Abstract
Blind signatures allow the issuing of signatures on messages chosen by the user so that they ensure blindness of the message against the signer. Moreover, a malicious user cannot output \(\ell +1\) signatures while only finishing \(\ell \) signing sessions. This notion, called one-more unforgeability, comes in two flavors supporting either sequential or concurrent sessions. In this paper, we investigate the security of a class of blind signatures constructed from Sigma-protocols with small challenge space \(\mathcal {C}_{\varSigma }\) (i.e., polynomial in the security parameter), using k repetitions of the protocol to decrease the chances of a cheating prover. This class of schemes includes, among others, the Schnorr blind signature scheme with bit challenges and the recently proposed isogeny-based scheme CSI-Otter (Crypto’23).
For this class of blind signatures, we show a polynomial-time attack that breaks one-more unforgeability for any \(\ell \ge k\) concurrent sessions in time \(O(k \cdot |\mathcal {C}_{\varSigma }|)\). Contrary to the ROS attack, ours is generic and does not require any particular algebraic structure. We also propose a computational trade-off, where, for any \(t \le k\), our attack works for \(\ell = \frac{k}{t}\) in time \(O(\frac{k}{t} \cdot |\mathcal {C}_{\varSigma }|^t)\). The consequences of our attack are as follows. Schemes in the investigated class of blind signatures should not be used concurrently without applying specific transformations to boost the security to support more signing sessions. Moreover, for the parameters proposed for CSI-Otter (\(k=128\) and \(|\mathcal {C}_{\varSigma }|=2\)), the scheme becomes forgeable after 128 concurrent signing sessions for the basic attack and with only eight sessions in our optimized attack. We also show that for those parameters, it is even possible to compute two signatures in around 10 min with just one signing session using the computation power of the Bitcoin network. Thus, we show that, for sequential security, the parameter k must be at least doubled in the security parameter for any of the investigated schemes.
You have full access to this open access chapter, Download conference paper PDF
Keywords
1 Introduction
Blind signatures allow a signer to sign messages picked by third parties without actually seeing them. This property, called blindness, enables many privacy-preserving applications of blind signatures. The authenticity of the signer’s signatures is based on a one-more unforgeability property, which informally states that one cannot create \(\ell +1\) valid signatures under different messages while only finishing the signing process \(\ell \) times with the signer. If one-more unforgeability holds even if those \(\ell \) signing queries are executed in parallel, we are talking about a concurrently secure blind signature scheme. Alternatively, we are talking about sequential unforgeable blind signatures, if the signer processes queries sequentially. Secure blind signatures can be constructed from different assumptions such as RSA [3, 10], discrete logarithm [1, 17, 21, 29], pairings [7], lattices [20, 26], and isogenies [22]. The resulting schemes provide various properties, including optimal round-complexity (i.e., two-move) and security under stronger security notions.
One of the most prominent ways to construct blind signatures is to leverage the existing construction of standard digital signatures from the Sigma protocol (\(\varSigma \)-protocol) and the Fiat-Shamir transformation. \(\varSigma \)-protocols are three-move interactive protocols, where the prover creates a commitment and later answers a challenge from the verifier. If the challenge space is small (e.g., bit challenges), the prover and verifier repeat the protocol k-times in parallel to decrease the chances of a cheating prover. For \(\varSigma \)-protocols, one can use the Fiat-Shamir transformation to turn this protocol into a signature scheme, i.e., compute the verifier’s challenge using a random oracle query on the prover’s commitment and a message picked by the prover/signer. The transformation can also be applied to \(\varSigma \)-protocols with a small challenge space where all k commitments are queried at once to the random oracle, and the prover’s responses are provided separately for each of the k protocol instances.
While this transformation works for standard signatures, it fails for blind signatures since the signer can break blindness by inspecting the commitment and the challenge value of the final signature. The signer can do it even if the user is the one querying the random oracle. A folklore approach to get around this problem is introducing a way to randomize the signer’s commitment and output of the random oracle that the user can reverse to receive the final signature. Prominent examples using this approach are the Schnorr blind signature scheme, the Abe-Okamoto scheme in the discrete logarithm setting, and the recently proposed CSI-Otter scheme [22] based on isogenies.
Unfortunately, the Schnorr blind signature scheme and many others following the above recipe are vulnerable to the so-called ROS attack [4]. These schemes cannot be concurrently unforgeable for \(\ell \) bigger than polylogarithmic in the security parameter. In practice, the scheme becomes unusable after approximately 8–10 concurrent signing queries, and the only way out is to either use transformations boosting the security to more signatures [9, 24] or use the scheme sequentially, which limits the number of real-world applications significantly. The attack requires that there exists an algebraic structure in the space of commitments that the attacker can leverage. Such a structure does not exist, e.g., for the CSI-Otter scheme, making it potentially secure against the ROS attack and allowing for polynomially many signing queries, an open problem left by the authors [22].
1.1 Our Contribution
This paper investigates the security of three-move blind signatures built generically from (parallel repetitions of) \(\varSigma \)-protocols with a small challenge space \(\mathcal {C}_{\varSigma }\) (non-negligible soundness error \(1/|\mathcal {C}_{\varSigma }|\)). For such blind signature schemes, we show a new polynomial-time attack breaking the unforgeability for \(\ell = k\), where k is the number of repetitions of the base protocol. Contrary to the ROS attack, we do not require any particular algebraic structure and rely solely on the honest verifier zero-knowledge property of the \(\varSigma \)-protocol and queries to the random oracle (i.e., computing hash digests).
The Attack. Katsumata et al. introduced in [22] a novel blind signature scheme based on isogenies called CSI-Otter. Their construction can be interpreted as a blinded variant of CSI-FiSh [6], itself based on a \(\varSigma \)-protocol with small challenge space (bit clallenge). However, the demonstrated scheme offers only provable security for a poly-logarithmic number of concurrent executions. The authors then conjectured its security for polynomially many executions based on its apparent immunity to the ROS attack, stemming from the non-algebraic structure of the protocol. We contend that this argument lacks rigor, as the ROS attack does not encompass all potential threats to the concurrent security of blind signatures in general. Thus, motivated by this observation, we elaborate a concrete attack targeting the concurrent security of this specific class of blind signatures, while being divergent from the ROS attack methodology. We use the fact that, from the user’s point of view, the signer is running k instances of the \(\varSigma \)-protocol with challenges from \(\mathcal {C}_{\varSigma }\). In the case of a honest user, there is no problem since we assume that the user will “glue" all k instances in the same random oracle query. However, a malicious user does not need to do it. Assume that \(\textbf{R} = (R_{1},\ldots , R_{k})\) is the commitment sent in the first step by the signer and \(\textbf{R}' = (R_{1}',\ldots , R_{k}')\) is the blinded commitment. A honest user can compute the challenge by computing \(\textbf{c}' = (c'_1, \ldots , c'_k) = \mathcal {H}(\textbf{R}' \Vert m)\) and then challenges the signer with a blinded version of it. Given the signer’s response, the honest user owns a signature under m.
A malicious user can generate a valid signature differently. Thanks to the honest verifier zero-knowledge property of the \(\varSigma \)-protocol, the adversary can simulate one of the k instances of the protocol. As a result of the simulation, it will receive a valid transcript \((e^*,d^*,z^*)\), where \(d^* \in \mathcal {C}_{\varSigma }\). The adversary can now compute the challenge \(\textbf{c}' = (c'_1, \ldots , c'_k)= \mathcal {H}( (R_1',\ldots , R_{k-1}',e^*)\Vert m^*)\) for a random message \(m^*\) and repeat the process for a different message until \(c'_k = d^*\). On average, a malicious user will only have to repeat this computation \(|\mathcal {C}_{\varSigma }|\) times, e.g. two times for bit challenges.
The key observation, now, is that the adversary only needs the \(k-1\) first elements of the signer’s response to receive a valid signature. It works since the adversary simulated the last instance and knows a proper answer \(z^*\) for the challenge \(\textbf{c}'\) it picked. This means that for the protocol instance with commitment \(R_k\), the adversary can arbitrarily choose a challenge and still be able to receive a valid signature. In itself, this is not interesting. However, suppose the adversary executes the same attack over k concurrent sessions. In that case, the malicious user ends up with k instances of the \(\varSigma \)-protocol for which it can arbitrarily pick the challenge while simultaneously still being able to compute k valid signatures. Thus, the adversary can use those instances to create a one-more signature.
To be more explicit, we provide an unblind version of the attack. Suppose \(\textbf{R}_1, \ldots , \textbf{R}_k\) are the commitment the signer creates for the k concurrent sessions the adversary executes, where \(\textbf{R}_i = (R_{i,1},\ldots ,R_{i,k})\). The adversary uses the above technique to simulate k instances of the \(\varSigma \)-protocol receiving \((e_i,d_i,z_i)\). It then finds messages \(m_1,\ldots ,m_k\) such that for every \(i \in \{1,\ldots ,k\}\) we have
The adversary now picks a random message \(m^*\) and computes the challenge \(\textbf{c}^* = \mathcal {H}((R_{1,k},\ldots ,R_{k,k}) \Vert m^*) \in \mathcal {C}_{\varSigma }^k\), where \(\textbf{c}^* = (c_1^*, \ldots , c_k^*)\). Now, for the ith session, it challenges the signer with \((c_{i,1},\ldots ,c_{i,k-1},c_i^*)\) and receives k separate responses for each of the elements of the challenge. It is easy to see now that by replacing the last entries of the response with the \(z_i\) values, the adversary will receive valid signatures for messages \(m_1,\ldots ,m_k\). By combining those last entries, the adversary can construct a valid signature for challenge \(\textbf{c}^*\), which means a valid forgery for message \(m^*\).
