Abstract
Useful security properties arise from sealing data to specific units of code. Modern processors featuring Intel’s TXT and AMD’s SVM achieve this by a process of measured and protected execution. Only code which has the correct measurement can access the data, and this code runs in an environment protected from observation and interference. We present a modelling language with primitives for protected execution, along with its semantics. We characterise an attacker who has access to all the capabilities of the hardware. In order to achieve automatic analysis of systems using protected execution without attempting to search an infinite state space, we define transformations that reduce the number of times the attacker needs to use protected execution to a pre-determined bound. Given reasonable assumptions we prove the soundness of the transformation: no secrecy attacks are lost by applying it. We then describe using the StatVerif extensions to ProVerif to model the bounded invocations of protected execution. We show the analysis of realistic systems, for which we provide case studies.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Trusted eXecution Modelling Language.
References
Advanced Micro Devices: Secure Virtual Machine Architecture Reference Manual. Advanced Micro Devices (2005)
Arapinis, M., Ritter, E., Ryan, M.D.: Statverif: verification of stateful processes. In: Proceedings of the 24th IEEE Computer Security Foundations Symposium, pp. 33–47. IEEE Computer Society Press (2011)
Coker, G., Guttman, J., Loscocco, P., Herzog, A., Millen, J., O’Hanlon, B., Ramsdell, J., Segall, A., Sheehy, J., Sniffen, B.: Principles of remote attestation. Int. J. Inf. Secur. 10(2), 63–81 (2011)
Datta, A., Franklin, J., Garg, D., Kaynar, D.: A logic of secure systems and its application to trusted computing. In: Proceedings of the 30th IEEE Symposium on Security and Privacy, pp. 221–236. IEEE Computer Society Press (2009)
Delaune, S., Kremer, S., Ryan, M.D., Steel, G.: A formal analysis of authentication in the TPM. In: Degano, P., Etalle, S., Guttman, J. (eds.) FAST 2010. LNCS, vol. 6561, pp. 111–125. Springer, Heidelberg (2011)
Delaune, S., Kremer, S., Ryan, M., Steel, G.: Formal analysis of protocols based on TPM state registers. In: Proceedings of the 24th IEEE Computer Security Foundations Symposium. IEEE Computer Society Press (2011)
Fournet, C., Planul, J.: Compiling information-flow security to minimal trusted computing bases. In: Barthe, G. (ed.) ESOP 2011. LNCS, vol. 6602, pp. 216–235. Springer, Heidelberg (2011)
Grawrock, D.: Dynamics of a Trusted Platform: A Building Block Approach. Intel Press, Hillsboro (2009)
Gürgens, S., Rudolph, C., Scheuermann, D., Atts, M., Plaga, R.: Security evaluation of scenarios based on the TCG’s TPM specification. In: Biskup, J., López, J. (eds.) ESORICS 2007. LNCS, vol. 4734, pp. 438–453. Springer, Heidelberg (2007)
Lin, A.: Automated analysis of security APIs. Ph.D. thesis, MIT (2005)
McCune, J., Parno, B., Perrig, A., Reiter, M., Isozaki, H.: Flicker: an execution infrastructure for TCB minimization. ACM SIGOPS Operating Syst. Rev. 42(4), 315–328 (2008)
Millen, J., Guttman, J., Ramsdell, J., Sheehy, J., Sniffen, B.: Analysis of a measured launch. http://www.mitre.org/work/tech_papers/tech_papers_07/07_0843/07_0843.pdf (2007). Accessed 7 Dec 2011
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Proof of Theorem 1
Proof of Theorem 1
Suppose \(K\) contains \(B_1\), \(B_2\), ..., \(B_n\). Let \(m\) be the number of sealed blobs in \(\overline{\mathsf{K }}\), as in Definition 1. Let \(S\) be a strategy such that  . Then:
. Then:
1 \(\exists S'\) such that  .
.
2 \(S'\) simulates \(S\); that is \(\exists q\) such that  .
.
3 \(S'\) uses only data present in \(S\), i.e. \(\text {names}(S') \subseteq \text {names}(S)\).
4 The number of \(\mathsf{SKINIT }\)s plus the number of \(\mathsf{reset }\)s in \(S'\) is at most \(m\).
We first prove a number of lemmas.
Lemma 1
 implies
implies  .
.
Proof
We show this by induction on \(S\).
Base case \(S = \emptyset \). The proof is obvious, setting \(p'' = p\).
Inductive case
\(S = C; S_1\). We have  . Take any \(p\).
. Take any \(p\).
Taking each case of C
\(\mathsf{skip }, x := f(), x:=g(), x:=\mathsf{seal }(u, v), \mathsf{check }\; u = v\) We have \(p' =\bot \), and  . Apply IH with \(p\) to obtain \(p''\), and we have
. Apply IH with \(p\) to obtain \(p''\), and we have  , i.e.
, i.e.  .
.
\(\mathsf{unseal }(v)\) This situation is impossible.
\(\mathsf{extend }(v)\)We have \(p' =\bot \) and  . Apply IH with \(h(p, v)\) to obtain \(p''\), and we then have
. Apply IH with \(h(p, v)\) to obtain \(p''\), and we then have  i.e.
i.e.  .
