platforms that users watch leak the privacy of their preferences. More and more video streaming is being encrypted to protect users’ privacy. In addition, many users use VPN to enhance their privacy protection further. VPN makes video platform identification challenging because it poses traffic obfuscation and further data encryption. Although the segment-based transmission mechanism and Variable Bit-Rate encoding in HAS make network video traffic show still identifiable patterns, most existing work cannot distinguish different platforms due to the similarity of video streaming. Therefore, we propose a traffic-based side-channel attack method to identify VPN video streaming platforms in real time. The aggregated feature sequence of the unidirectional video streaming is extracted to significantly retain the characteristics of different video platforms. Experiments on 10Gbps backbone background traffic show that the F1-score of the method exceeds 97% and can be processed in real time. In addition, we verify the method’s robustness on datasets with different path features and encryption techniques. A comparison with similar methods shows that our method only requires 1/1260 of the storage and 1/60 of the processing time to identify accurately.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Afuwape, A.A., Xu, Y., Anajemba, J.H., Srivastava, G.: Performance evaluation of secured network traffic classification using a machine learning approach. Comput. Stand. Interfaces 78, 103545 (2021)
Akhshabi, S., Anantakrishnan, L., Begen, A.C., Dovrolis, C.: What happens when http adaptive streaming players compete for bandwidth? In: Proceedings of the 22nd International Workshop on Network and Operating System Support for Digital Audio and Video, pp. 9–14 (2012)
Barradas, D., Santos, N., Rodrigues, L.: Effective detection of multimedia protocol tunneling using machine learning. In: 27th \(\{\)USENIX\(\}\) Security Symposium (\(\{\)USENIX\(\}\) Security 18), pp. 169–185 (2018)
Chen, S., Wang, R., Wang, X., Zhang, K.: Side-channel leaks in web applications: a reality today, a challenge tomorrow. In: 2010 IEEE Symposium on Security and Privacy, pp. 191–206. IEEE (2010)
Cho, K.: Km, and kato, a. traffic data repository at the wide project. USENIX ATC, Freenix track (2000)
Cisco.: Cisco visual networking index: Forecast and trends, 20172022 white paper. https://davidellis.ca/wp-content/uploads/2019/05/cisco-vni-feb2019.pdf
Dias, K.L., Pongelupe, M.A., Caminhas, W.M., de Errico, L.: An innovative approach for real-time network traffic classification. Comput. Netw. 158, 143–157 (2019)
Draper-Gil, G., Lashkari, A.H., Mamun, M.S.I., Ghorbani, A.A.: Characterization of encrypted and VPN traffic using time-related. In: Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP), pp. 407–414 (2016)
Esteban, J., Benno, S.A., Beck, A., Guo, Y., Hilt, V., Rimac, I.: Interactions between http adaptive streaming and TCP. In: Proceedings of the 22nd International Workshop on Network and Operating System Support for Digital Audio and Video, pp. 21–26 (2012)
Izadi, S., Ahmadi, M., Rajabzadeh, A.: Network traffic classification using deep learning networks and Bayesian data fusion. J. Netw. Syst. Manage. 30(2), 25 (2022)
Khan, M.U., Bukhari, S.M., Maqsood, T., Fayyaz, M.A., Dancey, D., Nawaz, R.: SCNN-attack: a side-channel attack to identify youtube videos in a VPN and non-VPN network traffic. Electronics 11(3), 350 (2022)
Mangla, T., Halepovic, E., Ammar, M., Zegura, E.: Using session modeling to estimate HTTP-based video QoE metrics from encrypted network traffic. IEEE Trans. Netw. Serv. Manage. 16(3), 1086–1099 (2019)
Pacheco, F., Exposito, E., Gineste, M.: A framework to classify heterogeneous internet traffic with machine learning and deep learning techniques for satellite communications. Comput. Netw. 173, 107213 (2020)
Shapira, T., Shavitt, Y.: FlowPic: a generic representation for encrypted traffic classification and applications identification. IEEE Trans. Netw. Serv. Manage. 18(2), 1218–1232 (2021)
Shi, Y., Ross, A., Biswas, S.: Source identification of encrypted video traffic in the presence of heterogeneous network traffic. Comput. Commun. 129, 101–110 (2018)
Stanton, R.: Securing VPNs: comparing SSL and IPSEC. Comput. Fraud Secur. 2005(9), 17–19 (2005)
Tang, J., et al.: Caps-LSTM: a novel hierarchical encrypted VPN network traffic identification using CapsNet and LSTM. In: Lu, W., Sun, K., Yung, M., Liu, F. (eds.) SciSec 2021. LNCS, vol. 13005, pp. 139–153. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-89137-4_10
Tang, P., Dong, Y., Mao, S.: Online traffic classification using granules. In: IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), pp. 1135–1140. IEEE (2020)
Acknowledgements
This work was supported by the National Key R &D Program of China (2021YFB3101403).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 IFIP International Federation for Information Processing
About this paper
Cite this paper
Lu, A., Wu, H., Luo, H., Cheng, G., Hu, X. (2024). Real-Time Platform Identification of VPN Video Streaming Based on Side-Channel Attack. In: Meyer, N., Grocholewska-Czuryło, A. (eds) ICT Systems Security and Privacy Protection. SEC 2023. IFIP Advances in Information and Communication Technology, vol 679. Springer, Cham. https://doi.org/10.1007/978-3-031-56326-3_24
Download citation
DOI: https://doi.org/10.1007/978-3-031-56326-3_24
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-56325-6
Online ISBN: 978-3-031-56326-3
eBook Packages: Computer ScienceComputer Science (R0)