In expectation, the adversary will have to compute the hash function \(k \cdot |\mathcal {C}_{\varSigma }|\) times and execute k concurrent sessions for the attack to be successful. It can also be performed with fewer sessions at the expense of computation, i.e. \(\frac{k}{t}\) concurrent sessions with adversary’s running time \(O(\frac{k}{t} \cdot |\mathcal {C}_{\varSigma }|^t)\). In case we want to run the attack in the sequential settings, the running time will be \(O(2 \cdot |\mathcal {C}_{\varSigma }|^{k/2})\), i.e., exponential in k but breaking unforgeability by creating two signatures while only querying one signature. In the above attack, the adversary requires the signer to create k (respectively \(\frac{k}{t}\)) signatures, where all must be made using concurrent sessions. We fix this shortcoming by extending the attack so that the adversary only needs two open sessions at a given time. However, the attack still requires the signer to create k (respectively \(\frac{k}{t}\)) signatures.
Implications. Our results show that for practical and concurrent applications, one should not use blind signatures constructed from \(\varSigma \)-protocols with a small challenge space. We summarize those protocols in Table 1. Since the attack is generic and requires no unique algebraic structure, it works in various settings: Schnorr blind signature with bit challenges in the discrete logarithm setting, the Fiat-Shamir blind signatures (as in [19]) in the RSA setting, CSI-Otter [22] in the isogenies setting. For example, CSI-Otter [22] only guarantees security for polylogarithmic signatures. We demonstrate a specific attack that compromises security after only 128 signatures. This implies that the signer would need to replace its secret keys after fewer than 128 signed signatures, rendering the scheme impractical. Interestingly, the attack also works in the weaker synchronized parallel attack model from [28], where we assume that the steps of the protocol for each session are executed in order of opened sessions, i.e., in our case, this means that the challenge for the first session must be sent before the challenge for the second session, etc.
While increasing the challenge space and consequently the number of instances k makes our attack more time-consuming, an efficient way to forge a signature will always exist if the signer uses the signing keys more than k times. In practice, to use such blind signatures concurrently, one must use boosting transformations similar to the case of Schnorr blind signatures and the ROS attack. Unfortunately, this leads to a significant increase in the communication complexity and signature size.
One of the main downsides of our results is that the attack targets all known \(\varSigma \)-protocols for the graph isomorphism problem. This significantly influences the area of post-quantum blind signatures, where we are still trying to find more efficient alternatives for schemes based on standard lattice-based problems. Potential blind signatures from the lattice isomorphism problem [14] and the CSI-Otter scheme are vulnerable to our attack, leaving us only with relatively inefficient blind signatures from standard lattice assumptions that suffer from big signature sizes.
Case Study. We introduce our attack, targetting any blind signature scheme built from a \(\varSigma \)-protocol with small challenge space. To make the attack more explicit, we show how to apply it against the CSI-Otter isogeny-based blind signature scheme recently introduced at Crypto’23. With this, we solve an open problem left by the authors [22]. In particular, we show that CSI-Otter is not concurrently secure in the polynomial regime, i.e., it does not support polynomially many concurrent sessions as conjectured by the authors.
We show that for the parameters proposed by the authors (i.e., \(n = 128\)), CSI-Otter becomes forgeable after issuing only 128 signatures. Sacrificing a bit of computation, we can make the scheme insecure even with only eight concurrent sessions. In such a case, the adversary must perform around half a megahash, which can be done in less than a second on commodity hardware (e.g., the rate of the M1 Pro processor is 5Mh/s). Moreover, we argue that CSI-Otter is not even sequentially secure for the proposed parameters. In such a case, our attack requires around \(2 \cdot 2^{64}\) hash computations, which is in the realms of the bitcoin difficulty, i.e., can be computed by the bitcoin network in around 10 min. Thus, the challenge space needs to be increased for CSI-Otter to be practically secure in the sequential setting. In particular, for n-bit security, we need at least \(k = 2 \cdot n\). Interestingly, one can use the argument in [19] as long as the number of repetitions is at least doubled with the security parameter. Hence, we show that their choice of parameters is tight with our concrete attack.
Summary of Contribution. This paper analyzes the security of a specific class of blind signature schemes, i.e., schemes constructed by applying a particular transformation to a \(\varSigma \)-protocol with a challenge space that is polynomial in the size of the security parameter. This class captures many existing schemes, including blind Schnorr signatures with bit challenges, the Fiat-Shamir factoring-based scheme (as in [19]), and the recently proposed CSI-Otter isogeny-based scheme [22].
-
We show that this class of blind signatures is vulnerable to a polynomial-time attack that breaks the one-more unforgeability for any \(\ell > k\) of concurrent sessions, where the challenge space is \(\mathcal {C}_{\varSigma }^{k}\), e.g., \(|\mathcal {C}_{\varSigma }| = 2\) and \(k=128\) for CSI-Otter [22]. The attack is generic and does not require any particular algebraic structure. It can be improved so that, at a given time, the adversary only needs to keep two sessions open concurrently while still requiring k signatures to create a forged one.
-
We then show that there exists a tradeoff between the number of sessions/signatures needed and the adversary’s running time. The implications are that CSI-Otter is forgeable for the above parameters with only eight concurrent sessions in under a second on commodity hardware.
-
We show that even if such schemes are only used in the impractical sequential setting, their parameters must be considered carefully. In particular, the challenge space must be at least doubled in the security parameter \(k \ge 2 \cdot n\). Otherwise, for the parameters proposed in [22], the required computation needed by an adversary is comparable to the work required by Bitcoin miners (\(2^{66}\) hash operations in expectation), where the network of miners can solve such a problem in around ten minutes.
2 Background
2.1 Notation
For a set X, |X| denotes the cardinality of X. For convenience, vectors will be denoted by a bold letter \(\textbf{v} = (v_1,\dots , v_k)\). We will denote the security parameter with n, and for positive integers k we define \([k] := \{1, \ldots , k\}\). We will use \(\Vert \) to denote the concatenation of strings. We use uppercase letters \(\mathcal {A}\) or \(\textsf{A}\) to denote algorithms. We let \(y \leftarrow \mathcal {A}(x)\) denote the output of \(\mathcal {A}\) on input x and
 for the randomized algorithm. For a set X the notation
for the randomized algorithm. For a set X the notation
 means that x is uniformly sampled from X. We use \(\textsf{st}\) explicitly to denote the inner state of an algorithm while omitting it when the context is clear. We say that a function is negligible and denote it as \(\textsf{negl}\!\!\left( n\right) \) if it vanishes faster than the inverse of any polynomial. For a prime number p, we denote the finite field with p elements as \(\mathbb {F}_p.\) Given an hash function \(\mathcal {H}: \{0, 1\}^*\rightarrow \{0, 1\}^k\) and a vector \(\textbf{R} = (R_1, \dots , R_n)\) we define \(\mathcal {H}(\textbf{R}) := \mathcal {H}(R_1\Vert \dots \Vert R_n)\), where the components of the vector are encoded as bit strings.
means that x is uniformly sampled from X. We use \(\textsf{st}\) explicitly to denote the inner state of an algorithm while omitting it when the context is clear. We say that a function is negligible and denote it as \(\textsf{negl}\!\!\left( n\right) \) if it vanishes faster than the inverse of any polynomial. For a prime number p, we denote the finite field with p elements as \(\mathbb {F}_p.\) Given an hash function \(\mathcal {H}: \{0, 1\}^*\rightarrow \{0, 1\}^k\) and a vector \(\textbf{R} = (R_1, \dots , R_n)\) we define \(\mathcal {H}(\textbf{R}) := \mathcal {H}(R_1\Vert \dots \Vert R_n)\), where the components of the vector are encoded as bit strings.
2.2 Sigma Protocols
Definition 1
(\(\varSigma \)-Protocol). A sigma protocol (\(\varSigma \)-protocol) is a three-move interactive protocol \(\varSigma = (\mathcal {G}, \mathcal {P}, \mathcal {V}, \mathcal {C})\) that consists of the following p.p.t. algorithm:
-
Key Generation. On input the security parameter \(1^n\), the probabilistic algorithm \(\mathcal {G}\) outputs a public key \(\textsf{pk}\) and a secret key \(\textsf{sk}\).
-
Prover. The prover \(\mathcal {P}= (\textsf{P}_1, \textsf{P}_2)\) consists of two algorithms:
-
1.
 : on input a secret key \(\textsf{sk}\) the probabilistic algorithm \(\textsf{P}_1\) outputs a commitment R and an internal state \(\textsf{st}\).
: on input a secret key \(\textsf{sk}\) the probabilistic algorithm \(\textsf{P}_1\) outputs a commitment R and an internal state \(\textsf{st}\). -
2.
\(s\leftarrow \textsf{P}_2(\textsf{sk}, c, \textsf{st})\): on input a challenge \(c \in \mathcal {C}\), a secret key \(\textsf{sk}\) and a state \(\textsf{st}\), the algorithm \(\textsf{P}_2\) outputs a response s.
-
1.
-
Verifier. On input a public key \(\textsf{pk}\), a commitment R, a challenge c, and a response s, the verification algorithm \(\mathcal {V}\) outputs 1 to indicate the prover is valid, and 0 otherwise.
We say that a \(\varSigma \)-protocol is correct if for every \(1^n\), for every key pair \((\textsf {pk}, \textsf {sk}) \leftarrow \mathcal {G}(1^n)\), and for every transcript (R, c, s) output from the interaction in Fig. 1 between a prover and a verifier, we have \(\mathcal {V}(\textsf {pk}, R, c, s) = 1.\)
Security Notions. We briefly capture the security of a \(\varSigma \)-protocol in the following notions: honest verifier zero-knowledge and special soundness.
-
We say that a \(\varSigma \)-protocol is honest verifier zero-knowledge (HVZK) if there exists a p.p.t. simulator \(\textsf{Sim}\) such that for every key pair \((\textsf {pk}, \textsf {sk}) \leftarrow \mathcal {G}(1^n)\), and for every challenge \(c \in \mathcal {C}\), it outputs a valid transcript \((R, c, s) \leftarrow \textsf{Sim}(\textsf {pk}, c)\) that is indistinguishable from a real transcript.
