Abstract
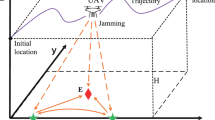
The flexibility and cost-effectiveness of unmanned aerial vehicles (UAVs) in a wide range of scenarios have made them indispensable tools for mobile communications. However, UAV communications are also facing increasing security threats, especially in open spaces where they are vulnerable to potential eavesdroppers. In this paper, we employ an extra UAV as a cooperative jammer to enhance UAV-to-ground communication security by sending artificial noise to effectively resist passive eavesdroppers. Unlike previous work, we focus on the dynamic scenario where the source UAV and the ground user move simultaneously. In this scenario, we propose a joint optimization algorithm of trajectory and power for the jamming UAV to obtain the optimal jamming strategy. Due to the absence of eavesdroppers’ locations, the goal of the optimization is to maximize a secure region. Numerical results demonstrate that our optimization algorithm can significantly enlarge the secure region compared to randomly selecting a position of the jamming UAV.
Supported in part by the National Key R&D Program of China under Grant 2022YFB3104503; in part by the National Natural Science Foundation of China under Grant 62202054, and Grant 62002022.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Al-Hourani, A., Kandeepan, S., Lardner, S.: Optimal lap altitude for maximum coverage. IEEE Wirel. Commun. Lett. 3(6), 569–572 (2014). https://doi.org/10.1109/LWC.2014.2342736
Alzenad, M., El-Keyi, A., Yanikomeroglu, H.: 3-D placement of an unmanned aerial vehicle base station for maximum coverage of users with different QoS requirements. IEEE Wirel. Commun. Lett. 7(1), 38–41 (2017)
Bayat, S., Louie, R.H., Han, Z., Vucetic, B., Li, Y.: Physical-layer security in distributed wireless networks using matching theory. IEEE Trans. Inf. Forensics Secur. 8(5), 717–732 (2013)
Boyd, S.P., Vandenberghe, L.: Convex Optimization. Cambridge University Press, Cambridge (2004)
Ding, X., Song, T., Zou, Y., Chen, X.: Security-reliability tradeoff for friendly jammer assisted user-pair selection in the face of multiple eavesdroppers. IEEE Access 4, 8386–8393 (2016)
Fan, J., Huo, Y., Fan, X., Hu, C., Jing, G.: A cooperative jamming based secure uplink transmission scheme for heterogeneous networks supporting D2D communications. In: Chellappan, S., Cheng, W., Li, W. (eds.) WASA 2018. LNCS, vol. 10874, pp. 103–114. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-94268-1_9
Fan, X., Huang, L., Huo, Y., Hu, C., Tian, Y., Qian, J.: Space power synthesis-based cooperative jamming for unknown channel state information. In: Ma, L., Khreishah, A., Zhang, Y., Yan, M. (eds.) WASA 2017. LNCS, vol. 10251, pp. 483–495. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-60033-8_42
Fan, X., Huo, Y.: Security analysis of cooperative jamming in internet of things with multiple eavesdroppers. In: 2019 IEEE Global Communications Conference (GLOBECOM), pp. 1–6. IEEE (2019)
Fan, X., Huo, Y.: Cooperative secure transmission against collusive eavesdroppers in internet of things. Int. J. Distrib. Sens. Netw. 16(6), 1550147720933464 (2020)
Fan, X., Wang, Y., Li, G., Huo, Y., Tian, Z.: Hybrid uplink-downlink Noma for secure coordinated multi-point networks. In: 2021 IEEE International Conference on Communications Workshops (ICC Workshops), pp. 1–6 (2021). https://doi.org/10.1109/ICCWorkshops50388.2021.9473623
Grant, M.: CVX: Matlab software for disciplined convex programming, version 1.21 (2011). http://cvxr.com/cvx
