Abstract
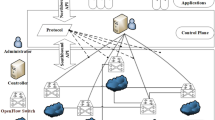
In order to solve the security threat caused by malicious nodes in the Internet of Things transmission link to the data flow and transmission process, a Software Defined Network (SDN) based detection and location method of malicious nodes in the Internet of Things is proposed. The software defined network architecture is applied to the transmission process of data flow between edge nodes. The incoming switch node adds a forwarding verification header to the incoming data packet according to the forwarding path. Each downstream switch node verifies and forwards the data packet based on the header to ensure the integrity of the data packet and the consistency of the forwarding path, and sends the abnormal data packet that fails to pass the verification to the controller. The controller locates the malicious exchange node in the link through the header information. Finally, the proposed method is simulated and evaluated, and the experimental results show that the scheme is effective.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Xiao, Y., Jia, Y., Liu, C., et al.: Edge computing security: state of the art and challenges. Proc. IEEE 107(8), 1608–1631 (2019)
Alwakeel, A.M.: An overview of fog computing and edge computing security and privacy issues. Sensors 21(24), 8226 (2021)
Ranaweera, P., Jurcut, A.D., Liyanage, M.: Survey on multi-access edge computing security and privacy. IEEE Commun. Surv. Tutorials 23(2), 1078–1124 (2021)
Kang, J. J., Fahd, K., Venkatraman, S., Trujillo-Rasua, R., Haskell-Dowland, P.: Hybrid routing for Man-in-the-Middle (MITM) attack detection in IoT networks. In 2019 29th International Telecommunication Networks and Applications Conference (ITNAC), pp. 1–6. IEEE (November 2019)
Mckeown, N.: Software-defined networking. In: IEEE International Conference on Computer Communications, pp. 30–32 (2009)
Javanmardi, S., Shojafar, M., Mohammadi, R., et al.: An SDN perspective IoT-Fog security: a survey. Comput. Netw. 229, 109732 (2023)
Kiran, N., Pan, C., Wang, S., et al.: Joint resource allocation and computation offloading in mobile edge computing for SDN based wireless networks. J. Commun. Netw. 22(1), 1–11 (2019)
Lu, J., Luan, W., Liu, R., et al.: Architecture of distribution internet of things based on widespread sensing & software defined technology. Grid Technol. 42(10), 3108–3115 (2018)
Gao, J., Agyekum, K.O.B.O., Sifah, E.B., et al.: A blockchain-SDN-enabled Internet of vehicles environment for fog computing and 5G networks. IEEE Internet Things J. 7(5), 4278–4291 (2019)
Bosshart, P., Daly, D., Gibb, G., et al.: P4: programming protocol-independent packet processors. ACM SIGCOMM Comput. Commun. Rev. 44(3), 87–95 (2014)
Sadiq, K.A., Thompson, A.F., Ayeni, O.A.: Mitigating DDoS Attacks in Cloud Network using Fog and SDN: A Conceptual Security Framework
Nguyen, T.G., Phan, T.V., Nguyen, B.T., So-In, C., Baig, Z.A., Sanguanpong, S.: Search: a collaborative and intelligent nids architecture for sdn-based cloud iot networks. IEEE Access 7, 107678–107694 (2019)
Khan, M.T., Akhunzada, A., Zeadally, S.: Proactive defense for fog-to-things critical infrastructure. IEEE Commun. Mag. 60(12), 44–49 (2022)
Gao, J., et al.: A blockchain-SDN-enabled internet of vehicles environment for fog computing and 5G networks. IEEE Internet Things J. 7(5), 4278–4291 (2019)
Xie, L., Ding, Y., Yang, H., Wang, X.: Blockchain-based secure and trustwor-thy internet of things in SDN-enabled 5G-VANETs. IEEE Access 7, 56656–56666 (2019)
Oh, J., et al.: A secure data sharing based on key aggregate searchable encryption in fog-enabled IoT environment. IEEE Trans. Netw. Sci. Eng. 9(6), 4468–4481 (2022)
Torres-Charles, C.A., Carrizales-Espinoza, D.E., Sanchez-Gallegos, D.D., et al.: SecMesh: an efficient information security method for stream processing in edge-fog-cloud. In: Proceedings of the 2022 7th International Conference on Cloud Computing and Internet of Things, pp. 8–16 (2022)
Mohan, K.V.M., Kodati, S., Krishna, V.: Securing SDN enabled IoT scenario infrastructure of fog networks from attacks. In: 2022 Second International Conference on Artificial Intelligence and Smart Energy, ICAIS, pp. 1239–1243. IEEE (2022)
Zhang, P., Xu, S., Yang, Z., et al.: FOCES: detecting forwarding anomalies in software defined networks. In: 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), pp. 830–840. IEEE (2018)
Hessam, G., Saba, G., Alkhayat, M.I.: A new approach for detecting violation of data plane integrity in software defined networks. J. Comput. Secur. 29(3), 341–358 (2021)
Kim, T.H.J., Basescu, C., Jia, L., et al.: Lightweight source authentication and path validation. In: Proceedings of the 2014 ACM Conference on SIGCOMM, pp. 271–282 (2014)
Sasaki, T., Pappas, C., Lee, T., et al.: SDNsec: forwarding accountability for the SDN data plane. In: 2016 25th International Conference on Computer Communication and Networks (ICCCN), pp. 1–10. IEEE (2016)
Zuo, Z., Chang, C., Zhang, Y., et al.: P4Label: packet forwarding control mechanism based on P4 for software-defined networking. J. Ambient Intell. Humanized Comput., 1–14 (2020)
Wu, P., Chang, C., Zuo, Z., et al.: SDN packet forwarding verification based on address overloading. J. Commun. 43(3), 88–100 (2022)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2025 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Jingxu, X., Chaowen, C., Lu, Y., Yingying, M., Chenli, Y. (2025). Detection and Localization of Malicious Nodes in Internet of Things Based on SDN. In: Cai, Z., Takabi, D., Guo, S., Zou, Y. (eds) Wireless Artificial Intelligent Computing Systems and Applications. WASA 2024. Lecture Notes in Computer Science, vol 14998. Springer, Cham. https://doi.org/10.1007/978-3-031-71467-2_37
Download citation
DOI: https://doi.org/10.1007/978-3-031-71467-2_37
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-71466-5
Online ISBN: 978-3-031-71467-2
eBook Packages: Computer ScienceComputer Science (R0)