-
We say that a \(\varSigma \)-protocol is (2-)special sound if there exists a deterministic polynomial time extractor \(\textsf{Ext}\) such that, for every key pair \((\textsf {pk}, \textsf {sk}) \leftarrow \mathcal {G}(1^n)\), recovers the secret \(\textsf{sk}\) given two valid transcripts \((R, c_1, s_1)\) and \((R, c_2, s_2)\) sharing the same commitment and different challenges.
We will assume hereafter that any \(\varSigma \)-protocol we encounter satisfies the properties enunciated in the above security notions. Recall also that we can turn any \(\varSigma \)-protocols into a signature scheme using the Fiat-Shamir Transform [16, 29].
2.3 Blind Signature Schemes
Definition 2
(Three-Moves Blind Signature Scheme). A three-moves blind signature scheme \({{\,\mathrm{\textsf{BS}}\,}}= (\mathcal {G},\mathcal {S}, \mathcal {U}, \mathcal {V})\) consists of the following p.p.t. algorithms:
-
Key Generation. On input the security parameter \(1^n\), the probabilistic algorithm \(\mathcal {G}\) outputs a public key \(\textsf{pk}\) and a secret key \(\textsf{sk}\).
-
Signer. The signer \(\mathcal {S}= (\textsf{S}_1, \textsf{S}_2)\) consists of two algorithms:
-
1.
 : on input a secret key \(\textsf{sk}\), the probabilistic algorithm \(\textsf{S}_1\) outputs an internal state \(\textsf{st}_{\textsf{S}}\) and a commitment R.
: on input a secret key \(\textsf{sk}\), the probabilistic algorithm \(\textsf{S}_1\) outputs an internal state \(\textsf{st}_{\textsf{S}}\) and a commitment R. -
2.
\(s \leftarrow \textsf{S}_2(\textsf{sk}, c, \textsf{st}_{\textsf{S}})\): on input a challenge \(c \in \mathcal {C}\), a secret key \(\textsf{sk}\) and an internal state \(\textsf{st}\), the algorithm \(\textsf{S}_2\) outputs a response s.
-
1.
-
User. The user \(\mathcal {U}= ({{\,\mathrm{\textsf{U}}\,}}_1, {{\,\mathrm{\textsf{U}}\,}}_2)\) consists of two algorithms:
-
1.
 : on input a public key \(\textsf{pk}\), a message m and a signer commitment R, the probabilistic algorithm \({{\,\mathrm{\textsf{U}}\,}}_1\) outputs a challenge \(c \in \mathcal {C}\) and an internal state \(\textsf{st}\).
: on input a public key \(\textsf{pk}\), a message m and a signer commitment R, the probabilistic algorithm \({{\,\mathrm{\textsf{U}}\,}}_1\) outputs a challenge \(c \in \mathcal {C}\) and an internal state \(\textsf{st}\). -
2.
\(\sigma \leftarrow {{\,\mathrm{\textsf{U}}\,}}_2(\textsf{pk}, s, \textsf{st}_{\textsf{U}})\): on input a public key \(\textsf{pk}\), a signer response s and an internal state \(\textsf{st}_{\textsf{U}}\), the probabilistic algorithm \({{\,\mathrm{\textsf{U}}\,}}_2\) outputs a signature \(\sigma \) on a message m.
-
1.
-
Verification. On input a public key \(\textsf{pk}\), a message m, and a signature \(\sigma \), the verification algorithm \(\mathcal {V}\) outputs 1 to indicate the prover is valid, and 0 otherwise.
We say that a three-moves blind signature scheme \({{\,\mathrm{\textsf{BS}}\,}}\) is correct if for every \(1^n\), for every key pair \((\textsf {pk}, \textsf {sk}) \leftarrow \mathcal {G}(1^n)\), for every message and signature pair \((m, \sigma )\) generated from the interaction in Fig. 2 between an user and a signer, we have \(\mathcal {V}(\textsf{pk}, m, \sigma ) = 1.\) We will omit “three-moves" and will say blind signature for brevity.
Security Notions. We capture the security of a Blind Signature Scheme \({{\,\mathrm{\textsf{BS}}\,}}\) by two security notions: blindness and one-more unforgeability. For blindness we will omit its formal definition and refer to [19] since we do not discuss blindness of the schemes and it is out of this paper’s scope.
Definition 3
(One-More-Unforgeability). Let \({{\,\mathrm{\textsf{BS}}\,}}= (\mathcal {G}, \mathcal {U}, \mathcal {S}, \mathcal {V})\) be a blind signature and n be the security parameter. We define the \(\ell \)-one more unforgeability game \({{\,\mathrm{\ell -\textbf{OMUF}_{{{\,\mathrm{\textsf{BS}}\,}}}}\,}}\) with an adversary \(\mathcal {A}\) (in the role of the user) as follows:
-
Setup. Sample a pair of keys
 . Initialize \(\ell _{\texttt{closed}} := 0\) and run \(\mathcal {A}\) on input \(\textsf{pk}\).
. Initialize \(\ell _{\texttt{closed}} := 0\) and run \(\mathcal {A}\) on input \(\textsf{pk}\). -
Online Phase. \(\mathcal {A}\) is given access to oracles \(\textsf{sign}_1\) and \(\textsf{sign}_2\), which behave as follows.
-
Oracle \(\textsf{sign}_1\): the oracle samples a fresh session identifier \(\textsf{sid}\). It sets \(\texttt{open}_{\textsf{sid}}:= \texttt{true}\) and generates
 . Then it returns the response \(R_{\textsf{sid}}\) to \(\mathcal {A}\).
. Then it returns the response \(R_{\textsf{sid}}\) to \(\mathcal {A}\). -
Oracle \(\textsf{sign}_2\): If \(\ell _{\texttt{closed}}<\ell \), the oracle takes as input a challenge c and a session identifier \(\textsf{sid}\). If \(\texttt{open}_{\textsf{sid}} = \texttt{false}\), it returns \(\perp \). Otherwise, it sets \(\ell _{\texttt{closed}} := \ell _{\texttt{closed}} + 1\) and \(\texttt{open}_{\textsf{sid}}:= \texttt{false}\). Then it computes the response
 and returns s to \(\mathcal {A}\).
and returns s to \(\mathcal {A}\).
-
-
Output Determination. When \(\mathcal {A}\) outputs distinct tuples \((m_1, \sigma _1),\dots , (m_k, \sigma _k)\), return 1 if \(k\ge \ell _{\texttt{closed}}+1\) and \(\mathcal {V}(\textsf{pk}, \sigma _i, m_i) = 1\) for all \(1\le i\le k\). Otherwise, return 0.
We define the advantage of \(\mathcal {A}\) as
where the probability goes over the randomness of the game as well as the randomness of the adversary \(\mathcal {A}\). We say the scheme \({{\,\mathrm{\textsf{BS}}\,}}\) is \(\ell \)-one-more unforgeable if for any adversary \(\mathcal {A}\) that makes at most \(\ell \) queries to \(\textsf{sign}_1\), the following holds:
3 Mix-and-Match Attacks
This section presents three attacks against the one-more-unforgeability of blind signature schemes based on \(\varSigma \)-protocols. The first two attacks center on concurrent security, and the third focuses on sequential security. We also briefly demonstrate the first two attacks in Figs. 3 and 4.
3.1 Schnorr-Type Blind Signatures
Many blind signature schemes, such as the Schnorr Blind Signature [11], the Abe-Okamoto scheme [1] or the more recent CSI-Otter [22], are based on an underlying sigma protocol. We will call the schemes following this paradigm Schnorr-type blind signatures.
Definition 4
Let \({{\,\mathrm{\textsf{BS}}\,}}= (\mathcal {G}, \mathcal {S}, \mathcal {U}, \mathcal {V})\) be a blind signature. We say that \({{\,\mathrm{\textsf{BS}}\,}}\) is of Schnorr-type if there exists a sigma protocol \(\varSigma = (\mathcal {G}_{\varSigma }, \mathcal {P}_{\varSigma }, \mathcal {V}_{\varSigma }, \mathcal {C}_{\varSigma })\) and an hash function \(\mathcal {H}:\{0,1\}^{\star }\rightarrow \mathcal {C}_{\varSigma }\) such that:
-
1.
\(\mathcal {G}= \mathcal {G}_{\varSigma }\), and \(\mathcal {V}_{\varSigma }\) is as in the Fiat-Shamir’s construction.
-
2.
\(\mathcal {S}= \mathcal {P}_{\varSigma }\). So, in particular, we have that \(\textsf{S}_1 = \textsf{P}_1\) and \(\textsf{S}_2 = \textsf{P}_2\).
We also require the following property on the user \(\mathcal {U}= ({{\,\mathrm{\textsf{U}}\,}}_1, {{\,\mathrm{\textsf{U}}\,}}_2)\):
-
3.
there exists algorithms \({{\,\mathrm{\textsf{U}}\,}}_1.\textsf{BlindCom},\ {{\,\mathrm{\textsf{U}}\,}}_1.\textsf{BlindChal}\) and \({{\,\mathrm{\textsf{U}}\,}}_2.\textsf{BlindResp}\) such that:
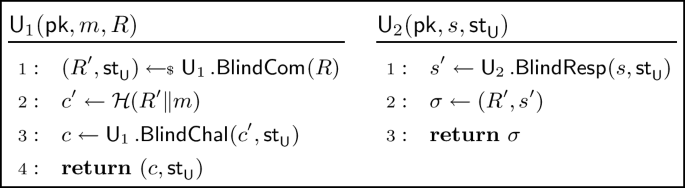
We will denote such a blind signature as \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }\).
Like sigma protocols, given a Schnorr-type blind signature \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }\) with challenge space \(\mathcal {C}\), we can construct (by taking parallel repetitions) another blind signature scheme with challenge space \(\mathcal {C}^k\) for any \(k\in \mathbb {N}\). We will denote it as \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\).
3.2 Main Attack
In this attack, the adversary initiates k concurrent sessions and obtains \(k + 1\) valid signatures.