Huang, L., Fan, X., Huo, Y., Hu, C., Tian, Y., Qian, J.: A novel cooperative jamming scheme for wireless social networks without known CSI. IEEE Access 5, 26476–26486 (2017)
Huo, Y., Fan, X., Ma, L., Cheng, X., Tian, Z., Chen, D.: Secure communications in tiered 5G wireless networks with cooperative jamming. IEEE Trans. Wireless Commun. 18(6), 3265–3280 (2019)
Huo, Y., Xu, M., Fan, X., Jing, T.: A novel secure relay selection strategy for energy-harvesting-enabled internet of things. EURASIP J. Wirel. Commun. Netw. 2018(1), 264 (2018)
Kong, P.Y.: A survey of cyberattack countermeasures for unmanned aerial vehicles. IEEE Access 9, 148244–148263 (2021). https://doi.org/10.1109/ACCESS.2021.3124996
Liu, C., Quek, T.Q., Lee, J.: Secure UAV communication in the presence of active eavesdropper. In: 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), pp. 1–6. IEEE (2017)
Ramirez, C., Kreinovich, V., Argaez, M.: Why 1 is a good approximation to 0: a geometric explanation (2013)
Razaviyayn, M.: Successive convex approximation: analysis and applications. Ph.D. thesis, University of Minnesota (2014)
Tran, H., So-In, C., et al.: Enhanced intrusion detection system for an eh IoT architecture using a cooperative UAV relay and friendly UAV jammer. IEEE/CAA J. Automatica Sinica 8(11), 1786–1799 (2021)
Vilela, J.P., Bloch, M., Barros, J., McLaughlin, S.W.: Wireless secrecy regions with friendly jamming. IEEE Trans. Inf. Forensics Secur. 6(2), 256–266 (2011). https://doi.org/10.1109/TIFS.2011.2111370
Wei, L., Jing, T., Fan, X., Wen, Y., Huo, Y.: The secrecy analysis over physical layer in noma-enabled cognitive radio networks. In: 2018 IEEE International Conference on Communications (ICC), pp. 1–6. IEEE (2018)
Xu, M., Jing, T., Fan, X., Wen, Y., Huo, Y.: Secure transmission solutions in energy harvesting enabled cooperative cognitive radio networks. In: 2018 IEEE Wireless Communications and Networking Conference (WCNC), pp. 1–6. IEEE (2018)
Yan, S., Yang, N., Land, I., Malaney, R., Yuan, J.: Three artificial-noise-aided secure transmission schemes in wiretap channels. IEEE Trans. Veh. Technol. 67(4), 3669–3673 (2017)
Zeng, Y., Zhang, R., Lim, T.J.: Wireless communications with unmanned aerial vehicles: opportunities and challenges. IEEE Commun. Mag. 54(5), 36–42 (2016). https://doi.org/10.1109/MCOM.2016.7470933
Zhang, H., Sun, J., Wang, X., Gong, C.: Achieving physical layer security against location unknown eavesdroppers via friendly jammer. IEEE/CAA J. Automatica Sinica 10(10), 2038–2040 (2023). https://doi.org/10.1109/JAS.2023.123258
Zhang, P., Jiang, Y., Lin, C., Fan, Y., Shen, X.: P-coding: secure network coding against eavesdropping attacks. In: 2010 Proceedings IEEE INFOCOM, pp. 1–9 (2010). https://doi.org/10.1109/INFCOM.2010.5462050
Zhou, Y.: Improving physical layer security via a UAV friendly jammer for unknown eavesdropper location. IEEE Trans. Veh. Technol. 67(11), 11280–11284 (2018). https://doi.org/10.1109/TVT.2018.2868944
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2025 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Yu, W. et al. (2025). 3D Physical Layer Secure Transmission for UAV-Assisted Mobile Communications Without Locations of Eavesdroppers. In: Cai, Z., Takabi, D., Guo, S., Zou, Y. (eds) Wireless Artificial Intelligent Computing Systems and Applications. WASA 2024. Lecture Notes in Computer Science, vol 14998. Springer, Cham. https://doi.org/10.1007/978-3-031-71467-2_29
Download citation
DOI: https://doi.org/10.1007/978-3-031-71467-2_29
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-71466-5
Online ISBN: 978-3-031-71467-2
eBook Packages: Computer ScienceComputer Science (R0)