Abstract
Java deserialization vulnerabilities arise when unexpected data triggers dangerous function calls during deserialization processes. Current deserialization vulnerability detection faces challenges such as path explosion caused by polymorphism [29] in Java, leading to incomplete analysis and inefficiency.
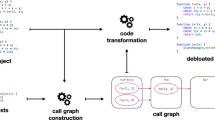
In this paper, we present SerdeSniffer, a new Java deserialization vulnerability detection tool to address these challenges. SerdeSniffer is the first tool that employs a bottom-up function summarization technique to mitigate path explosion effectively. Specifically, SerdeSniffer uses function summaries during interprocedural analysis to effectively prevent multiple calculations in taint analysis and utilizes fixpoint computation to analyze issues related to function recursion and cyclic calls.
To avoid omissions in summary information, we use the over-tainting method in taint analysis and treat uninitialized variables as taint sources. We also merge the summary information of called functions to facilitate polymorphic analysis. Furthermore, SerdeSniffer includes a vulnerability detection algorithm that starts from dangerous functions and uses summary information and propagation rules in a bottom-up approach, and employs a sanitizer to eliminate ineffective propagation paths.
In comparative experiments based on ysoserial [23], a tool for generating payloads that exploit Java object deserialization, SerdeSniffer identified nine more historical gadget chains than other open source tools. In testing the latest versions of components, SerdeSniffer discovered three new gadget chains within 600 s, the longest being 14 nodes, two of these new chains confirmed by CVEs in the PUBLISHED state.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
alibaba/fastjson. https://github.com/alibaba/fastjson
Collections - home. https://commons.apache.org/proper/commons-collections/
CVE-2017-20189. https://nvd.nist.gov/vuln/detail/CVE-2017-20189
CVE-2024-22871. https://nvd.nist.gov/vuln/detail/CVE-2024-22871
Gadget chains in zaproxy. https://bugcrowd.com/submissions/33b61ea8-30cd-40b2-81c8-30b5dff979d0
GCMiner/GCMiner: Artifact for ICSE 2023. https://github.com/GCMiner/GCMiner
Issues \(\cdot \) GCMiner/GCMiner. https://github.com/GCMiner/GCMiner
neo4j/neo4j: Graphs for everyone. https://github.com/neo4j/neo4j
ODDFuzz/ODDFuzz. https://github.com/ODDFuzz/ODDFuzz
SerdeSniffer/SerdeSniffer. https://github.com/SerdeSniffer/SerdeSniffer
Snyk vulnerability database | snyk. https://security.snyk.io/
unshorn/serhybridpub. https://bitbucket.org/unshorn/serhybridpub/src/master/
Weblogic server|oracle. https://www.oracle.com/java/weblogic/
wh1t3p1g/tabby: Code analysis tool. https://github.com/wh1t3p1g/tabby
Allard, A., Albinsson, B., Wadell, G.: Rapid typing of human adenoviruses by a general PCR combined with restriction endonuclease analysis. J. Clin. Microbiol. 39(2), 498–505 (2001)
Antoniadis, T., et al.: Porting doop to soufflé: a tale of inter-engine portability for datalog-based analyses. In: Proceedings of the 6th ACM SIGPLAN Int. Workshop on SOAP, pp. 25–30. ACM (2017). https://doi.org/10.1145/3088515.3088522
Bravenboer, M., et al.: Strictly declarative specification of sophisticated points-to analyses. In: OOPSLA09, pp. 243–262. ACM (2009)
Cao, S., et al.: Improving java deserialization gadget chain mining via overriding-guided object generation. In: 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE), pp. 397–409. IEEE (2023)
Cao, S., et al.: ODDFuzz: Discovering java deserialization vulnerabilities via structure-aware directed greybox fuzzing. In: 2023 IEEE Symposium on Security and Privacy (SP), pp. 2726–2743. IEEE (2023)
Chen, B., et al.: Efficient detection of java deserialization gadget chains via bottom-up gadget search and dataflow-aided payload construction. In: 2024 IEEE Symposium on Security and Privacy (SP), pp. 150–150. IEEE Computer Society (2024)
Chen, X., et al.: Tabby: automated gadget chain detection for java deserialization vulnerabilities. In: 2023 53rd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), pp. 179–192. IEEE (2023)
Dean, J., Grove, D., Chambers, C.: Optimization of object-oriented programs using static class hierarchy analysis. In: Tokoro, M., Pareschi, R. (eds.) ECOOP 1995. LNCS, vol. 952, pp. 77–101. Springer, Heidelberg (1995). https://doi.org/10.1007/3-540-49538-X_5