The main attack depicted for the special case \(k = 4\). The rows of the matrix are the signer’s commitments \(\textbf{R}_{1},\dots , \textbf{R}_4\) of the four sessions. The row at the bottom represents the simulated instances of the \(\varSigma \)-protocol used to replace the last instances in the signer’s commitment, which are used to generate a forgery with commitment \(\textbf{R}_5\).
Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k = (\mathcal {G}, \mathcal {S}, \mathcal {U}, \mathcal {V})\) be a k-parallel repetition of a Schnorr-type blind signature where \(k = k(n)\) is a positive integer depending on n. Let \(\varSigma = (\mathcal {G}_{\varSigma }, \mathcal {P}_{\varSigma }, \mathcal {V}_{\varSigma }, \mathcal {C}_{\varSigma })\) be the underlying sigma protocol. We have, by construction, that the challenge space of \({{\,\mathrm{\textsf{BS}}\,}}\) is equal to \(\mathcal {C}_{\varSigma }^k\) and the signer \(\mathcal {S}\) is equal to \(\mathcal {P}_{\varSigma }^k\). The attacker \(\mathcal {A}\) will proceed as follows.
-
1.
It opens k concurrent sessions \({{\,\mathrm{\textsf{BS}}\,}}^{(1)},\dots , {{\,\mathrm{\textsf{BS}}\,}}^{(k)}\) with \(\mathcal {S}\). Let \(\textbf{R}_i\) be the commitment sent by \(\mathcal {S}\) in the ith session. Since \(\mathcal {S}= \mathcal {P}_{\varSigma }^k\), we can write
$$ \textbf{R}_{i} = (R_{i, 1},\dots , R_{i, k}) $$where \(R_{i,j}\leftarrow _{\$} \textsf{P}_1(\textsf{sk})\) for any \(i,j\in [k]\).
-
2.
From that, the attacker constructs a new fake signer commitment as
$$ \textbf{R}_{k+1} = (R_{1 ,k}, \dots , R_{k, k}). $$Let \(\textbf{R}'_{k+1}\leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(\textbf{R}_{k+1})\), \(\textbf{c}_{k+1}\leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_{k+1})\) be the blinded commitment and challenge respectively, where \(\textbf{c}'_{k+1} = \mathcal {H}(\textbf{R}'_{k+1}\Vert m_{k+1})\) for a message \(m_{k+1}\in \{0,1\}^{\star }\) picked at random.
In addition, it computes k valid transcriptsFootnote 1 \((e_i, d_i, z_i),\ i\in [k],\) of the underlying sigma protocol for random challenges \(d_{i}\).
-
3.
To construct a valid response for the challenge \(\textbf{c}'_{k+1}\), \(\mathcal {A}\) interacts with \(\mathcal {S}\) as follows. For each opened session \({{\,\mathrm{\textsf{BS}}\,}}^{(i)}\), the attacker replaces \(\textbf{R}_i\) with \(\widetilde{\textbf{R}}_{i} = (R_{i,1}, \dots , R_{i, k-1}, e_i)\) and blinds it as
$$\begin{aligned} \textbf{R}'_i = (R'_{i,1}, \dots , R'_{i, k-1}, e_i), \end{aligned}$$(1)where, for \(j \in [k-1]\), \(R'_{i,j}\leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(R_{i,j})\). The attacker then finds a message \(m_i\) such that the last entry of \(\textbf{c}'_{i} = \mathcal {H}(\textbf{R}'_{i}\Vert m_i)\) is equal to \(d_i\). For random messages \(m_i\) this happens after \(O(|\mathcal {C}_{\varSigma }|)\) queries of the hash functionFootnote 2. In this way, it will be able to ask the signer the response for the challenge of the forgery. \(\mathcal {A}\) then sends to the signer the blinded challenge
$$ \textbf{c}_i = (c_{i,1},\dots , c_{i, k-1}, c_{k+1, i}), $$where \(c_{i,j} \leftarrow _{\$} {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(c'_{i,j})\) for \(j\in [k-1]\), and receives the response \(\textbf{s}_i\) from \(\mathcal {S}\), where \(\textbf{s}_i\leftarrow \textsf{S}_2(\textsf{sk}, \textbf{c}_i)\). The attacker now blinds the response as
$$\begin{aligned} \textbf{s}'_i = (s'_{i,1},\dots , s'_{i, k-1}, z_i), \end{aligned}$$(2)where \(s'_{i,j} \leftarrow _{\$} {{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}(s_{i,j})\) for \(j\in [k-1]\), and closes session \({{\,\mathrm{\textsf{BS}}\,}}^{(i)}\).
-
4.
Finally, the attacker sets the response for \(\textbf{c}'_{k+1}\) to
$$\begin{aligned} \textbf{s}'_{k+1} = (s'_{1 ,k},\dots , s'_{k, k}), \end{aligned}$$(3)where \(s'_{i,k} \leftarrow _{\$} {{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}(s_{i,k})\) for \(i\in [k]\). To conclude, \(\mathcal {A}\) outputs \(k+1\) signatures:
$$ (m_i, (\textbf{R}'_i,\textbf{s}'_i)),\ \text {for } i \in [k+1]. $$
Lemma 1
For all \(i = 1,\dots , k+1\) the pair \((\textbf{R}'_i,\textbf{s}'_i)\) is a valid signature for the message \(m_i\).
Proof
We distinguish two cases: \(i\le k\) and \(i = k+1\).
-
\(i\le k.\) From Eq. 1 we have \(\textbf{R}'_i = (R'_{i,1}, \dots , R'_{i, k-1}, e_i)\) and from 2 that \(\textbf{s}'_i = (s'_{i,1},\dots , s'_{i, k-1}, z_i)\). Let \(\textbf{c}'_{i} = \mathcal {H}(\textbf{R}'_i\Vert m_i)\). For \(j \in [k-1]\), \(R'_{i, j}\) and \(s'_{i, j}\) are honestly generated following \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }\), therefore
$$ \mathcal {V}_{\varSigma }(\textsf{pk}, R'_{i, j}, c'_{i,j}, s'_{i,j}) = 1\ \ \forall j\in [k-1] $$In addition, by construction, \(c'_{i, k} = d_i\) and \((e_i, d_i, z_i)\) is a valid transcript for \(\varSigma \), hence \(\mathcal {V}_{\varSigma }(\textsf{pk}, e_{i}, d_{i}, z_{i}) = 1\). Therefore
$$ \mathcal {V}_{{{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k}(\textsf{pk}, m_i, (\textbf{R}'_i,\textbf{s}'_i)) = 1. $$ -
\(i = k+1.\) Let \(\textbf{R}'_{k+1} \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(\textbf{R}_{k+1})\), \(\textbf{c}'_{k+1} = \mathcal {H}(\textbf{R}'_{k+1}\Vert m_{k+1})\) and also let \(\textbf{c}_{k+1}\leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_{k+1})\) as in step 2 above. By Eq. 3 we have \(\textbf{s}'_{k+1} = (s'_{1 ,k},\dots , s'_{k, k})\) where \(s_{j, k}\) is the blinded response of the signer for the challenge \(c_{k+1, j}\) and commitment \(R_{j, k}\). Therefore
$$ \mathcal {V}_{\varSigma }(\textsf{pk}, R'_{k+1, 1}, c'_{k+1,j}, s'_{j ,k}) = 1\ \ \forall j\in [k-1]. $$and hence \(\mathcal {V}_{{{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k}(\textsf{pk}, m_{k+1}, (\textbf{R}'_{k+1},\textbf{s}'_{k+1})) = 1\)
We have just proved the following:
Theorem 1
Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) be a parallel repetition of a Schnorr-type blind signature scheme supporting at most k concurrent sessions. There exists an adversary \(\mathcal {A}\) against the \(\ell \)-one-more unforgeability game, for \(\ell = k\), such that
and asking \(O(k\cdot |\mathcal {C}_{\varSigma }|)\) queries to the hash function, where \(\mathcal {C}_{\varSigma }\) is the challenge space of the base sigma protocol.
The 2 out of k attack when \(k = 3\). The vectors \(\textbf{R}_1, \textbf{R}_2, \textbf{R}_3\) are the signer commitments. The attacker will replace them with \(\textbf{R}'_1, \textbf{R}'_2, \textbf{R}'_3\) in order to get the forgery. On the right side, we depict the commitments used for the 3 standard signatures, while the left side represents the order of the challenges asked to the signer. At the top, we have the forgery with commitment \(\textbf{R}_4\) that in this scenario corresponds to \(\textbf{R}_3\).
As previously mentioned in the introduction, the above attack can be generalized as follows. Instead of brute force one challenge, \(\mathcal {A}\) will go for t consecutive challenges for some \(1\le t \le k\). In this way, by opening \(s = \lceil k/t\rceil \) concurrent sessions and making \(O(|\mathcal {C}_{\varSigma }|^t)\) queries to the hash function for each of them, it will get \(s + 1\) signatures.
Theorem 2
Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) be a parallel repetition of a Schnorr-type blind signature scheme supporting at most \(s = \lceil k/t\rceil \) concurrent sessions for some \(1\le t\le k\). There exists an adversary \(\mathcal {A}\) against the \(\ell \)-one-more unforgeability game, for \(\ell = s\), such that,
and asking \(O(s\cdot |\mathcal {C}_{\varSigma }|^t)\) queries to the hash function, where \(\mathcal {C}_{\varSigma }\) is the challenge space of the base sigma protocol.
3.3 Two Out of k Attack
In this attack, the adversary employs \(k - 1\) pairs of concurrent sessions, totaling k sessions, to get \(k + 1\) signatures. More precisely, we will construct an adversary \(\mathcal {A}\) against the k-one-more unforgeability for a Schnorr-type blind signature that supports at most two concurrent sessions at a given time. Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) be as in the previous section. For simplicity, we will present the adversary \(\mathcal {A}\) in the particular case \(k = 3\). However, the attack generalized easily, and we will prove its correctness for an arbitrary k. The attacker proceeds as follows.
-
1.
