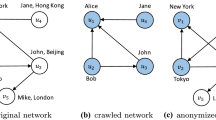
Abstract
Social networks not only help expand interpersonal interactions, enable data analysis, and implement intelligent recommendations, but also can deeply examine social structures and dynamic changes between individuals, making them an indispensable part of contemporary society. However, malicious entities pose a significant threat to user identity and relationship information within social networks, raising concerns about privacy and security issues. Although existing k-anonymity schemes provide certain privacy protection, they lack the flexibility to adjust the intensity of privacy protection according to specific scenarios and user preferences, thus seriously compromising the utility of anonymized data. Based on the isomorphic algorithm, this paper proposes a new structural anonymity algorithm called α-partial isomorphic anonymity (α-PIA) to meet the privacy protection and data usage requirements in different scenarios of social networks. By capturing graph structure features at different levels to calculate the similarity between nodes, α-PIA can improve clustering quality. Extensive experiments are carried out based on two public datasets. Experimental results show that compared with similar schemes, α-PIA achieves better results in terms of information loss, average clustering coefficient and average shortest path length and better balances the privacy protection and practicality of graph data.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Siddula, M., Li, Y., Cheng, X., Tian, Z., Cai, Z.: Anonymization in online social networks based on enhanced Equi-cardinal clustering. IEEE Trans. C. Soc. Syst. 6(4), 809–820 (2019)
Zhang, S., Hu, B., Liang, W., Li, K.-C., Gupta, B.B.: A caching-based dual K-anonymous location privacy-preserving scheme for edge computing. IEEE Internet Things J. 10(11), 9768–9781 (2023)
Mauw, S., Ramírez-Cruz, Y., Trujillo-Rasua, R.: Preventing active re-identification attacks on social graphs via sybil subgraph obfuscation. Knowl. Inf. Syst. 64(4), 1077–1100 (2022)
Zhao, Y., Chen, J.: A survey on differential privacy for unstructured data content. ACM Comput. Surv. 54(10s), 1–28 (2022)
Jiang, H., Pei, J., Yu, D., Yu, J., Gong, B., Cheng, X.: Applications of differential privacy in social network analysis: a survey. IEEE Trans. Knowl. Data Eng. 35(1), 108–127 (2023)
Hou, L., Ni, W., Zhang, S., Fu, N., Zhang, D.: PPDU: dynamic graph publication with local differential privacy. Knowl. Inf. Syst. 65(7), 2965–2989 (2023)
Ding, X., Wang, C., Choo, K.K.R., Jin, H.: A novel privacy preserving framework for large scale graph data publishing. IEEE Trans. Knowl. Data Eng. 33(2), 331–343 (2019)
Zhang, E., Li, H., Huang, Y., Hong, S., Zhao, L., Ji, C.: Practical multi-party private collaborative k-means clustering. Neuro Comput. 467, 256–265 (2022)
Sowmyarani, C.N., Namya, L.G., Nidhi, G.K., Kumar, P.R.: Enhanced k-Anonymity model based on clustering to overcome Temporal attack in Privacy Preserving Data Publishing. In: IEEE Int. Conference on Electronics, Computing and Communication Technologies (CONECCT), pp. 1–6. IEEE, Bangalore, India (2022)
Kacha, L., Zitouni, A., Djoudi, M.: KAB: a new k-anonymity approach based on black hole algorithm. J. King Saud Univ. Comput. Inf. Sci. 34(7), 4075–4088 (2022)
Xiang, N., Ma, X.: TKDA: An Improved Method for K-degree Anonymity in Social Graphs. In: IEEE Symposium on Computers and Communications (ISCC), pp. 1–6. IEEE, Rhodes, Greece (2022)
Lu, X., Song, Y., Bressan, S.: Fast identity anonymization on graphs. In: 23rd International Conference on Database and Expert Systems Applications (DEXA), pp. 281–295. Springer, Vienna, Austria (2012)
Casas-Roma, J., Herrera-Joancomartí, J., Torra, V.: K-Degree anonymity and edge selection: improving data utility in large networks. Knowl. Inf. Syst. 50(2), 447–474 (2017)
Kiabod, M., Dehkordi, M.N., Barekatain, B.: TSRAM: A time-saving k-degree anonymization method in social network. Expert Syst. Appl. 125, 378–396 (2019)
Kiabod, M., Dehkordi, M.N., Barekatain, B.: A fast graph modification method for social network anonymization. Expert Syst. Appl. 180, 115148 (2021)
Tripathy, B.K., Panda, G.K.: A New Approach to Manage Security against Neighborhood Attacks in Social Networks. In: 2010 International Conference on Advances in Social Networks Analysis and Mining, pp. 264–269. IEEE, Odense, Denmark (2010)
Zou, L., Chen, L., Ozsu, M.T.: K-Automorphism: a general framework for privacy preserving network publication. Proc. VLDB Endowment 2(1), 946–957 (2009)
Cheng, J., Fu A.W., Liu, J.: K-isomorphism: privacy preserving network publication against structural attacks. In: 2010 ACM SIGMOD International Conference Management of data on Management of data, pp. 459–470. ACM, Indianapolis Indiana, America (2010)
Zhang, H., Lin, L., Xu, L., Wang, X.: Graph partition based privacy-preserving scheme in social networks. J. Netw. Comput. Appl. 195, 103214 (2021)
Adam, Ó.Conghaile.: Cohomology in constraint satisfaction and structure isomorphism. In: 47th International Symposium on Mathematical Foundations of Computer Science, p. 75:1–75:16. Leibniz-Zentrum für Informatik, Vienna, Austria (2022)
Stanford large network dataset collection. https://snap.stanford.edu/data/
Network Repository Homepage. https://networkrepository.com
Rossi, R.A., Ahmed, N.K.: The network data repository with interactive graph analytics and visualization. In: 29th AAAI Conference on Artificial Intelligence, pp. 4292–4293 (2015)
Acknowledgments
This work was financially supported by the Natural Science Foundation of China (Nos. U22A2099, 61966009, 62172350), the Guangdong Basic and Applied Basic Research Foundation (No. 2023A1515012846), the Innovation Project of Guangxi Graduate Education (No. YCSW2023326), and the Innovation Project of GUET Graduate Education (No. 2023YCXS057).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 IFIP International Federation for Information Processing
About this paper
Cite this paper
Zhang, M., Hao, Y., Lu, P., Chang, L., Li, L. (2024). Flexible k-anonymity Scheme Suitable for Different Scenarios in Social Networks. In: Shi, Z., Torresen, J., Yang, S. (eds) Intelligent Information Processing XII. IIP 2024. IFIP Advances in Information and Communication Technology, vol 703. Springer, Cham. https://doi.org/10.1007/978-3-031-57808-3_26
Download citation
DOI: https://doi.org/10.1007/978-3-031-57808-3_26
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-57807-6
Online ISBN: 978-3-031-57808-3
eBook Packages: Computer ScienceComputer Science (R0)