Frohoff, C.: ysoserial (2015). https://github.com/frohoff/ysoserial
Grech, N., Smaragdakis, Y.: P/Taint: unified points-to and taint analysis. Proc. ACM Program. Lang. 1(OOPSLA), 1–28 (2017)
Haken, I.: Gadget inspector. https://github.com/JackOfMostTrades/gadgetinspector
Hasti, R., et al.: Using static single assignment form to improve flow-insensitive pointer analysis. In: Proceedings of the ACM SIGPLAN 1998 Conference on Programming Language Design and Implementation. PLDI ’98, New York, NY, USA, pp. 97–105. Association for Computing Machinery (1998)
Jordan, H., Scholz, B., Subotić, P.: Soufflé: on synthesis of program analyzers. In: Chaudhuri, S., Farzan, A. (eds.) CAV 2016, Part II. LNCS, vol. 9780, pp. 422–430. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-41540-6_23
Lam, P., et al.: The soot framework for java program analysis: a retrospective. In: Cetus Users and Compiler Infastructure Workshop (CETUS 2011), vol. 15 (2011)
Milojkovic, N., et al.: Polymorphism in the spotlight: studying its prevalence in java and smalltalk. In: 2015 IEEE 23rd International Conference on Program Comprehension, pp. 186–195 (2015). https://doi.org/10.1109/ICPC.2015.29
Needham, M., Hodler, A.E.: Graph algorithms: practical examples in Apache Spark and Neo4j. O’Reilly Media (2019)
Pacheco, C., Ernst, M.D.: Randoop: feedback-directed random testing for java. In: Companion to the 22nd ACM SIGPLAN conference on object-oriented programming systems and applications Companion, pp. 815–816 (2007)
Padhye, R., et al.: JQF: coverage-guided property-based testing in java. In: Proceedings of the 28th ACM SIGSOFT International Symposium on Software Testing and Analysis, pp. 398–401. ACM (2019). https://doi.org/10.1145/3293882.3339002
Rasheed, S., et al.: A hybrid analysis to detect java serialisation vulnerabilities. In: Proceedings of the 35th IEEE/ACM International Conference on Automated Software Engineering. ASE ’20, pp. 1209–1213. Association for Computing Machinery (2021)
Scholz, B., Jordan, H., Subotić, P., Westmann, T.: On fast large-scale program analysis in datalog. In: Proceedings of the 25th International Conference on Compiler Construction, pp. 196–206 (2016)
Acknowledgement
This work was supported by National Key Research and Development Program of China (No.2023YFB3106400, 2023QY1202), the National Natural Science Foundation of China (U2336203, U1836210), the Key Research and Development Science and Technology of Hainan Province (GHYF2022010), and Beijing Natural Science Foundation (4242031).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Appendix
A Appendix
The content of this appendix is the Clojure command execution gadget chain.
1.1 A.1 Clojure Command Execution
The new deserialization vulnerability in Clojure, affecting versions 1.9 to 1.12-alpha5, presents distinct characteristics compared to historical vulnerabilities. To address vulnerabilities, version 1.9 introduced patches that blocked the serialization of specific classes including AbstractTableModel$ff19274a. Despite these efforts, this version also inadvertently made clojure.lang.Var serializable, thereby opening up new avenues for potential exploitation.
SerdeSniffer discovered a new exploitation chain that bypasses these patch restrictions. As shown in Fig. 9, the deserialization of HashMap triggers the hashCode function in the PersistentQueue class. This sequence continues into the first function of PersistentQueue$Seq, which allows for the serialization and manipulation of its Iterate objects. These serialized objects facilitate function calls that use the serialized f and prevSeed fields, ultimately leading to command execution via the invoke function of core$partial$fn__5920 in process$start.
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Liu, X., Wang, H., Xu, M., Zhang, Y. (2024). SerdeSniffer: Enhancing Java Deserialization Vulnerability Detection with Function Summaries. In: Garcia-Alfaro, J., Kozik, R., Choraś, M., Katsikas, S. (eds) Computer Security – ESORICS 2024. ESORICS 2024. Lecture Notes in Computer Science, vol 14984. Springer, Cham. https://doi.org/10.1007/978-3-031-70896-1_9
Download citation
DOI: https://doi.org/10.1007/978-3-031-70896-1_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-70895-4
Online ISBN: 978-3-031-70896-1
eBook Packages: Computer ScienceComputer Science (R0)