It first opens two concurrent sessions \({{\,\mathrm{\textsf{BS}}\,}}^{(1)}, {{\,\mathrm{\textsf{BS}}\,}}^{(2)}\). Let \(\textbf{R}_1 = (R_{1,1}, R_{1, 2}, R_{1,3})\) and \(\textbf{R}_2 = (R_{2,1}, R_{2,2}, R_{2,3})\) be the commitments sent by the signer in the first and second session respectively. Also, let \(\widetilde{\textbf{R}}_1 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(\textbf{R}_1)\) and \(\widetilde{\textbf{R}}_2 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(\textbf{R}_2)\) be the blinded commitments.
-
2.
\(\mathcal {A}\) now computes two valid transcripts \((e_1, d_1, z_1)\) and \((e_2, d_2, z_2)\) of the underlying sigma protocol for random challenges \(d_1\) and \(d_2\). Set \(\textbf{R}'_1 = (e_1, \widetilde{R}_{1,2}, \widetilde{R}_{1,3})\) and \(\textbf{R}'_2 = (e_2, \widetilde{R}_{1,1}, \widetilde{R}_{2,3})\). Then, the attacker searches for two messages \(m_1, m_2\) such that \(\textbf{c}'_1 = \mathcal {H}(\textbf{R}'_1\Vert m_1)\) and \(\textbf{c}'_2 = \mathcal {H}(\textbf{R}'_2\Vert m_2)\) have the first component equal to \(d_1\) and \(d_2\) respectively. As before, this can be achieved with \(O(|\mathcal {C}_{\varSigma }|)\) queries to the hash function.
-
3.
The attacker computes \(\widetilde{\textbf{c}}_1 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_1)\) and \(\widetilde{\textbf{c}}_2 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_2)\), and sends to the signer, in the first session, the challenge \(\textbf{c}_1 = (\widetilde{c}_{2,2}, \widetilde{c}_{1,2}, \widetilde{c}_{1,3})\). Upon receiving the response \(\textbf{s}_1\) from the signer, \(\mathcal {A}\) blinds it by computing \(\widetilde{\textbf{s}}_{1}\leftarrow {{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}(\textbf{s}_{1})\) and sets
$$ \textbf{s}'_1 = (z_1, \widetilde{s}_{1,2}, \widetilde{s}_{1,3}). $$It outputs \((m_1, (\textbf{R}'_1, \textbf{s}'_1))\) and closes \({{\,\mathrm{\textsf{BS}}\,}}^{(1)}\).
-
4.
Now \(\mathcal {A}\) opens the third session \({{\,\mathrm{\textsf{BS}}\,}}^{(3)}\). Note that two concurrent sessions are open at the moment. Let \(\textbf{R}_3 = (R_{3,1}, R_{3,2}, R_{3,3})\) be the commitment sent by the signer and let \(\widetilde{\textbf{R}}_3 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}(\textbf{R}_3)\) be the blinded commitment. It creates a valid transcript of the underlying sigma protocol \((e_3, d_3, z_3)\) for a random challenge \(d_3\) and sets \(\textbf{R}'_3 = (e_3, \widetilde{R}_{2,1}, \widetilde{R}_{2,2})\). As before, searches for a message \(m_3\) such that \(\textbf{c}'_3 = \mathcal {H}(\textbf{R}'_3\Vert m_3)\) has the first component equal to \(d_3\).
-
5.
Similarly to Step 3 above, the attacker computes \(\widetilde{\textbf{c}}_3 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_3)\) and sends to the signer, in the second session, the challenge \(\textbf{c}_2 = (\widetilde{c}_{3,2}, \widetilde{c}_{3,3}, \widetilde{c}_{2,3})\). Upon receiving the response \(\textbf{s}_2\) from the signer in session two, \(\mathcal {A}\) computes the blinded response as \(\widetilde{\textbf{s}}_2\leftarrow {{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}(\textbf{s}_2)\) and sets
$$ \textbf{s}'_2 = (z_2, \widetilde{s}_{1,1}, \widetilde{s}_{2,3}). $$It outputs \((m_2, (\textbf{R}'_2, \textbf{s}'_2))\) and closes \({{\,\mathrm{\textsf{BS}}\,}}^{(2)}\).
-
6.
Now only one session, \({{\,\mathrm{\textsf{BS}}\,}}^{(3)}\), is open. It sets \(\textbf{R}'_4 = \widetilde{\textbf{R}}_3\) and \(\textbf{c}'_4 = \mathcal {H}(\textbf{R}'_4\Vert m_4)\). \(\mathcal {A}\) will ask the server in \({{\,\mathrm{\textsf{BS}}\,}}^{(3)}\) to respond for this challenge. It hence computes \(\widetilde{\textbf{c}}_4 \leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\textbf{c}'_4)\) and sends to \(\mathcal {S}\), in the third session, the challenge \(\textbf{c}_3 = (\widetilde{c}_{4,1}, \widetilde{c}_{4,2}, \widetilde{c}_{4,3})\). Upon receiving the response \(\textbf{s}_3\) from the signer, \(\mathcal {A}\) blinds it as \(\widetilde{\textbf{s}}_3\) and sets
$$ \textbf{s}'_3 = (z_3, \widetilde{s}_{2,1}, \widetilde{s}_{2,2}), $$and
$$ \textbf{s}'_4 = (\widetilde{s}_{3,1}, \widetilde{s}_{3,2}, \widetilde{s}_{3,3}) $$It outputs \((m_3, (\textbf{R}'_3, \textbf{s}'_3))\), the forgery \((m_4, (\textbf{R}'_4, \textbf{s}'_4))\), and closes \({{\,\mathrm{\textsf{BS}}\,}}^{(3)}\).
Lemma 2
For all \(i = 1,\dots , k+1\) the pair \((\textbf{R}'_i,\textbf{s}'_i)\) is a valid signature for the message \(m_i\).
Proof
We will distinguish two cases like in lemma 1.
-
\(i \le k.\) We have by construction
$$ \textbf{R}'_{i} = (e_i, \underbrace{\widetilde{R}_{i -1, 1}, \dots , \widetilde{R}_{i-1, i-1}}_\text {i - 1 terms}, \underbrace{\widetilde{R}_{i,i+1}, \dots , \widetilde{R}_{i, k}}_\text {k - i terms}), $$$$ \textbf{c}'_i = \mathcal {H}(\textbf{R}'_{i}\Vert m_i) = (c'_{i,1},\dots , c'_{i, k}), $$and
$$ \textbf{s}'_{i} = (z_i, \underbrace{\widetilde{s}_{i -1, 1}, \dots , \widetilde{s}_{i-1, i-1}}_\text {i - 1 terms}, \underbrace{\widetilde{s}_{i,i+1}, \dots , \widetilde{s}_{i, k}}_\text {k - i terms}). $$Since \(c'_{i, 1} = d_i\) by construction, we have \(\mathcal {V}_{\varSigma }(\textsf{pk}, e_i, d_i, z_i) = 1\). Moreover, for all \(1\le j \le i -1\), we have \(\mathcal {V}_{\varSigma }(\textsf{pk}, \widetilde{R}_{i -1, j}, c_{i,j}, \widetilde{s}_{i -1, j}) = 1\). Similarly, \(\mathcal {V}_{\varSigma }(\textsf{pk}, \widetilde{R}_{i , j}, c_{i,j}, \widetilde{s}_{i, j}) = 1\) for all \(i+1\le j \le k\). We therefore have
$$ \mathcal {V}_{{{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k}(\textsf{pk}, m_i, (\textbf{R}'_i, \textbf{s}'_i)) = 1. $$ -
\(i = k+1.\) In this case we have
$$ \textbf{R}'_{k+1} = (\widetilde{R}_{k,1},\dots ,\widetilde{R}_{k,k}), $$$$ \textbf{c}'_{k+1} = \mathcal {H}(\textbf{R}'_{i}\Vert m_i) = (c'_{k,1},\dots , c'_{k, k}) $$and
$$ \textbf{s}'_{k+1} = (\widetilde{s}_{k,1},\dots ,\widetilde{s}_{k,k}). $$From the description of the attack we have \(\mathcal {V}_{\varSigma }(\textsf{pk}, \widetilde{R}_{k , j}, c_{k,j}, \widetilde{s}_{k, j}) = 1\) for any \( j\in [k]\) and hence
$$ \mathcal {V}_{{{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k}(\textsf{pk}, m_{k+1}, (\textbf{R}'_{k+1}, \textbf{s}'_{k+1})) = 1. $$
We have just proved the following theorem:
Theorem 3
Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) be (a parallel repetition of) a Schnorr-type blind signature scheme supporting at most two concurrent sessions. There exists an adversary \(\mathcal {A}\) against the \(\ell \)-one-more unforgeability game, for \(\ell = k\), such that
and asking \(O(k\cdot |\mathcal {C}_{\varSigma }|)\) queries to the hash function, where \(\mathcal {C}_{\varSigma }\) is the challenge space of the base sigma protocol.
3.4 One Out of One Attack
In this attack, the adversary, by opening only one session with the signer, obtains two signatures. This, however, comes with a trade-off of exponential computational cost. More precisely, suppose the attacker cannot open concurrent sessions, i.e., sequential setting. We will show how the attacker can produce two valid signatures after one session with the signer. Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}^k_{\varSigma }\) be the blind signature scheme. Suppose, for simplicity, the number of repetition k is an even number and set \(t = k/2\). We construct \(\mathcal {A}\) as follows.
-
1.
The attacker opens one session \({{\,\mathrm{\textsf{BS}}\,}}\) with the signer. Let \(\textbf{R} = (R_1,\dots , R_k)\) be the signer commitment and let:
$$ \textbf{R}' = (R'_1,\dots , R'_k), $$be the blinded commitment.
-
2.