.
\(\mathsf{reset }, \mathsf{SKINIT } \{ P; \mathsf{rtn }\,u \}\) We have \(p'=1\) and  , and
, and  , i.e. set \(p'' = p'''\) and we have
, i.e. set \(p'' = p'''\) and we have  .
.
Lemma 2
 implies
implies  .
.
Proof
Consider each case of \(C\) in turn.
Lemma 3
 implies
implies  .
.
Proof
Consider each case of \(C\) in turn. For unseal, we prove the left disjunct. For all other cases, we prove the right disjunct.
Lemma 4
If \(p \ne \bot \) then  implies
implies  .
.
Proof
Consider each case of \(C\) in turn.
Lemma 5
 implies
implies  or
or  .
.
Proof
Consider each case of \(C\) in turn. For unseal, we prove the left disjunct. For all other cases, we prove the right disjunct.
Part 1 of Theorem 1
 implies
implies  .
.
Proof
We prove something more general:
 implies
implies  .
.
Base case \(S = \emptyset \) is obvious.
Inductive case \(S = C; S_1\)
Suppose  .
.
Expanding:  . By inductive hypothesis, \(\exists S_1' . \)
. By inductive hypothesis, \(\exists S_1' . \)
-
either
 . From
. From  , by Lemma 2, \(\exists C'\).
, by Lemma 2, \(\exists C'\). . So set \(S' = C'; S_1'\). Then
. So set \(S' = C'; S_1'\). Then  .
. -
or
 . From
. From  , by Lemma 3, either
, by Lemma 3, either  , so
, so  , or
, or 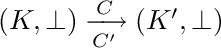 , so
, so  where again, \(S' = C'; S_1'\).
where again, \(S' = C'; S_1'\).
Part 2 of Theorem 1
 implies
implies  .
.
Proof
We prove something stronger:
 implies
implies  .
.
We prove this using induction on \(S\).
Base case \(S = \emptyset \) is obvious.
Inductive case
\(S = C; S_1\). Inductive hypothesis:  implies
implies  .
.
We want to prove  i.e.
i.e.  .
.
-
Either \(p' = \bot \)
-
either \(p = \bot \):
 , so by Lemma 4 and IH
, so by Lemma 4 and IH  , i.e.
, i.e.  .
. -
or \(p \ne \bot \):
 . by Lemma 5 and IH \(\exists p'' . \)
. by Lemma 5 and IH \(\exists p'' . \)
-
either
 , Then by Lemma 1,
, Then by Lemma 1,  , i.e.
, i.e. 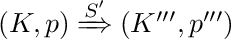 .
. -
or
 . Then by Lemma 1,
. Then by Lemma 1,  , i.e.
, i.e.  .
.
-
-
-
or \(p' \ne \bot \) then
 by Lemma 4, and so by IH
by Lemma 4, and so by IH  , i.e.
, i.e.  .
.
Part 3 of Theorem 1
\(S'\) uses only the data present in \(S\) that is, every name in \(S'\) is in \(S\).
Part 3 of the theorem is readily proved by inspection of the transformation.
Part 4 of Theorem 1
The number of \(\mathsf{SKINIT }\)s plus the number of \(\mathsf{reset }\)s in \(S'\) is at most \(m\).
Part 4 follows from the facts that:
-
at most \(m\) plaintext-distinct sealed blobs can be produced from the initial data;
-
the transformed strategy \(S'\) runs at most one SKINIT for each blob sealed to a PCR value rooted in 0 (other invocations are run as SUBRs);
-
the transformed strategy \(S'\) runs at most one reset for each sealed blob rooted in 1 (other resets are transformed into skips).
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Xu, S., Batten, I., Ryan, M. (2014). Dynamic Measurement and Protected Execution: Model and Analysis. In: Abadi, M., Lluch Lafuente, A. (eds) Trustworthy Global Computing. TGC 2013. Lecture Notes in Computer Science(), vol 8358. Springer, Cham. https://doi.org/10.1007/978-3-319-05119-2_4
Download citation
DOI: https://doi.org/10.1007/978-3-319-05119-2_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-05118-5
Online ISBN: 978-3-319-05119-2
eBook Packages: Computer ScienceComputer Science (R0)





 . From
. From  , by Lemma 2,
, by Lemma 2,  . So set
. So set  .
. . From
. From  , by Lemma 3, either
, by Lemma 3, either  , so
, so  , or
, or 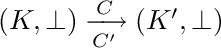 , so
, so  where again,
where again,  , so by Lemma 4 and IH
, so by Lemma 4 and IH  , i.e.
, i.e.  .
. . by Lemma 5 and IH
. by Lemma 5 and IH  , Then by Lemma 1,
, Then by Lemma 1,  , i.e.
, i.e. 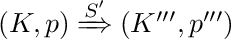 .
. . Then by Lemma 1,
. Then by Lemma 1,  , i.e.
, i.e.  .
. by Lemma 4, and so by IH
by Lemma 4, and so by IH  , i.e.
, i.e.  .
.