For any \(1\le i\le k\), \(\mathcal {A}\) will generate k valid transcripts \((r_i, d_i, z_i)\) for the underlining \(\varSigma \)-protocol, and define
$$ \textbf{R}'_1 = (r_1,\dots , r_t, R'_1,\dots , R'_t), $$and
$$ \textbf{R}'_2 = (r_{t+1}, \dots , r_k, R'_{t+1}, \dots , R'_k). $$It will then search for two messages \(m_1\) and \(m_2\) such that:
$$ \textbf{c}'_1 = \mathcal {H}(\textbf{R}'_1\Vert m_1) = (d_1,\dots ,d_t,c'_{1,t+1},\dots , c'_{1, k}) $$and
$$ \textbf{c}'_2 = \mathcal {H}(\textbf{R}'_2\Vert m_2) = (d_{t+1},\dots ,d_k,c'_{2,t+1},\dots , c'_{2, k}). $$This will require \(O(|\mathcal {C}_{\varSigma }|^t)\) queries to the hash funcion \(\mathcal {H}\).
-
3.
The attacker now sets \(\widetilde{\textbf{c}} = (c'_{1,t+1},\dots , c'_{1, k}, c'_{2,t+1},\dots , c'_{2, k})\), then blinds it as \(\textbf{c}\leftarrow {{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}(\widetilde{\textbf{c}})\) and sends this to the signer. Upon receiving the response \(\textbf{s}\), it blinds it as \(\widetilde{\textbf{s}}\leftarrow {{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}(\textbf{s})\) and sets
$$ \textbf{s}'_1 = (z_1, \dots , z_t, \widetilde{s}_1, \dots , \widetilde{s}_t), $$and
$$ \textbf{s}'_2 = (z_{t+1}, \dots , z_k, \widetilde{s}_{t+1}, \dots , \widetilde{s}_k). $$ -
4.
The attacker will close the session and output \((m_1, (\textbf{R}'_1, \textbf{s}'_1))\), and \((m_2, (\textbf{R}'_2, \textbf{s}'_2))\).
Lemma 3
The pairs \((\textbf{R}'_1, \textbf{s}'_1)\) and \((\textbf{R}'_2, \textbf{s}'_2)\) are valid signatures for the messages \(m_1\) and \(m_2\) respectively.
Proof
The proof of this theorem is analogous to that of lemma 1, and hence it will be omitted.
Theorem 4
Let \({{\,\mathrm{\textsf{BS}}\,}}= {{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) be a parallel repetition of a Schnorr-type blind signature scheme not supporting any concurrent sessions. There exists an adversary \(\mathcal {A}\) against the \(\ell \)-one-more unforgeability game, for \(\ell = 1\), such that
and asking \(O(2\cdot |\mathcal {C}_{\varSigma }|^t)\) queries to the hash function, where \(\mathcal {C}_{\varSigma }\) is the challenge space of the base sigma protocol and \(t = \lceil k/2\rceil \).
4 Cryptanalysis of CSI-Otter
As a concrete example, we will apply our attack to the isogeny-based blind signature scheme CSI-Otter [22] as one of the state-of-the-art blind signatures based on \(\varSigma \)-protocols.
4.1 Cryptographic Group Actions
The scheme we will describe is based on cryptographic group actions with twist [8, 15, 27]. We will, therefore, provide some background.
Definition 5
(Group Action). We say that a group \((G, +)\) acts on a set X if there exists a function \(\star : G\times X\rightarrow X\) satisfying the following properties.
-
1.
Identity: for any \(x\in X\), we have \(0\star x=x\) where 0 is the identity element of G.
-
2.
Compatibility: for any \(g,h\in G\) and any \(x\in X\), we have \((g + h)\star x = g\star (h\star x)\).
-
3.
Transitivity: for every \(x_1, x_2 \in X\), there exists a group element \(g \in G\) such that \(x_2 = g \star x_1\).
-
4.
Free: for each group element \(g \in G\), g is the identity element if and only if there exists some set element \(x \in X\) such that \(x = g \star x\).
We will say, for brevity, that \((G, X, \star )\) is a group action.
Let \((G, X, \star )\) be a group action and \(x_0\in X\) a set element. It follows from the definition that, every \(x\in X\) can be written as \(x = g\star x_0\) for a (unique) \(g\in G\). We define the twist of a set element \(x = g\star x_0\) as \(x^{-1} = (-g)\star x_0\).
The specific group action used in CSI-Otter is the CSIDH-512 action defined in [8]. In particular, X is the set of supersingular elliptic curvesFootnote 3 over \(\mathbb {F}_p\) with \(\mathbb {F}_p\)-rational endomorphism ring isomorphicFootnote 4 to an order \(\mathcal {O}\subseteq \mathbb {Q}(\sqrt{-p})\); the group G is the ideal class group \(\mathcal {C}\ell (\mathcal {O})\) acting on X via isogeny; and \(x_0 = E_0\) is the curveFootnote 5 defined by:
We also remark that, for this specific action, the twist can be efficiently computed for every \(x\in X\) [31]. For the cryptographic definitions of security, we refer to [2].
4.2 The Scheme
Let \((G, X, \star )\) be a cryptographic group action with twist, and let \(x_0\in X\) be a set element. Recall that \(x^{-1}\) represents the twist of \(x\in X\). We now describe the blind signature scheme presented in [22]. In the underlying sigma protocol, the prover \(\mathcal {P}\) holds a secret key \(\textsf{sk}= (\delta , a_{\delta })\in \{0,1\}\times G\) and a public key \(\textsf{pk}= (y_0, y_1) = ({a_0}\star x_0, {a_1}\star x_0)\). The interaction is described in Fig. 5. This \(\varSigma \)-protocol is correct, special sound and honest verifier zero-knowledge [5]. For the latter property, we can construct a simulator \(\textsf{Sim}\) that, given a challenge \(c\in \{-1, 1\}\) and a public key \((y_0, y_1)\), samples random
 and
and
 conditioned on \(c_0 \cdot c_1 = c\). It then sets \(R_b = r_b \star y^c_b\) for \(b \in \{0,1\}\), and outputs the simulated transcript \(((R_0, R_1),\ c,\ (r_0, r_1, c_0, c_1))\).
conditioned on \(c_0 \cdot c_1 = c\). It then sets \(R_b = r_b \star y^c_b\) for \(b \in \{0,1\}\), and outputs the simulated transcript \(((R_0, R_1),\ c,\ (r_0, r_1, c_0, c_1))\).
The blind signature scheme \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma } = (\mathcal {G}, \mathcal {U}, \mathcal {S}, \mathcal {V})\) is defined as follows:
-
\(\mathcal {G}(1^n):\) On input the security parameter \(1^n\), it samples a bit
 , a pair
, a pair
 and outputs a public key \(\textsf{pk}= (y_0,y_1) = (a_0\star x_0,a_1\star x_0)\) and secret key \(\textsf{sk}= (\delta , a_{\delta })\).
and outputs a public key \(\textsf{pk}= (y_0,y_1) = (a_0\star x_0,a_1\star x_0)\) and secret key \(\textsf{sk}= (\delta , a_{\delta })\). -
\({{\,\mathrm{\textsf{S}}\,}}_1(\textsf{sk}):\) The signer first samples
 and sets \(R_{\delta } = r_{\delta } \star x_0\). It then samples
and sets \(R_{\delta } = r_{\delta } \star x_0\). It then samples
 and sets \(R_{1-\delta } = {r_{1-\delta }}\star y_{1-\delta }^{c_{1-\delta }}\). It then outputs the signer state \(\textsf{st}_{{{\,\mathrm{\textsf{S}}\,}}} = (r_{\delta }, c_{1-\delta }, r_{1-\delta })\) and the signer commitment \(R = (R_0, R_1)\).
and sets \(R_{1-\delta } = {r_{1-\delta }}\star y_{1-\delta }^{c_{1-\delta }}\). It then outputs the signer state \(\textsf{st}_{{{\,\mathrm{\textsf{S}}\,}}} = (r_{\delta }, c_{1-\delta }, r_{1-\delta })\) and the signer commitment \(R = (R_0, R_1)\). -
\({{\,\mathrm{\textsf{U}}\,}}_1(\textsf{pk}, m, R):\) The user parses \((R_0, R_1) \leftarrow R\), samples
 , and computes \(R'_b = {t_b} \star (R_b)^{e_b}\) for \(b \in \{0, 1\}\). It then computes \(c' = \mathcal {H}(R'_0\Vert R'_1\Vert m)\) and outputs the user state \(\textsf{st}_{{{\,\mathrm{\textsf{U}}\,}}} = (e_b, t_b)_{b\in \{0,1\}}\) and user message \(c = c' \cdot e_0 \cdot e_1\).
, and computes \(R'_b = {t_b} \star (R_b)^{e_b}\) for \(b \in \{0, 1\}\). It then computes \(c' = \mathcal {H}(R'_0\Vert R'_1\Vert m)\) and outputs the user state \(\textsf{st}_{{{\,\mathrm{\textsf{U}}\,}}} = (e_b, t_b)_{b\in \{0,1\}}\) and user message \(c = c' \cdot e_0 \cdot e_1\). -
\({{\,\mathrm{\textsf{S}}\,}}_2(\textsf{sk}, c, \textsf{st}_{{{\,\mathrm{\textsf{S}}\,}}}):\) The signer parses \((r_{\delta }, c_{1-\delta }, r_{1-\delta }) \leftarrow \textsf{st}_{{{\,\mathrm{\textsf{S}}\,}}}\), sets \(c_{\delta } = c \cdot c_{1-\delta } \in \{-1, 1\}\), and updates \(r_{\delta } \leftarrow r_{\delta } - a_{\delta }\cdot c_{\delta }\in G\). It then outputs the signer response \(s = (c_b, r_b)_{b\in \{0,1\}}\).
-
\({{\,\mathrm{\textsf{U}}\,}}_2(\textsf{pk}, s, \textsf{st}_{{{\,\mathrm{\textsf{U}}\,}}}):\) The user parses \((e_b , t_b)_{b\in \{0,1\}} \leftarrow \textsf{st}_{{{\,\mathrm{\textsf{U}}\,}}}\), \((c_b , r_b )_{b\in \{0,1\}} \leftarrow s\) and sets \((c'_b , r'_b ) = (c_b \cdot e_b, t_b + r_b \cdot e_b)\) for \(b \in \{0, 1\}\). It then checks if
$$\begin{aligned} c'_0 \cdot c'_1 = \mathcal {H}({r'_0}\star y_0^{c'_0}\Vert {r'_1}\star y_1^{c'_1}\Vert m). \end{aligned}$$(4)If it holds, it outputs a signature \(\sigma = (c'_b , r'_b )_{b\in \{0,1\}} \in (\{-1, 1\} \times G)^2\), and otherwise a \(\perp \).
-
\(\mathcal {V}(\textsf{pk}, m, \sigma ):\) The verifier outputs 1 if Eq. 4 holds, and otherwise 0.
This is, in fact, a Schnorr-type blind signature. It is clear from the construction that \({{\,\mathrm{\textsf{S}}\,}}_1 = \textsf{P}_1\) and \({{\,\mathrm{\textsf{S}}\,}}_2 = \textsf{P}_2\), and we have the following table for the user.

Blue lines represent the function \({{\,\mathrm{\textsf{U}_1.\textsf{BlindCom}}\,}}\); the line yellow represents \({{\,\mathrm{\textsf{U}_1.\textsf{BlindChal}}\,}}\) and the violet \({{\,\mathrm{\textsf{U}_2.\textsf{BlindResp}}\,}}\). It follows, now, that the blind signature \({{\,\mathrm{\textsf{BS}}\,}}_{\varSigma }^k\) is vulnerable to our attacks since the base challenge space \(\mathcal {C}_{\varSigma }\) has cardinality 2 and k is linear in the security parameter n.
5 Discussion
This section discusses potential ways of circumventing our attack in the concurrent setting, their downsides, and implications on the efficiency and practicality of the blind signature vulnerable to our attack. We also discuss implications on sequential security, particularly a concrete treatment of those schemes in the post-quantum setting.
5.1 Concurrent Security
For our mix-and-match attack to work, the adversary must be able to initiate and finalize k signing sessions where the signer supports at least two concurrent sessions at a time. The parameter k depends on the challenge space \(\mathcal {C}_{\varSigma }\) of the underlying \(\varSigma \)-protocol, e.g., in the case of CSI-Otter, the authors use the challenge space \(\mathcal {C}_{\varSigma } = \{-1,1\}\) and set the number of repetitions to \(k = 128\). This parameter is usually polynomial in the security parameter to ensure that the soundness error for the augmented \(\varSigma \)-protocol is negligible while keeping it small to ensure efficiency. For almost all practical applications, the parameter \(k = 128\) ensures that the soundness error of the \(\varSigma \)-protocol is negligible for 128-bit security. Thus, in most cases, any blind signature scheme from \(\varSigma \)-protocol with small challenge space will be forgeable after just around a hundred signed messages.
A potential way to circumvent our attack is to increase k since it is allowed to be polynomial in the security parameter. This way, the number of supported signatures will also be polynomial in the security parameter, where the polynomial can be freely chosen. Unfortunately, this approach will significantly decrease the efficiency of the used scheme. Let us discuss this on the CSI-Otter example. Doubling the parameter k to 256 will also double the number of signatures, allowing for one forgery, i.e., from 128 to 256 (note that we are considering the main attack here). At the same time, the communication complexity of the exchange and the signature size will also be doubled. We usually set parameters for a standard digital signature scheme so that one key pair can be used to sign around \(2^{30}\). To achieve a similar property while protecting against our main attack, we must set \(k = 2^{30}\), leading to signatures in the gigabytes and inefficient computations.
Increasing the parameter k provides a simple fix that increases the number of concurrent sessions the blind signature can provide. Asymptotically, the scheme offers the required security, but it is impractical if we want a genuinely usable scheme supporting many signatures. Note that a signer can continuously refresh the key pair, which is not a problem for standard digital signatures but decreases the anonymity set in the blind signature setting.
An alternative approach would be to employ boosting transformations [9, 24] known and used for the Schnorr blind signature scheme vulnerable to the ROS attack. Those solutions employ cut-and-choose techniques that allow the reduction to limit the number of signing queries while providing more questions to the adversary, i.e., in the case of Schnorr signatures, the adversary is allowed to do polynomially many queries in the security parameter while at the same time, the reduction only queries the signing oracle at most a logarithmic number of times. Similar techniques could be employed for the class of blind signatures considered in this paper. Contrary to increasing the parameter k, this approach increases the communication and signature size by a smaller factor than in the previous solution, making it more efficient. However, it is still impractical and not comparable to other blind signature schemes, e.g., applying this technique to CSI-Otter would still make it less efficient than state-of-the-art schemes based on lattices.
Interestingly, [23] proposes a definition for a new version of the ROS problem called “parallel ROS” and shows that it applies to the concurrent security of CSI-Otter [22]. This attack is similar to ours, particularly in terms of efficiency. However, the only solution to the problem diverges from the fundamental concept of the ROS problem, which involves computing a signature through linear combinations of queried signatures. For this reason, we prioritized substance over form, as our generic approach enables broader application.
5.2 Sequential Security
Using the threshold variant of our attack, an adversary can compute two valid signatures using only one signing session in \(O(2^{k/2})\) number of hash evaluations. Thus, launching a practical attack in the sequential setting against CSI-Otter with the proposed parameters \(k = 128\) requires around \(2 \cdot 2 \cdot 2^{64}\) hash evaluation in expectation. This amount of computation is less than the work required by miners to add a new block to the Bitcoin blockchain. In particular, this means that the Bitcoin mining pool can, with non-negligible probability, forge CSI-Otter signatures even in the sequential setting in around 10 min for the parameter proposed by the authors.
Our results show that assuming the underlying \(\varSigma \)-protocol has a negligible soundness error for a parameter \(k_\varSigma \), e.g., \(k_\varSigma = n\), then, we need to set the parameter k for the blind signature to \(k = 2 \cdot k_\varSigma \), i.e., in the case of \(k_\varSigma = n\) this will lead to \(k = 2 \cdot n\). In the case of CSI-Otter, this means that to get around the above sequential attack, the parameter k must be set to \(2 \cdot 128 = 256\).
The above considerations are only for the classical setting and do not treat the hash function in the post-quantum scenario. In this setting, we can accelerate the adversary’s computation using Grover’s algorithm on quantum computers [18]. In particular, the problem the adversary must solve is to find a message m for which \(\mathcal {H}(\textbf{R} || m ) = a b\) for fixed commitments \(\textbf{R}\) and prefix a. As shown in [30] the adversary’s work will be reduced to \(O(2^{\frac{k}{4}})\). Therefore, the parameter k must be increased four times for the scheme to be secure against a quantum attacker.
5.3 Revisiting CSI-Otter Parameters
We will now discuss concrete parameters for CSI-Otter [22]. The authors in the original paper propose two variants: one with challenge space \(\{-1,1\}\) with \(k = 128\) repetitions and an optimized variant with a challenge space of size 4 with \(k = 64\) repetitions. In both cases, our main attack can forge a new signature with 128 and 64 concurrent sessions, only evaluating the hash function several hundred times. By sacrificing a bit of computation (i.e., around one hour on a commodity M1 Pro processor with a five megahash/s rate), the same concurrent attack can be executed with just 4 concurrent sessions in total for the basic version and 2 concurrent sessions for the optimized version. For the above considerations, we still assume a pre-quantum attacker.
It is evident that CSI-Otter is not concurrently secure for the proposed parameters and design. Increasing the parameter k does not solve the problem since increasing it x times also increases the communication and signature size x times, which might blow up the signature’s size to Gigabytes to allow only \(2^{20}\) signatures, making the scheme impractical. In Table 2, we provide an optimistic estimation for the scheme’s efficiency after applying the proposed treatments. As argued in the introduction, CSI-Otter and, more generally, blind signatures from \(\varSigma \)-protocols with small challenge space should not be used concurrently without applying transformations to boost their security. Therefore, CSI-Otter can only be used as a blind signature scheme in the sequential setting.
The authors introduced the optimized variant with a challenge space of size 4 and \(k = 64\) repetitions to reduce the signature size by two at the expense of the size of the secret key and communication from the signer. Further improvements with an even bigger space and smaller repetitions should be possible. Unfortunately, our attacks show that this decreases the scheme’s security, allowing the adversary to forge signatures with fewer concurrent sessions and making a sequential attack more feasible. In particular, for the above case, an adversary only needs to compute \(2 \cdot 4 \cdot 2^{32} = 2^{35}\) (in expectation) to forge a fresh signature with just one signing query. For the basic version of CSI-Otter, this is \(2 \cdot 2 \cdot 2^{64} = 2^{66}\). The provided parameters should ensure 128-bit security, and they do if the scheme were a standard digital signature scheme. However, our attack shows that to achieve n-bit security for the blind signature scheme, we must set \(k = 2 \cdot n\). Thus, the repetitions must be more than 256 for 128-bit security in both cases, making the optimized variant no longer beneficial. The number of 256 repetitions must be further increased if we want to consider the post-quantum setting where we can apply Grover’s algorithm mentioned in the above section discussing sequential security.
6 Conclusion
We described three attacks against a class of three-move blind signature schemes based on \(\varSigma \)-protocol with small challenge space and parallel repetition. Unlike the ROS attack, the proposed attacks do not require any particular algebraic structure. This property is essential, as the lack of algebraic structure provides ambiguous arguments when assessing the concurrent security of the blind signature scheme. Moreover, because our attacks are generic and only rely on hash evaluation, there is a need for more rigorous treatment for the security parameter, especially when considered in the quantum setting.
We described an example case study of the CSI-Otter isogeny-based scheme and show that our mix-and-match attacks apply to this scheme. However, we highlighted that the class of aforementioned blind signature schemes is not restricted to this scheme and applies to other existing lattice-based or RSA-based constructions. CSI-Otter requires a more rigorous treatment of parameters to achieve practical sequential security. In contrast, one must apply boosting transformations for concurrent security, significantly worsening the scheme’s performance, communication, and signature size, making it less attractive than other post-quantum secure candidates (e.g., scheme from lattice assumptions).
We conclude by observing that, in the isogeny-based setting, \(\varSigma \)-protocols with exponentially large challenge space exist, e.g., SQISign [13]. It is unclear, however, whether it is possible to turn those \(\varSigma \)-protocols into a blind signature or not. We leave this question to potential future work.
Notes
- 1.
This can be done because of the honest verifier zero-knowledge property of the sigma protocol.
- 2.
Define \(x = |\mathcal {C}_{\varSigma }|\), the probability of fail after Q queries is equal to \(((x-1)/x)^Q\). This probability is negligible for \(Q = O(x)\), with constant \(128\log 2\).
- 3.
Modulo isomorphism over \(\mathbb {F}_p\).
- 4.
We also require that an element \(\pi \in \mathcal {O}\) maps to the Frobenius endomorphism trough that isomorphism.
- 5.
This is in fact supersingular for primes \(p \equiv 3 \pmod {4}\).
References
Abe, M., Okamoto, T.: Provably secure partially blind signatures. In: Bellare, M. (ed.) CRYPTO 2000. LNCS, vol. 1880, pp. 271–286. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-44598-6_17
Alamati, N., De Feo, L., Montgomery, H., Patranabis, S.: Cryptographic group actions and applications. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part II. LNCS, vol. 12492, pp. 411–439. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-64834-3_14
Bellare, M., Namprempre, C., Pointcheval, D., Semanko, M.: The one-more-RSA-inversion problems and the security of Chaum’s blind signature scheme. J. Cryptol. 16(3), 185–215 (2003). https://doi.org/10.1007/s00145-002-0120-1
Benhamouda, F., Lepoint, T., Loss, J., Orrù, M., Raykova, M.: On the (in)security of ROS. In: Canteaut, A., Standaert, F.X. (eds.) EUROCRYPT 2021, Part I. LNCS, vol. 12696, pp. 33–53. Springer, Heidelberg (2021). https://doi.org/10.1007/978-3-030-77870-5_2
Beullens, W., Katsumata, S., Pintore, F.: Calamari and Falafl: logarithmic (linkable) ring signatures from isogenies and lattices. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part II. LNCS, vol. 12492, pp. 464–492. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-64834-3_16
Beullens, W., Kleinjung, T., Vercauteren, F.: CSI-FiSh: efficient isogeny based signatures through class group computations. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019, Part I. LNCS, vol. 11921, pp. 227–247. Springer, Heidelberg (2019). https://doi.org/10.1007/978-3-030-34578-5_9
Boldyreva, A.: Threshold signatures, multisignatures and blind signatures based on the gap-Diffie-Hellman-group signature scheme. In: Desmedt, Y. (ed.) PKC 2003. LNCS, vol. 2567, pp. 31–46. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-36288-6_3
Castryck, W., Lange, T., Martindale, C., Panny, L., Renes, J.: CSIDH: an efficient post-quantum commutative group action. In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018, Part III. LNCS, vol. 11274, pp. 395–427. Springer, Heidelberg (2018). https://doi.org/10.1007/978-3-030-03332-3_15
Chairattana-Apirom, R., Hanzlik, L., Loss, J., Lysyanskaya, A., Wagner, B.: PI-cut-choo and friends: Compact blind signatures via parallel instance cut-and-choose and more. In: Dodis, Y., Shrimpton, T. (eds.) CRYPTO 2022, Part III. LNCS, vol. 13509, pp. 3–31. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-15982-4_1
Chaum, D.: Blind signatures for untraceable payments. In: Chaum, D., Rivest, R.L., Sherman, A.T. (eds.) CRYPTO 1982, pp. 199–203. Plenum Press, New York (1982)
Chaum, D., Pedersen, T.P.: Wallet databases with observers. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 89–105. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_7
De Feo, L., Galbraith, S.D.: SeaSign: compact isogeny signatures from class group actions. In: Ishai, Y., Rijmen, V. (eds.) EUROCRYPT 2019, Part III. LNCS, vol. 11478, pp. 759–789. Springer, Heidelberg (2019). https://doi.org/10.1007/978-3-030-17659-4_26
De Feo, L., Kohel, D., Leroux, A., Petit, C., Wesolowski, B.: SQISign: compact post-quantum signatures from quaternions and isogenies. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part I. LNCS, vol. 12491, pp. 64–93. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-64837-4_3
Ducas, L., van Woerden, W.P.J.: On the lattice isomorphism problem, quadratic forms, remarkable lattices, and cryptography. In: Dunkelman, O., Dziembowski, S. (eds.) EUROCRYPT 2022, Part III. LNCS, vol. 13277, pp. 643–673. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-07082-2_23
Duman, J., Hartmann, D., Kiltz, E., Kunzweiler, S., Lehmann, J., Riepel, D.: Generic models for group actions. In: Boldyreva, A., Kolesnikov, V. (eds.) PKC 2023, Part I. LNCS, vol. 13940, pp. 406–435. Springer, Heidelberg (2023). https://doi.org/10.1007/978-3-031-31368-4_15
Fiat, A., Shamir, A.: How to prove yourself: practical solutions to identification and signature problems. In: Odlyzko, A.M. (ed.) CRYPTO 1986. LNCS, vol. 263, pp. 186–194. Springer, Heidelberg (1987).https://doi.org/10.1007/3-540-47721-7_12
Fuchsbauer, G., Plouviez, A., Seurin, Y.: Blind Schnorr signatures and signed ElGamal encryption in the algebraic group model. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020, Part II. LNCS, vol. 12106, pp. 63–95. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-45724-2_3
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: 28th ACM STOC, pp. 212–219. ACM Press (1996). https://doi.org/10.1145/237814.237866
Hauck, E., Kiltz, E., Loss, J.: A modular treatment of blind signatures from identification schemes. In: Ishai, Y., Rijmen, V. (eds.) EUROCRYPT 2019, Part III. LNCS, vol. 11478, pp. 345–375. Springer, Heidelberg (2019).https://doi.org/10.1007/978-3-030-17659-4_12
Hauck, E., Kiltz, E., Loss, J., Nguyen, N.K.: Lattice-based blind signatures, revisited. In: Micciancio, D., Ristenpart, T. (eds.) CRYPTO 2020, Part II. LNCS, vol. 12171, pp. 500–529. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-56880-1_18
Kastner, J., Loss, J., Xu, J.: The Abe-Okamoto partially blind signature scheme revisited. In: Agrawal, S., Lin, D. (eds.) ASIACRYPT 2022, Part IV. LNCS, vol. 13794, pp. 279–309. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-22972-5_10
Katsumata, S., Lai, Y.F., LeGrow, J.T., Qin, L.: Csi-otter: isogeny-based (partially) blind signatures from the class group action with a twist. In: Advances in Cryptology. CRYPTO 2023. Part III, pp. 729–761. Springer, Heidelberg (2023). https://doi.org/10.1007/978-3-031-38548-3_24
Katsumata, S., Lai, Y.F., Reichle, M.: Breaking parallel ROS: implication for isogeny and lattice-based blind signatures. Cryptology ePrint Archive, Paper 2023/1603 (2023). https://eprint.iacr.org/2023/1603
Katz, J., Loss, J., Rosenberg, M.: Boosting the security of blind signature schemes. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021, Part IV. LNCS, vol. 13093, pp. 468–492. Springer, Heidelberg (2021). https://doi.org/10.1007/978-3-030-92068-5_16
Ling, S., Nguyen, K., Stehlé, D., Wang, H.: Improved zero-knowledge proofs of knowledge for the ISIS problem, and applications. In: Kurosawa, K., Hanaoka, G. (eds.) PKC 2013. LNCS, vol. 7778, pp. 107–124. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-36362-7_8
Lyubashevsky, V., Nguyen, N.K., Plançon, M.: Efficient lattice-based blind signatures via gaussian one-time signatures. In: Hanaoka, G., Shikata, J., Watanabe, Y. (eds.) PKC 2022, Part II. LNCS, vol. 13178, pp. 498–527. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-030-97131-1_17
Orsini, E., Zanotto, R.: Simple two-round OT in the explicit isogeny model. Cryptology ePrint Archive, Paper 2023/269 (2023). https://eprint.iacr.org/2023/269
Pointcheval, D.: Strengthened security for blind signatures. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 391–405. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054141
Pointcheval, D., Stern, J.: Security arguments for digital signatures and blind signatures. J. Cryptol. 13(3), 361–396 (2000). https://doi.org/10.1007/s001450010003
Ramos-Calderer, S., Bellini, E., Latorre, J.I., Manzano, M., Mateu, V.: Quantum search for scaled hash function preimages. Quantum Inf. Process. 20(5), 180 (2021). https://doi.org/10.1007/s11128-021-03118-9
Silverman, J.H.: The Arithmetic of Elliptic Curves, Graduate Texts in Mathematics, vol. 106. Springer, New York (1986)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 International Association for Cryptologic Research
About this paper
Cite this paper
Do, K., Hanzlik, L., Paracucchi, E. (2024). M&M’S: Mix and Match Attacks on Schnorr-Type Blind Signatures with Repetition. In: Joye, M., Leander, G. (eds) Advances in Cryptology – EUROCRYPT 2024. EUROCRYPT 2024. Lecture Notes in Computer Science, vol 14656. Springer, Cham. https://doi.org/10.1007/978-3-031-58751-1_13
Download citation
DOI: https://doi.org/10.1007/978-3-031-58751-1_13
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-58750-4
Online ISBN: 978-3-031-58751-1
eBook Packages: Computer ScienceComputer Science (R0)


 : on input a secret key
: on input a secret key 
 : on input a secret key
: on input a secret key  : on input a public key
: on input a public key 
 . Initialize
. Initialize  . Then it returns the response
. Then it returns the response  and returns s to
and returns s to 



 , a pair
, a pair
 and outputs a public key
and outputs a public key  and sets
and sets  and sets
and sets  , and computes
, and computes 